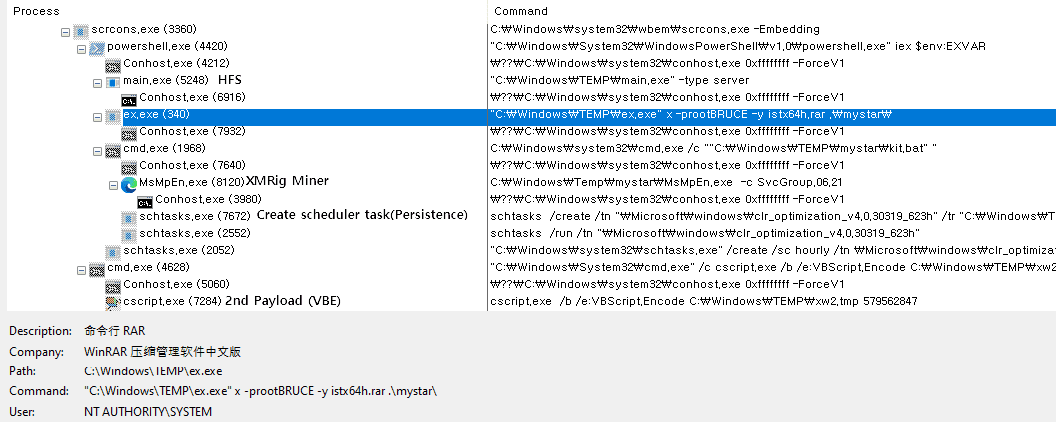
The final process tree | | Image: ASEC
The AhnLab Security Intelligence Center (ASEC) has uncovered a concerning trend in cybercrime involving the misuse of Binary Managed Object Files (BMOFs) for the distribution of XMRig, a notorious cryptocurrency mining malware. This novel attack vector underscores the increasing sophistication of threat actors who are continually adapting their techniques to exploit legitimate system components for malicious purposes.
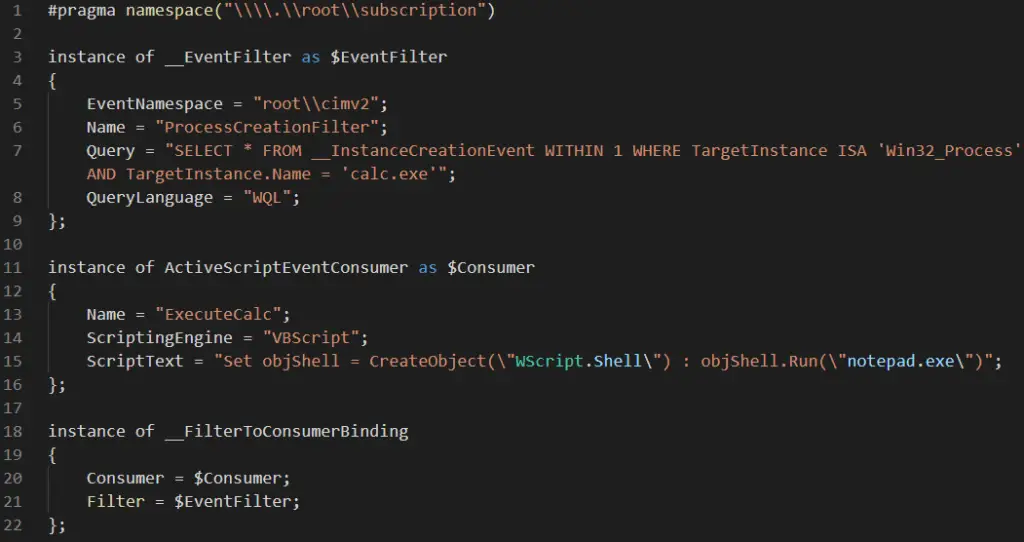
While BMOFs serve essential functions in Windows Management Instrumentation (WMI), their ability to execute scripts has become a point of exploitation. Cybercriminals are leveraging this feature to establish persistent malware presence through the creation of “Permanent Event Subscriptions.” These subscriptions function as triggers, ensuring the malware’s execution and resilience against system reboots, effectively granting attackers continuous access to compromised systems.
The ASEC report reveals that this BMOF-based attack method is often deployed in conjunction with the BondNet malware. BondNet primarily targets SQL servers, leveraging exploits or brute-force attacks to gain initial access. Upon successful intrusion, it proceeds to utilize the compromised BMOF to execute further malicious activities, including downloading additional malware components and, ultimately, installing the XMRig coinminer.
XMRig, a cryptojacking malware, surreptitiously utilizes the victim’s computing power to mine Monero cryptocurrency, generating illicit profits for the attackers at the expense of the compromised system’s performance and energy consumption.
The ability of threat actors to weaponize legitimate system tools like BMOFs highlights the need for robust security measures. Organizations are strongly advised to employ strong password policies, maintain up-to-date software, and deploy comprehensive endpoint protection solutions.
Related Posts:
- Palo Alto Firewalls Under Attack: Critical Flaw Exploited to Deploy Cryptojacking Malware
- Log4j Campaign Exploited to Deploy XMRig Cryptominer
- Beware of “How to Fix” Button: New Phishing Emails Trick Users into Executing Malicious Commands
- Vulnerable Microsoft SQL Server are being targeted by hackers