Image: SSD Secure Disclosure
A newly disclosed security advisory details a significant vulnerability within the Linux kernel, specifically impacting Ubuntu 22.04 users. The vulnerability, tracked as CVE-2025-0927, a heap overflow in the HFS+ file system implementation, could allow an attacker to escalate local privileges on affected systems.
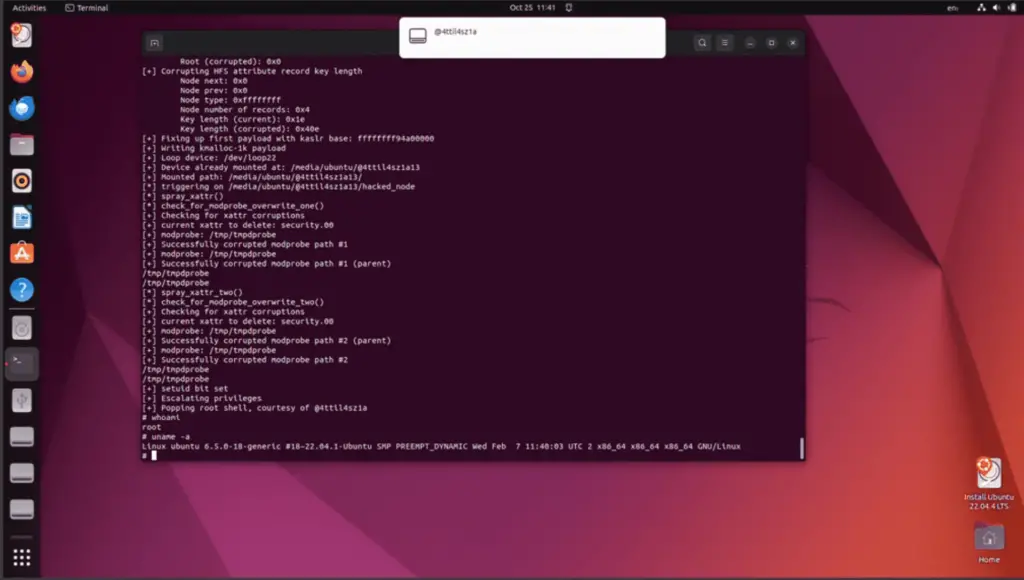
The flaw resides in the HFS+ driver of the Linux kernel. According to the advisory, the vulnerability is a buffer overflow in B-tree node processing. Under specific conditions, the hfs_bnode_read_key function, located in fs/hfsplus/bnode.c, is used to populate an in-kernel buffer from the filesystem, but it lacks proper boundary checks on the size of the key.
The advisory notes the following:
“Our understanding is that the authors must have assumed that this function was called only in contexts where it had been verified for B-tree records that the corresponding keys stored within those had reasonable length values.”
Interestingly, the vulnerability’s presence in the Linux kernel dates back to its initial git repository build in 2005, specifically Linux-2.6.12-rc2.
The vulnerability impacts the Linux Kernel up to version 6.12.0 and Ubuntu 22.04 with Linux Kernel 6.5.0-18-generic.
To exploit this vulnerability, an attacker needs to be able to mount a specially crafted file system. While historically, mounting file systems has been restricted to processes with the CAP_SYS_ADMIN capability, the introduction of namespaces has led to discussions about relaxing these restrictions.
A cybersecurity researcher released a public proof-of-concept exploit for this flaw.
The advisory highlights this shift:
“With unprivileged mounts, a hostile attacker doesn’t need physical access to the machine to exploit lurking kernel filesystem bugs. i.e., they can just use loopback mounts, and they can keep mounting corrupted images until they find something that works.”
In the context of Ubuntu, the advisory points out that both the Desktop and Server versions come with default polkit rules that allow users with an active local session to create loop devices and mount various block file systems. This effectively bypasses the CAP_SYS_ADMIN restrictions that the kernel imposes on normal users.
The Common Vulnerability Scoring System (CVSS) has assigned a score of 7.8 to CVE-2025-0927. An attacker exploiting this vulnerability could cause a denial of service (system crash) or potentially execute arbitrary code.
Ubuntu has addressed this vulnerability in their security advisory and accompanying fix. Users of affected systems are strongly advised to apply the provided patches as soon as possible.