The Apache Software Foundation has issued a critical security advisory warning users of a remote code execution (RCE) vulnerability in its popular graph database, HugeGraph. Tracked as CVE-2024-27348, the flaw affects versions 1.0.0 to 1.2.1 when running on Java 8 or Java 11.
The vulnerability resides in HugeGraph’s Gremlin traversal language interface, which allows users to interact with the graph database. An attacker could exploit this flaw by sending specially crafted requests to the Gremlin server, potentially gaining the ability to execute arbitrary code on the underlying system.
This could have devastating consequences, including the theft or manipulation of sensitive data, the disruption of services, and the installation of additional malware.
Any organization using a vulnerable version of Apache HugeGraph is at risk. Due to the widespread use of graph databases in various industries, including finance, healthcare, and social networking, the potential impact of this vulnerability is significant.
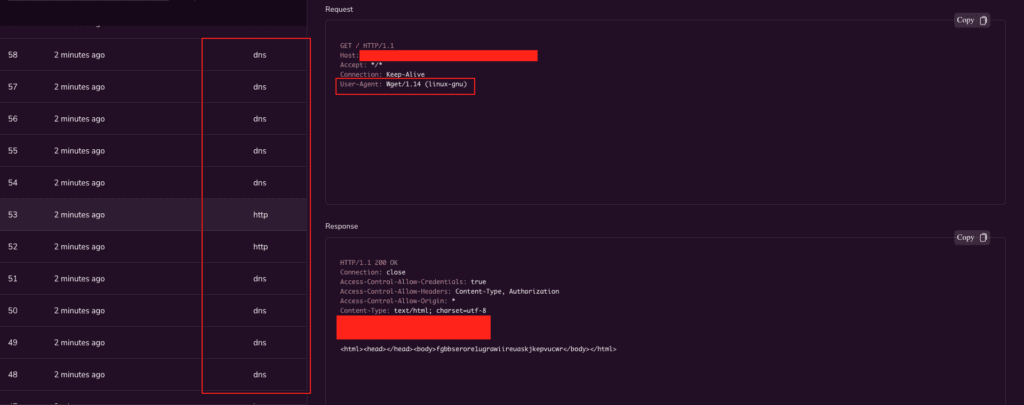
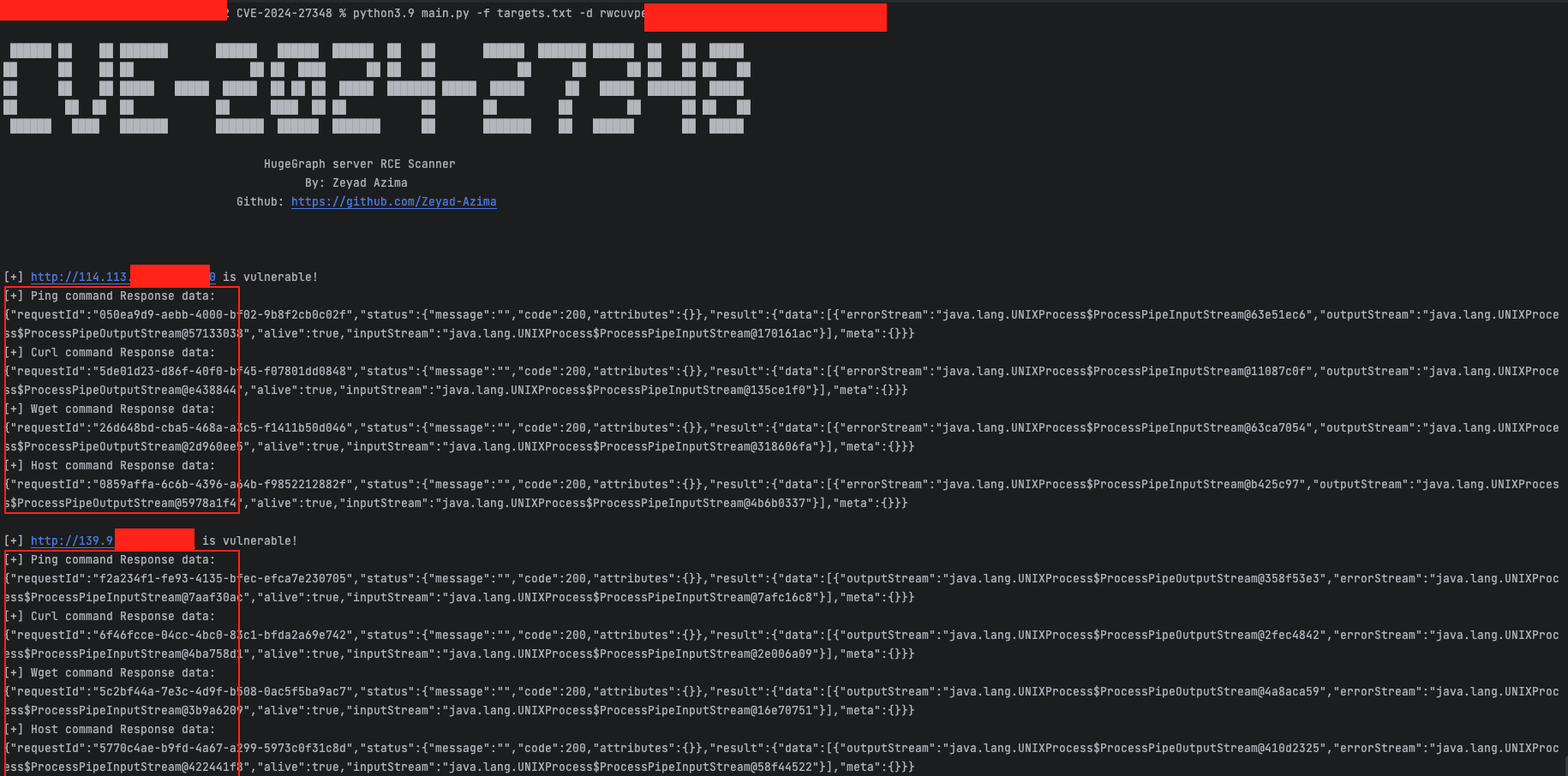
Adding to the urgency of the situation, security researcher Zeyad Azima has recently published a proof-of-concept exploit code for the CVE-2024-27348 vulnerability. This Python script, which can execute commands on a targeted system, underscores the need for swift action to mitigate the risk.
The Apache Software Foundation urges users to immediately take the following actions:
- Upgrade: Update to HugeGraph version 1.3.0 or later, ensuring it runs on Java 11.
- Enable Authentication: Implement the built-in authentication system to restrict access to the Gremlin server.
- Whitelist IP Addresses: Configure the “Whitelist-IP/port” function to further limit access to authorized sources.