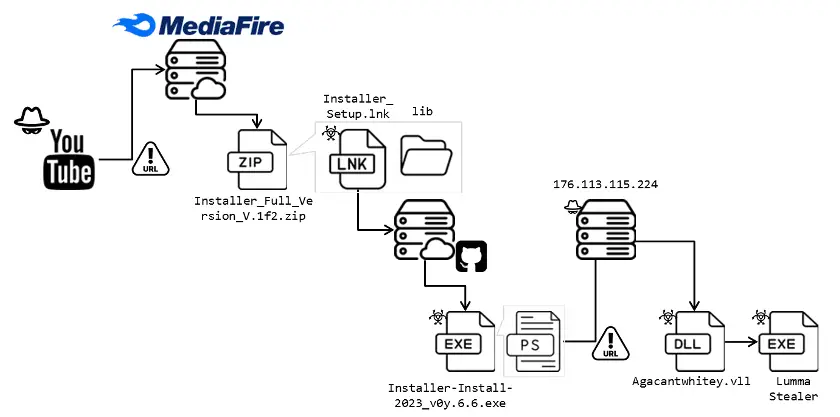
Attack flow | Image: FortiGuard Labs
In an era where digital threats lurk behind every click, a new predatory tactic has emerged, blurring the lines between harmless content and cyber threats. FortiGuard Labs recently unveiled a cunning stratagem employed by a threat group, exploiting YouTube channels to disseminate a variant of the notorious Lumma Stealer malware.
The threat actors ingeniously breach YouTuber accounts, uploading videos that masquerade as guides for installing cracked software. Embedded within these seemingly benign videos are malicious URLs. These URLs, often shortened by services like TinyURL and Cuttly, lead to downloads of a ZIP file, camouflaged as legitimate software but laden with the Lumma Stealer variant. This method’s efficacy is proven by the growing number of downloads, signifying the effectiveness of YouTube as a malware distribution channel.

Lumma Stealer, primarily targeting sensitive information like user credentials, system details, and browser data, has been a dark web and Telegram channel fixture since 2022. The malware’s global reach, evidenced by its command-and-control (C2) servers, highlights its pervasive threat. This variant is engineered to stealthily infiltrate systems, eluding detection with sophisticated obfuscation techniques.
The initial stage involves a .NET loader, hosted on platforms like GitHub, camouflaging its nefarious intent. The loader, obfuscated with SmartAssembly, verifies system environments before proceeding. It employs a PowerShell script to connect to remote servers, retrieve encrypted binary data, and decipher the ultimate payload of Lumma Stealer. Anti-VM and anti-debugging techniques further cloak its presence, thwarting common security measures.
Upon successful deployment, Lumma Stealer activates, targeting a plethora of user data. It can access crypto wallets, browser extensions, and other sensitive data. Communicating with a C2 server, it facilitates the exchange of instructions and transmission of stolen data. The malware’s ability to update its exfiltration tactics to leverage HTTPS signals its evolving sophistication.
This attack vector, exploiting YouTube’s popularity and the allure of free software, is a stark reminder of the evolving landscape of cyber threats. Users must remain vigilant, questioning the legitimacy of software sources and relying on secure, reputable origins for their digital needs.