Cisco on Wednesday announced that it has patched two vulnerabilities in its BroadWorks CommPilot Application Software, which has been assigned a “high severity” rating, based on its CVSS score.
The high-severity vulnerability was found during the resolution of a Cisco TAC support case. Track as CVE-2022-20958 (CVSS score: 8.3), the bug is caused by insufficient validation of user-supplied input. By sending a specially crafted HTTP request, an attacker could exploit this vulnerability to execute arbitrary code on the system.
According to Cisco, “An attacker could exploit this vulnerability by sending a crafted HTTP request to the web interface of an affected device. A successful exploit could allow the attacker to execute arbitrary code on an affected device as the bworks user. This would allow the attacker to read arbitrary files in the file system and or interrupt some of the running processes.”
The second bug tracked as CVE-2022-20951 (CVSS score: 7.7) is a server-side request forgery. This bug was caused by insufficient validation of user-supplied input. By sending a specially crafted HTTP request, a remote authenticated attacker could exploit this vulnerability to perform a server-side request forgery (SSRF) attack on an affected device.
“This vulnerability is due to insufficient validation of user-supplied input. An attacker could exploit this vulnerability by sending a crafted HTTP request to the web interface of an affected device. A successful exploit could allow the attacker to obtain confidential information from the Cisco BroadWorks server and other devices on the network,” read the Cisco advisory.
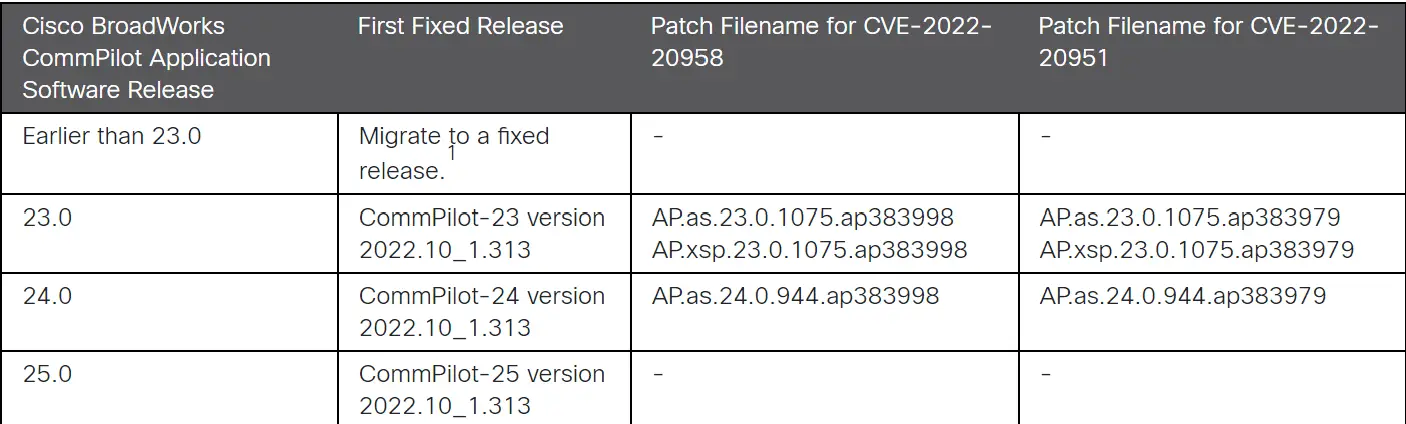
The CVE-2022-20958 and CVE-2022-20951 bugs can impact several Cisco products if they are running a BroadWorks CommPilot Application Software earlier than 23.0.

Cisco says there is no evidence that these flaws have been exploited in malicious attacks.