Deepin Linux, renowned for its beauty and simplicity, is a hallmark of open-source technology. Developed by a talented Chinese team, it promises a user-friendly, secure, and stable experience. The default document reader in Deepin Linux, known as “deepin-reader”, has recently been spotlighted for a serious vulnerability. This flaw, stemming from a design oversight, enables remote command execution through specially crafted docx documents.
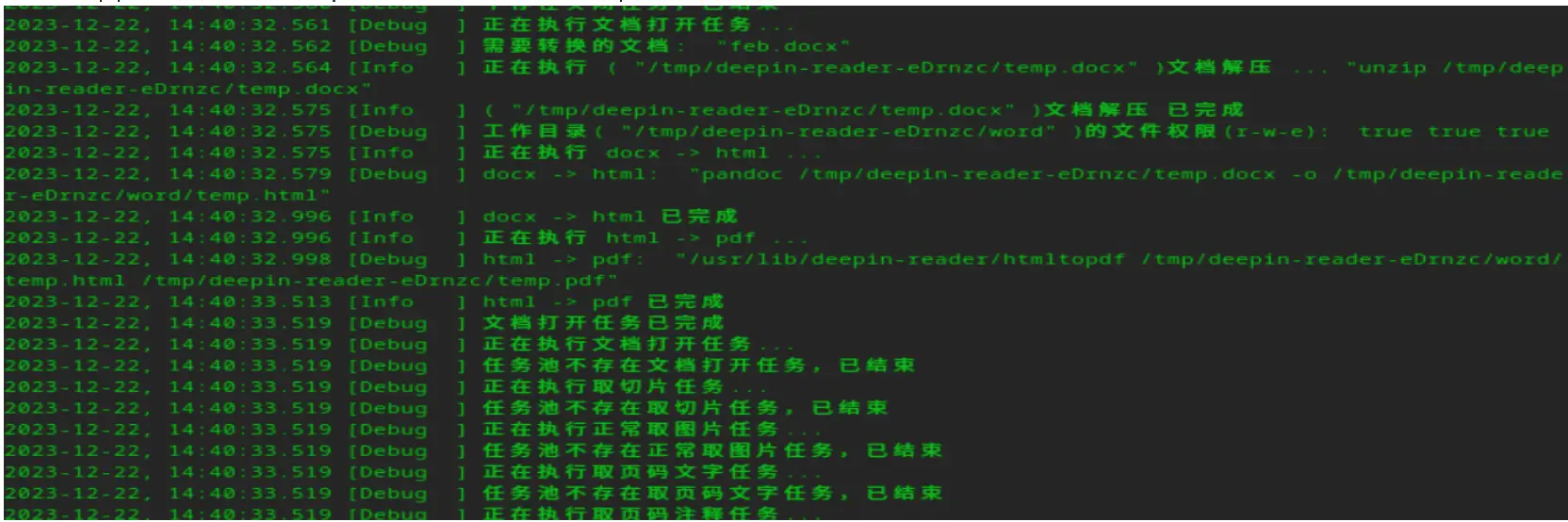
When a user opens a docx file, deepin-reader embarks on a multi-step journey:
1. Creation of a Temporary Directory: The reader places the docx document in a temporary directory under /tmp.
2. Unzipping the Document: Utilizing the “unzip” shell command, it extracts the contents of the docx file.
3. Converting to HTML: Post-extraction, “pandoc” is summoned to convert the docx to an HTML file, resulting in “temp.html” in the word/ directory.
4. Final Conversion to PDF: The HTML file is then transformed into a PDF for viewing.

This routine process, however, harbors a potential flaw.
The vulnerability lies in the manipulation of the “word/temp.html” symlink in a malicious docx file. This symlink can be pointed to any file within the target system. Consequently, when the docx file is opened, pandoc inadvertently writes to the system file linked by the symlink.
Tracked as CVE-2023-50254 and scoring a concerning 8.2 on the CVSS scale, this is classified as a file overwrite vulnerability. The real danger unfolds when critical files like .bash_rc or .bash_login are overwritten. The malicious code executes as soon as the unsuspecting user opens the terminal.
CVE-2023-50254 affects versions of deepin-reader prior to 6.0.7. Credit for unearthing this flaw goes to security researcher Febinrev, who identified the vulnerability and published a proof-of-concept.
Fortunately, the Deepin team has released a patch to address this issue. So, if you’re a Deepin user, updating your system to the latest version is your best defense against this document-borne Trojan horse.