Image: Nvidia
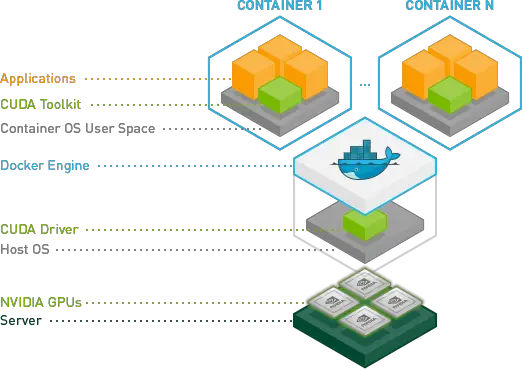
NVIDIA has recently issued a security bulletin addressing two vulnerabilities in its Container Toolkit (CTK), which could potentially expose organizations relying on GPU-accelerated containers to a variety of cyber threats. The affected versions of the NVIDIA Container Toolkit, up to v1.16.1, contain Time-of-check Time-of-use (TOCTOU) vulnerabilities (CVE-2024-0132 and CVE-2024-0133) that could lead to severe consequences if left unpatched.
- CVE-2024-0132 (CVSS 9.0): This critical TOCTOU vulnerability allows a specially crafted container image to exploit the default configuration of the NVIDIA Container Toolkit. If successfully exploited, attackers could gain unauthorized access to the host’s file system. This vulnerability opens doors to potential code execution, escalation of privileges, denial of service (DoS) attacks, as well as information disclosure and data tampering. Notably, use cases where the Container Device Interface (CDI) is employed remain unaffected.
- CVE-2024-0133 (CVSS 4.1): The second vulnerability, although rated with a lower severity score, allows a crafted container image to create empty files on the host’s file system, leading to data tampering. Similar to the first vulnerability, CDI use cases are not affected.
For organizations leveraging GPU-accelerated containers in their infrastructure, these vulnerabilities present a critical risk, especially CVE-2024-0132, which could enable an attacker to execute malicious code or escalate privileges across the host system. Attackers could potentially compromise the security of the host environment, leading to loss of sensitive data and interruption of business operations.
NVIDIA has released security patches in response to these vulnerabilities:
- NVIDIA Container Toolkit: The vulnerability has been resolved in version 1.16.2.
- NVIDIA GPU Operator: An update to version 24.6.2 resolves the issues related to this component.
Users and administrators are strongly encouraged to update their systems to the latest versions immediately to mitigate potential exploitation risks.
Related Posts:
- Hacker group threatens to expose Nvidia driver and firmware data
- Nvidia’s internal systems were attacked by hackers
- Hacker group stole the credentials of over 71,000 Nvidia employees
- Samsung allegedly hit by hackers