In the fast-paced world of Internet communications, staying ahead of security threats is not just a choice but a necessity. Recently, 3CX, a renowned VoIP communications company, has issued a stark warning to its customers, highlighting a critical security vulnerability that could potentially compromise vast amounts of sensitive data.
Identified as CVE-2023-49954, this security loophole is an SQL Injection flaw found in 3CX CRM Integration. SQL Injection, a common but dangerous web security vulnerability, allows attackers to interfere with the queries that an application makes to its database. This can lead to unauthorized access to sensitive data, and in severe cases, complete database takeover.
The vulnerability specifically targets the CRM integration templates provided by 3CX for connecting to various databases such as MongoDB, MsSQL, MySQL, and PostgreSQL. These templates, using placeholders like [FirstName], [SearchText], and [Email], fail to sanitize user input adequately. This oversight opens a gateway for SQL injection attacks, allowing malicious actors to manipulate database queries and potentially access or corrupt valuable data.
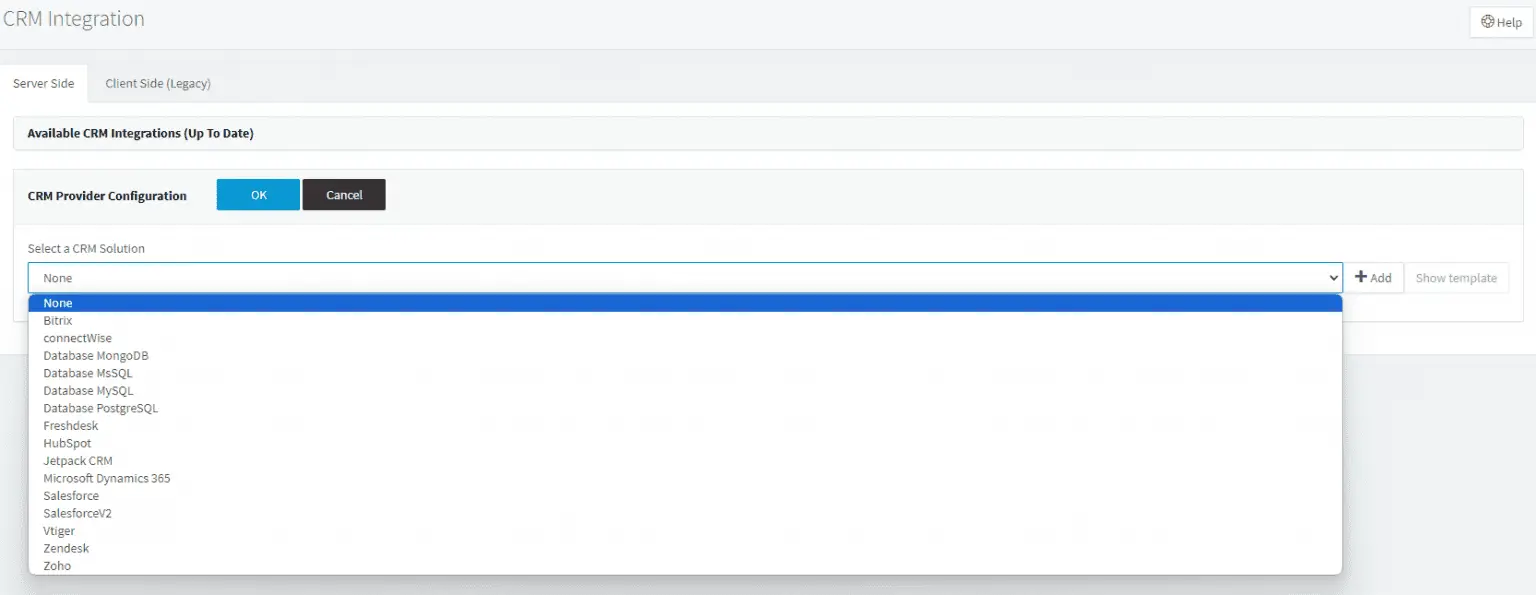
The CVE-2023-49954 vulnerability impacts versions 18 and 20 of 3CX’s VoIP software. Unfortunately, as of now, there is no available update to rectify this flaw. The company’s Chief Information Security Officer, Pierre Jourdan, has emphasized that the only viable solution, at this moment, is to deactivate the CRM integration by setting the CRM solution to ‘None’.
While it might seem like a minor glitch, the scale of the impact is not negligible. According to Jourdan, approximately 0.25% of 3CX’s user base, which includes at least 350,000 companies, might be exposed to this vulnerability. This translates to a minimum of 875 customers who are potentially at risk.
In response to this emerging threat, 3CX has taken a proactive stance by advising its customers to disable their SQL Database integrations immediately. This includes databases like MongoDB, MsSQL, MySQL, and PostgreSQL. Such a preventive measure, though disruptive, is crucial to safeguard against any potential SQL injection attacks until a fix is developed.