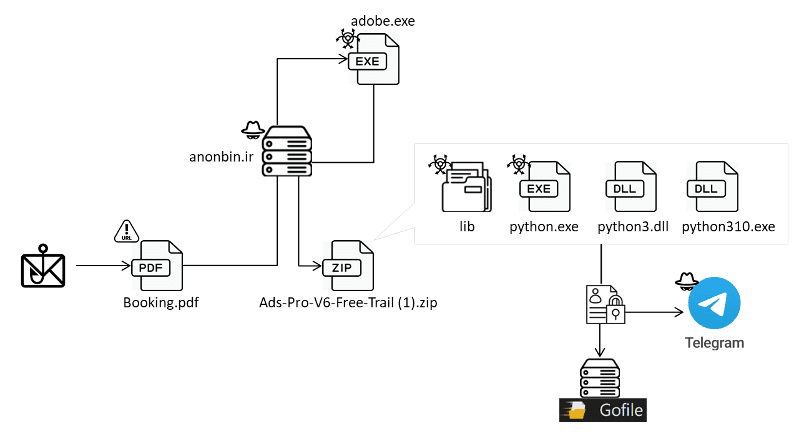
Attack flow | Image:
In a digital age teeming with cyber threats, FortiGuard Labs recently identified an email phishing campaign that spread MrAnon Stealer malware. Crafted with cunning precision, this campaign entices victims through seemingly innocuous hotel booking emails, leading them into a trap laid with malicious intent.
The attack commences with phishing emails, masquerading as hotel room reservation inquiries, with the lure of a holiday season booking. The bait is an attached PDF, seemingly harmless yet harboring a link to download a .NET executable. This file, in turn, unfurls a sequence of events, deploying a PowerShell script that culminates in unleashing the MrAnon Stealer malware.

MrAnon Stealer, a Python-based information stealer, is adept at evading detection, thanks to its compression with cx-Freeze. This malware insidiously harvests a plethora of sensitive data – from credentials and browser sessions to cryptocurrency extensions:
- Browsers Data: 7Star, Amigoz, Bravez, Cent Browser, Chrome Canary, Epic Privacy Browser, Google Chrome, Iridium, Kometa, Microsoft Edge, Opera, Opera GX, Orbitum, Sputnik, Torch, Uran, Vivaldi, Yandex, Firefox, Pale Moon, SeaMonkey, and Waterfox.
- Desktop Wallets: Bytecoin Wallet, Guarda, Atomic Wallet, Coinomi Wallet, Bitcoin Armory, and Exodus.
- Browser Extensions:

- Messengers: Discord, Discord Canary, Element, Signal, Telegram Desktop
- VPN Clients: NordVPN, ProtonVPN, and OpenVPN Connect
- Browser Wallets:
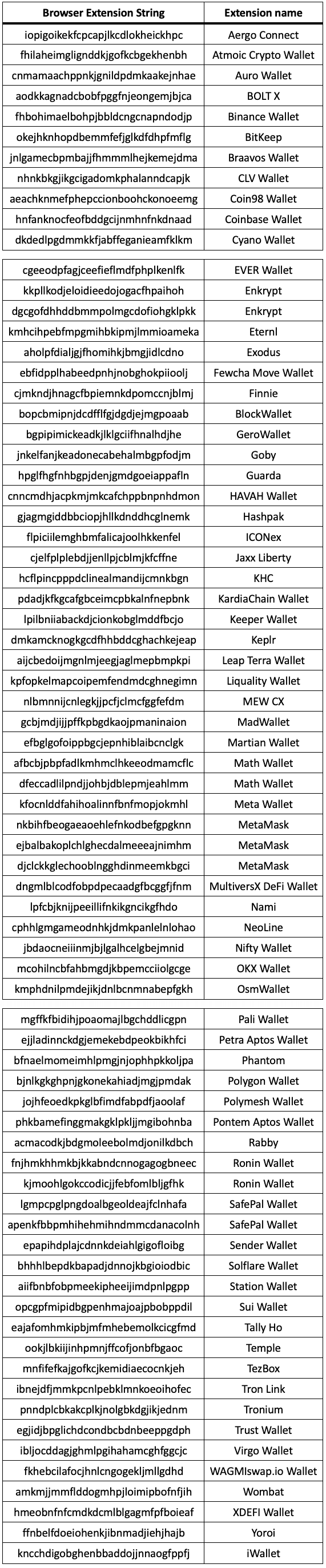
- Others: FileZilla and FileZilla Server
- Gaming: Steam
- Files: It scans these directories: Desktop, Documents, Downloads, Pictures, and grabs specific files with following extensions: “.7z,” “.bmp,” “.conf,” “.csv,” “.dat,” “.db,” “.doc,” “.jpeg,” “.jpg,” “.kdbx,” “.key,” “.odt,” “.ovpn,” “.pdf,” “.png,” “.rar,” “.rdp,” “.rtf,” “.sql,” “.tar,” “.txt,” “.wallet,” “.xls,” “.xlsx,” “.xml,” and “.zip.”
Interestingly, the campaign primarily targeted Germany, with a notable spike in activity observed in November 2023. Given the high severity level of this threat, users are urged to exercise heightened vigilance, particularly with email attachments and unfamiliar PDF files. The MrAnon Stealer campaign serves as a stark reminder of the relentless evolution of cyber threats and the need for constant awareness in our interconnected world.
The MrAnon Stealer’s phishing campaign is a sophisticated blend of social engineering and technical prowess, underlining the ever-evolving landscape of cyber threats. It’s a clarion call for individuals and organizations alike to fortify their defenses and remain vigilant against such devious digital deceptions.