Example brand impersonation domain used to distribute the Atera RAT.
A recent report by Zscaler ThreatLabz sheds light on the rising wave of phishing campaigns, with threat actors increasingly turning to typosquatting and brand impersonation tactics. From February 2024 to July 2024, the research team analyzed over 30,000 lookalike domains linked to some of the most popular global brands, uncovering that over 10,000 of these domains were malicious in nature.
Leading the pack of impersonated brands are tech giants Google, Microsoft, and Amazon, collectively accounting for nearly 75% of all phishing domains that exploit typosquatting and brand impersonation. Attackers mimic these household names to take advantage of their vast user bases, capitalizing on the high likelihood of stolen credentials being monetized quickly. Typosquatting, where slight misspellings of well-known domains lure users into malicious websites, plays a significant role in these attacks.
ThreatLabz discovered that the Internet Services sector bore the brunt of phishing attacks, with 29.2% of all phishing domains targeting this vertical. Professional Services and Online Shopping websites followed closely, making these sectors prime targets due to the sensitive and financial data they handle. The lucrative nature of these industries, combined with the frequent handling of user credentials and payment information, makes them an attractive target for cybercriminals.
Nearly half of all phishing domains analyzed in the report used free Let’s Encrypt TLS certificates to give the illusion of legitimacy. By securing a “padlock” symbol next to the URL, attackers trick users into believing the site is safe. This tactic enables phishing sites to evade basic browser security warnings, increasing the chances of success.
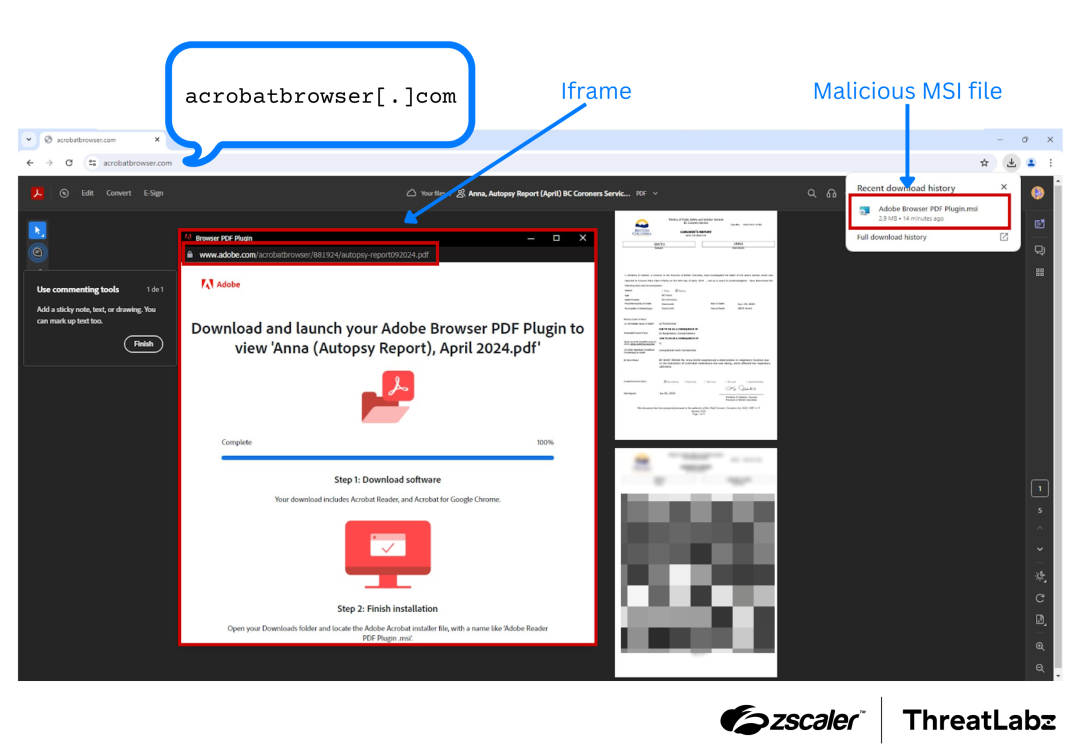
Several case studies in the report highlight the diverse ways in which threat actors leverage these malicious domains. In one instance, the domain acrobatbrowser[.]com was found impersonating Adobe, distributing the Atera Remote Access Trojan (RAT), which allowed attackers to take control of victim systems. Other domains, such as offlice365[.]com, were used to steal credentials by imitating Microsoft Office 365 login pages. Even popular messaging platforms like WhatsApp were exploited, with scammers pretending to represent Amazon, luring victims into sharing personal information for fake job offers.
Phishing domains also serve as conduits for more advanced operations, including command-and-control (C2) communication. One notable case involved the domain onedrivesync[.]com, where attackers used a TacticalRMM tool disguised as Microsoft OneDrive, a trusted application in corporate environments. This allowed threat actors to maintain control over compromised systems, making detection and remediation more difficult for security teams.
With typosquatting and brand impersonation showing no signs of slowing down, the need for heightened vigilance is clear. The report emphasizes the importance of user awareness and corporate cybersecurity measures in combating these attacks. By recognizing these deceptive tactics, users can better protect themselves from falling victim to phishing schemes, and organizations can strengthen their defenses against these ever-evolving threats.
Related Posts:
- Warning: Fake WinRar Websites Distributing Malware
- Attackers Leveraging Public Cobalt Strike Profiles to Evade Detection
- Inside a Python Infostealer: How Attackers Abuse Legitimate Platforms for Credential Theft