Image: Network-Sec
A vulnerability in the Windows Disk Cleanup Tool (cleanmgr.exe) has been patched by Microsoft as part of its February 2025 Patch Tuesday. Tracked as CVE-2025-21420, the flaw could allow an attacker to gain SYSTEM privileges on a vulnerable system. This vulnerability, scoring a CVSS rating of 7.8, poses a significant risk to Windows users.
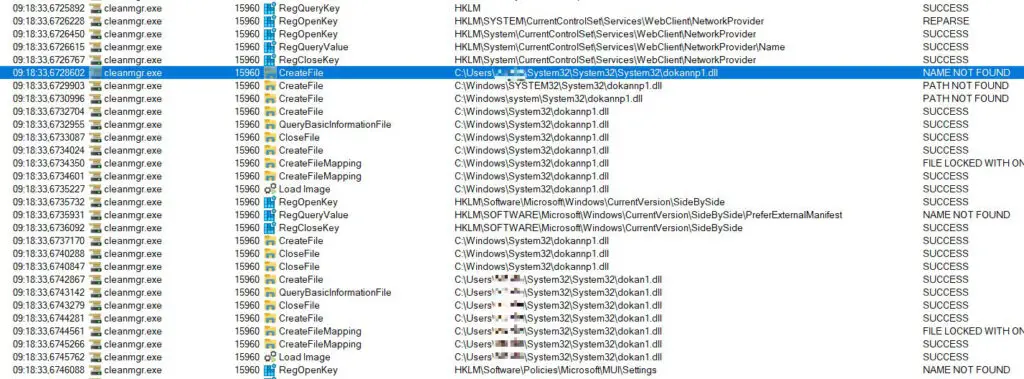
The vulnerability was anonymously disclosed to Microsoft and subsequently, a proof-of-concept exploit was published on GitHub by a security researcher. The exploit leverages a DLL sideloading technique with cleanmgr.exe. Essentially, the researcher demonstrated how a malicious DLL could be disguised and loaded by the Disk Cleanup tool, effectively hijacking its execution path.
The published proof-of-concept outlines the following steps:
The researcher’s notes indicate that standard DLL sideloading techniques are employed. While they were still investigating the precise mechanism for privilege escalation, they suggested that scheduling cleanmgr.exe to run under the NT AUTHORITY\SYSTEM account or waiting for a system-triggered execution (e.g., due to low disk space or excessive temporary files) could be potential avenues.
Microsoft has addressed this vulnerability in its February 2025 Patch Tuesday release. This patch includes fixes for 55 security flaws, including four zero-day vulnerabilities, two of which are actively being exploited in the wild. Users are strongly advised to apply this update immediately to protect their systems from potential attacks.
The relatively simple nature of the exploit, coupled with the potential for SYSTEM-level compromise, makes CVE-2025-21420 a serious threat. Users who have not yet applied the February 2025 patch should prioritize doing so to mitigate the risk. Further details about the patch and the other vulnerabilities addressed can be found on the Microsoft Security Response Center website.