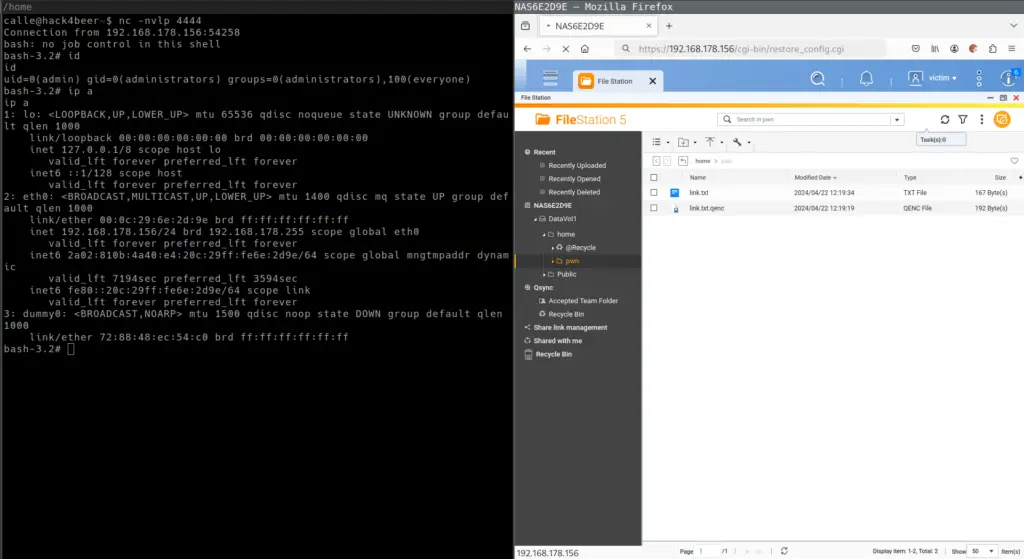
Security researcher c411e published a proof-of-concept (PoC) exploit code for a severe vulnerability in QNAP NAS devices, identified as CVE-2024-53691, with a CVSS score of 8.7. Exploitation of this flaw allows attackers to escalate privileges and achieve remote code execution (RCE) as the root user, posing significant risks to affected systems.
The vulnerability resides in QNAP’s file encryption and decryption functions, which can be abused through a crafted ZIP file containing symbolic links (symlinks). By exploiting this, attackers with standard user access can manipulate the system’s file paths to overwrite critical files.
A Proof-of-Concept (PoC) exploit demonstrates how attackers can gain complete control over the device:
- Prepare Exploit Payload:
- A symbolic link is created and compressed into a ZIP file.
- The target is the restore_config.cgi file for triggering malicious commands.
- Execute Reverse Shell:
- A payload script with a reverse shell command is crafted.
- By encrypting and then decrypting the payload using QNAP’s built-in file operations, attackers overwrite the symbolic link target file.
- Trigger Code Execution:
- The final step involves opening a specific endpoint (/cgi-bin/restore_config.cgi) to execute the reverse shell.
This sequence enables attackers to achieve RCE, allowing them to control the device entirely. c411e has also published a proof-of-concept (PoC) exploit code, which demonstrates CVE-2024-53691’s potential for remote code execution.
QNAP devices are often used to store and back up sensitive data, making them attractive targets for cybercriminals. Exploitation of this vulnerability can lead to:
- Data Theft: Stealing sensitive files stored on the device.
- Ransomware: Encrypting data and demanding payment for decryption keys.
- Malware Deployment: Installing malicious software to spy on or disrupt the network.
This flaw affects QNAP’s QTS 5.1.x and QuTS hero h5.1.x operating systems. QNAP has addressed this vulnerability in their latest software updates, QTS 5.2.0.2802 build 20240620 and later, and QuTS hero h5.2.0.2802 build 20240620 and later. Users are strongly recommended to patch their systems promptly to mitigate the risk of cyberattacks.
Related Posts:
- QNAP Addresses High Severity Vulnerabilities in License Center and Operating Systems
- QNAP detects a large number of ransomware attacks
- QNAP Counters Massive Weak Password Onslaught, Shields NAS Devices
- DeadBolt ransomware is threatening QNAP users
- Critical Vulnerabilities in QNAP Notes Station 3: Update Now to Protect Your Data
