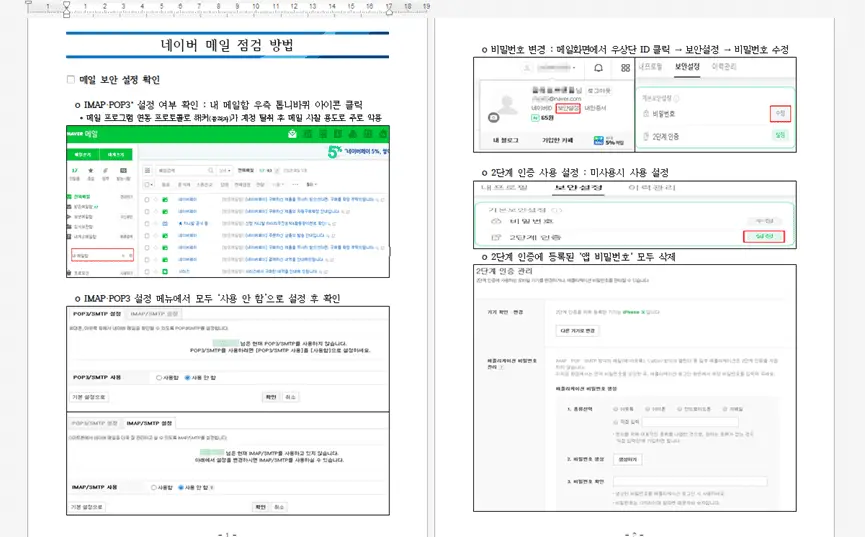
Cybersecurity specialists at Qi An Xin have unearthed malicious LNK files specifically targeting users in South Korea. Upon execution, these files unfurled decoy documents and VB scripts. Notably, one such document masqueraded as a guide on conducting electronic mail security checks.
Initially, the experts hypothesized that the onslaught originated from the North Korean faction APT37, known for employing similar dissemination tactics for malicious software. However, a meticulous scrutiny of the scripts and server addresses implicated the equally North Korean Konni group.

In their stratagem, the Konni group leveraged LNK files, essentially commonplace Windows shortcuts increasingly used by various threat actors, seemingly to disguise their operations as those of other hacking conglomerates.
In the malicious campaign scrutinized, the Konni scripts, activated via LNK files, orchestrated the following maneuvers:
- They established tasks in the Windows scheduler for recurrent execution of the malevolent code, circumventing the deletion of principal files and maintaining persistent control over the infected system.
- They amassed diverse system information, including process lists, configuration details, and user folder contents.
- They transmitted the gathered data to the malefactors’ command server.
Analysis of the detected malicious software revealed similarities in methods with previously published samples linked to Konni. This includes code concealment techniques, data transmission principles to C2 servers, and technical implementation specifics.
This suggests a potential nexus between Konni and other East Asian groups like APT37 and Kimsuky, known for analogous malevolent code concealment within LNK files and bait file distribution to enhance attack efficacy.
Thus, the scrutinized attack exemplifies both a tactical shift by Konni and a trend toward methodological convergence and knowledge exchange among various APT groups in the Asian region.
To safeguard against such assaults, experts advise adherence to several fundamental principles:
- Exercise caution when handling files from dubious or unverified sources, particularly social media messages and email attachments.
- Routinely back up crucial data for swift restoration in case of infection.
- Promptly install all security updates from software developers, as they often rectify vulnerabilities exploited by perpetrators.
The detected activity of the Konni hacking group underscores the continual evolution of cybercriminal tactics. The employment of social engineering through bait documents, malevolent software distribution via LNK files, and knowledge sharing with other APT groups form a highly effective and perilous repertoire.
While expert recommendations are relatively straightforward, the reality is that an increasing number of threats are capable of circumventing the defenses of average users. Consequently, corporations must invest both in cutting-edge technical solutions like next-generation antivirus software and in enhancing personnel awareness of various cyberattack types.