Image: Rapid7
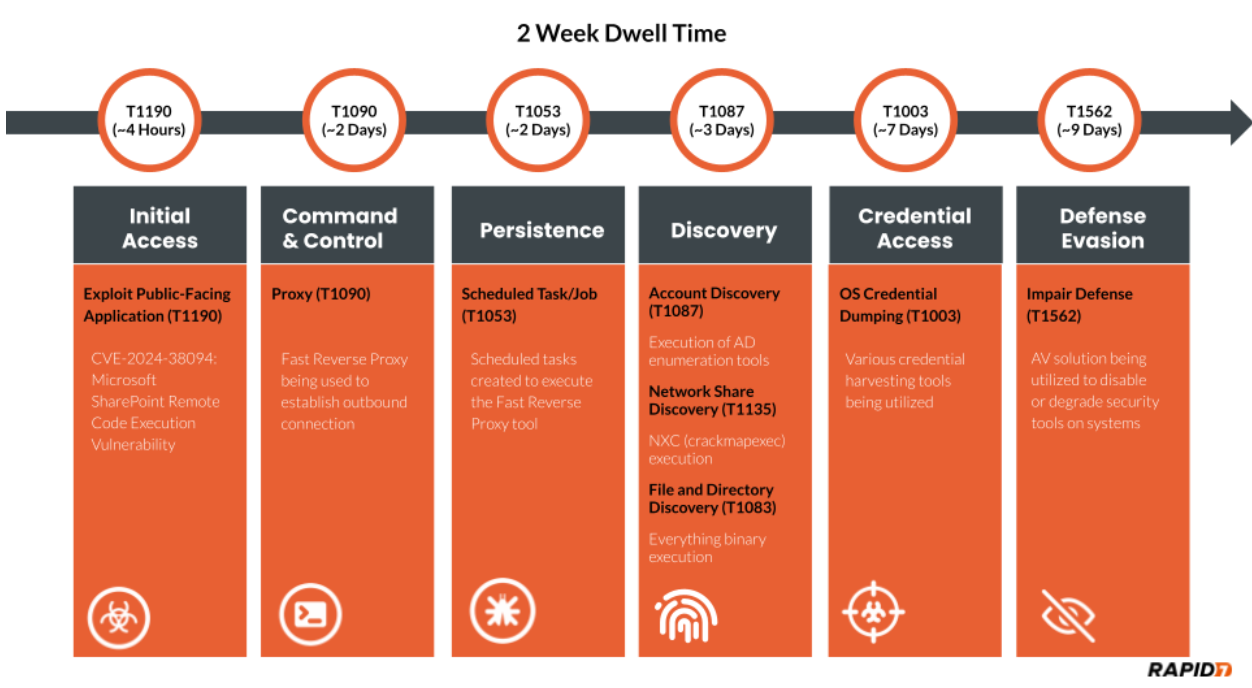
A recent report from Rapid7’s Incident Response team reveals a serious compromise of a Microsoft SharePoint server that enabled an attacker to gain entire domain access, impacting critical systems through a sophisticated blend of techniques. This incident, attributed to the exploitation of CVE-2024-38094, underscores the importance of swift detection and response to vulnerabilities in on-premise SharePoint servers.
The investigation began when Rapid7 noticed suspicious activity involving a Microsoft Exchange service account with domain administrator privileges. Rapid7 identified the attack vector as a known vulnerability, CVE-2024-38094, in the SharePoint server, explaining, “Exploitation for initial access has been a common theme in 2024, often requiring security tooling and efficient response procedures to avoid major impact.” This vulnerability allowed attackers to execute remote code, giving them the foothold needed to move laterally across the network undetected for two weeks.
Once inside, the attacker leveraged the compromised Exchange service account to install the Horoung Antivirus (AV), a Chinese antivirus product, which interfered with the system’s active security measures. This interference led to a crash of the existing security solutions, enabling the attacker to freely pursue their objectives. Rapid7 noted, “The installation of Horoung caused a conflict with active security products… resulting in a crash of these services,” a clear example of the Impairing Defenses (T1562) tactic. This intentional crash granted the attacker the ability to install and run malicious tools, including Impacket, for lateral movement.
From the compromised SharePoint server, the attacker deployed Mimikatz to extract credentials and tampered with system logs to cover their tracks. Evidence indicated that “a majority of system logging was disabled,” the report states, making detection challenging. Additionally, the attacker utilized a webshell called ghostfile93.aspx to establish persistent access, generating numerous HTTP POST requests from a single external IP. The presence of this webshell and other malicious executables, such as Fast Reverse Proxy (FRP), allowed the attacker to map the network, gather credentials, and establish external connections.
Rapid7 observed a range of binaries used by the attacker, each designed to expand control within the domain. The attacker ran everything.exe to index the NTFS file system and Certify.exe to create Active Directory Federation Services (ADFS) certificates, granting them elevated privileges. Kerbrute, a tool for brute-forcing Kerberos tickets, was also deployed, indicating a targeted approach to compromise authentication mechanisms within the network. The report highlights, “These TTPs involved utilizing several binaries to include everything.exe, kerbrute_windows_amd64.exe, 66.exe, Certify.exe, and attempts to destroy third-party backups.”
Rapid7’s analysis emphasizes the need for robust logging and early detection measures. The advisory underscores that “analysis of authentication event logs from the domain controllers” is essential for detecting anomalous activity, particularly involving privileged accounts. It recommends reviewing security policies, strengthening log monitoring, and applying the latest patches, especially in high-risk services like SharePoint, to prevent similar breaches.
Related Posts:
- Microsoft’s September Patch Tuesday: A Patchwork of Urgency with 4 Zero-Days Under Attack
- Kimsuky APT: New TTPs Revealed in Rapid7 Cybersecurity Report
- Cybercriminals Evolve Social Engineering Tactics, Exploit CVE-2022-26923 in Sophisticated Campaign
- PoC Released for SharePoint Pre-Auth RCE Chain (CVE-2023-29357 & CVE-2023-24955)
