CVE-2024-5276 (CVSS 9.8): Critical SQLi Flaw in Fortra FileCatalyst Workflow, PoC Available
A critical SQL Injection vulnerability (CVE-2024-5276) has been discovered in Fortra FileCatalyst Workflow, a popular enterprise file transfer solution. This vulnerability could allow attackers to tamper with application data, potentially creating administrative users, deleting data, or modifying sensitive information within the application database.
Vulnerability Details and Potential Impact
The vulnerability, rated with a CVSS score of 9.8, stems from the software’s failure to properly validate user input. This allows malicious actors to craft SQL statements that can manipulate the underlying database, potentially leading to data corruption and unauthorized access.
“A SQL injection vulnerability exists, whereby an attacker can utilize a script to implement the injection and execute an undesired SQL command, including table deletion or creating an admin-level user. An admin-level user has privileges that may affect other FileCatalyst components within your deployment,” Fortra warns.
Tenable Research, who discovered and reported the CVE-2024-5276 flaw, has released a proof-of-concept (PoC) exploit code, raising concerns that attackers could quickly leverage this vulnerability. While data exfiltration via SQL injection is not currently possible, the impact of data modification or unauthorized access could be severe for organizations relying on FileCatalyst Workflow.
Mitigation and Recommendations
Fortra has released an updated version of FileCatalyst Workflow (5.1.6 build 139) that addresses this critical vulnerability. Users are strongly urged to upgrade their systems immediately to protect their data and infrastructure.
For those who cannot immediately upgrade, Fortra has provided mitigation steps to disable the vulnerable servlets within FileCatalyst Workflow.
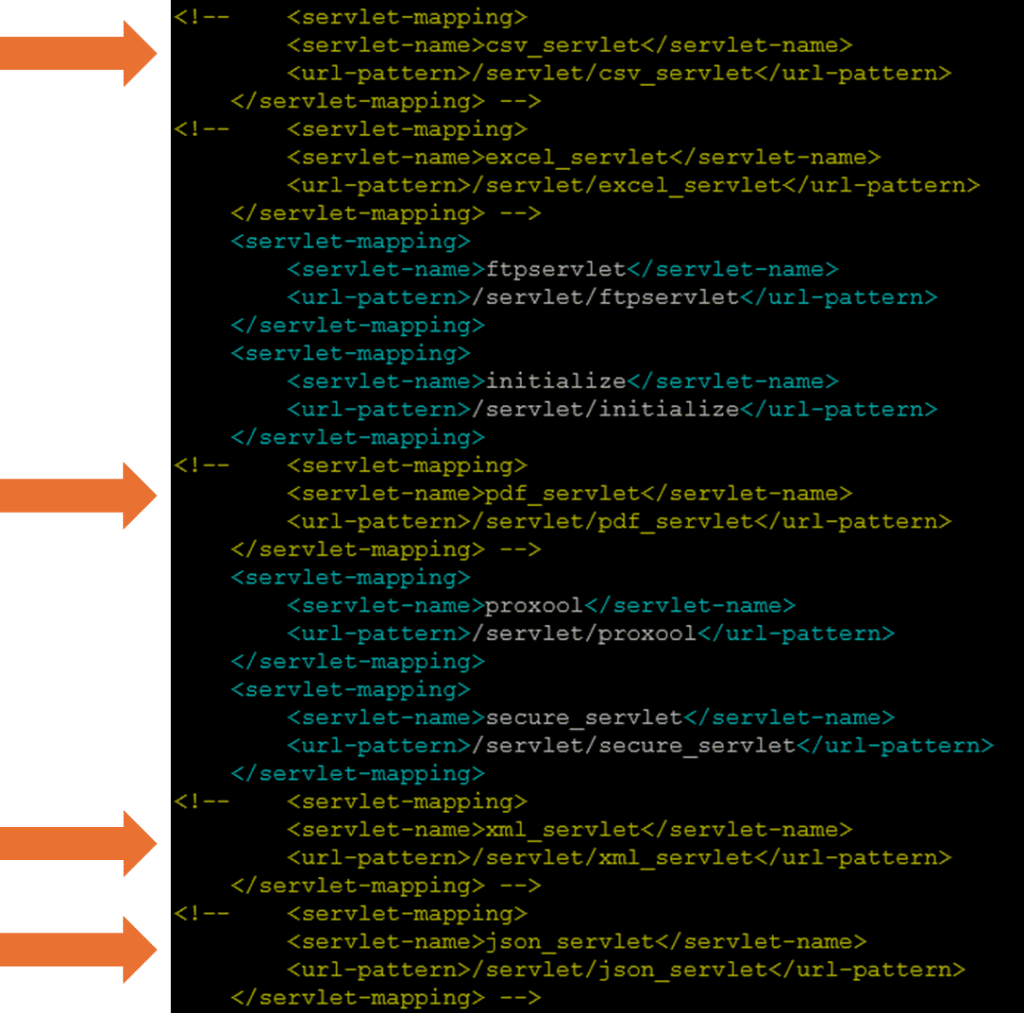
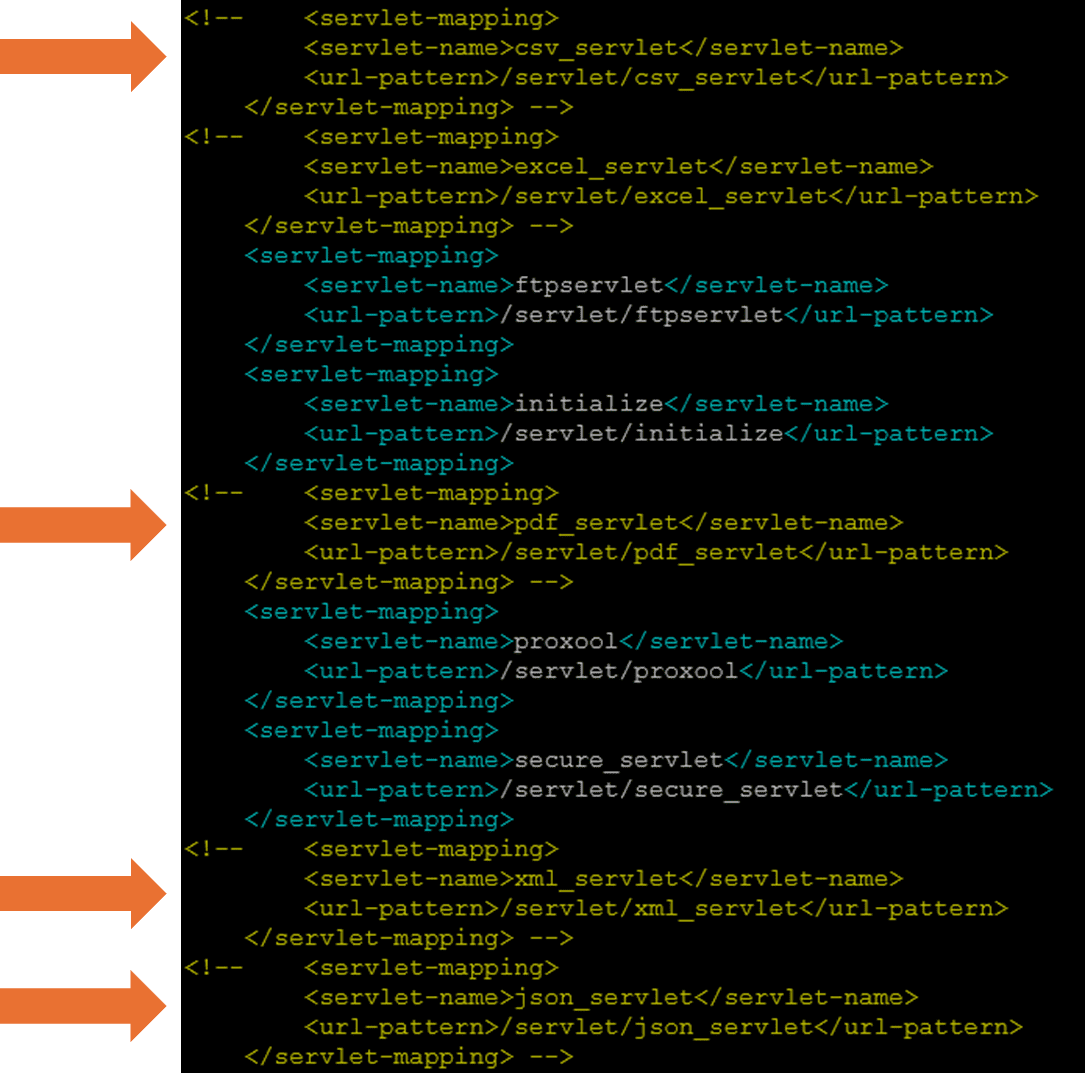
- Navigate to the “web.xml” file located at:
<tomcat install dir>/webapps/workflow/WEB-INF/web.xml - Edit the file and comment out the servlet mapping blocks (as shown in the below screenshot) for:
csv_servlet, pdf_servlet, xml_servlet, json_servlet - Save the changes to the file and restart your Tomcat instance