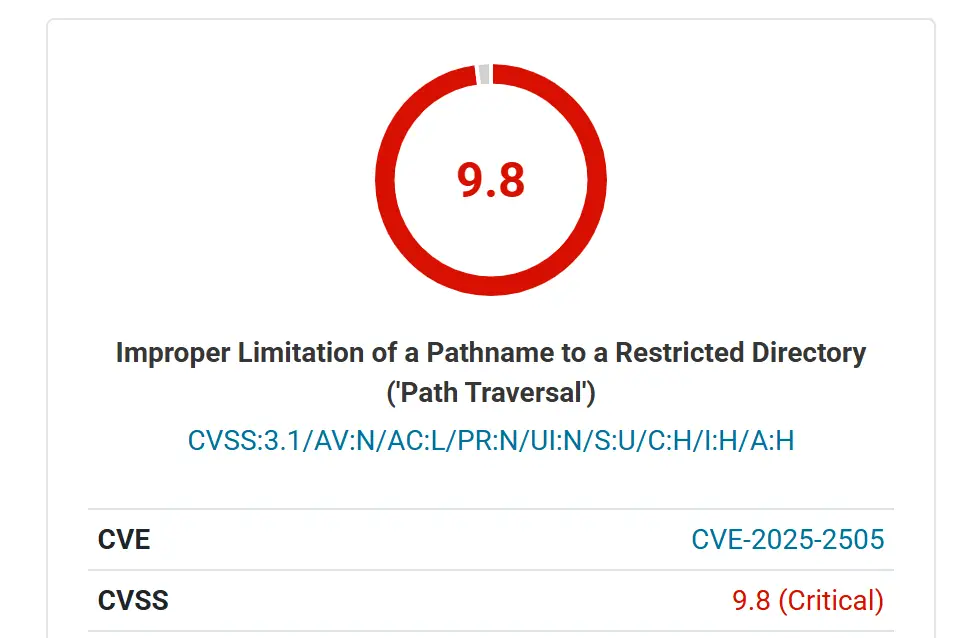
A critical security vulnerability has been discovered in the popular Age Gate plugin for WordPress, potentially exposing over 40,000 websites to unauthenticated remote code execution attacks. The flaw, tracked as CVE-2025-2505, has been assigned a CVSS severity score of 9.8.
The Age Gate plugin is widely used by WordPress site owners to restrict content based on user age, typically for compliance with regulations concerning age-restricted content. However, a Local PHP File Inclusion (LFI) vulnerability has been identified in all versions up to and including 3.5.3, making it possible for attackers to exploit the flaw through the ‘lang’ parameter.
This security flaw allows unauthenticated attackers to include and execute arbitrary PHP files on the server. This can result in:
- Bypassing access controls
- Extracting sensitive data
- Executing arbitrary code in cases where images or other permitted file types can be uploaded and included
The risk associated with this vulnerability is particularly severe, as it could lead to full server compromise. Attackers exploiting CVE-2025-2505 may:
- Execute malicious PHP scripts remotely
- Establish persistent backdoors for long-term control
- Exploit loopholes in web server configurations to escalate privileges
If an attacker can successfully upload a malicious PHP file disguised as an image or other allowed format, they can use the vulnerability to force its execution, leading to complete control over the affected website.
The developers of the Age Gate plugin have released a patched version (3.5.4) that resolves the security flaw. Website administrators and WordPress users are strongly urged to update their Age Gate plugin immediately to mitigate the risk.
Related Posts:
- Americans have lost more than $2.7 billion to social media scams since 2021
- Cyberattack Compromises Marin City Housing Project, $950,000 in Public Funds Stolen
- Dutch police arrested 3 ransomware criminals, aged only 18-21, who made illegal profits of 2.5 million euros