Damn Web Scanner: web vulnerabilities scanner
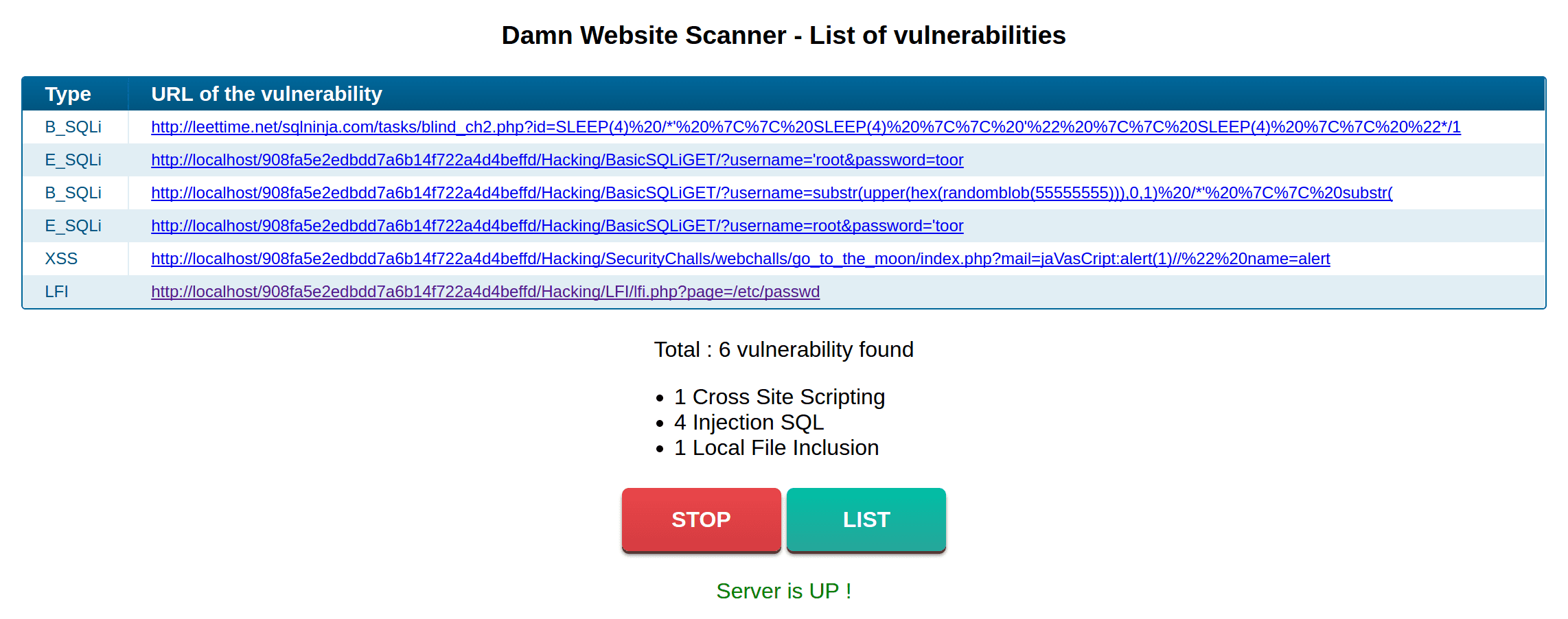
Damn Web Scanner
Another web vulnerabilities scanner, this extension works on Chrome and Opera. The extension is working in the background and will notify you if it finds any vulnerability
Currently, it scans for:
- SQL Injection
- Cross Site Scripting
- Local File Inclusion
- Remote Commands Execution
All the features are:
- Detect if the server is up
- Start/Stop button
- New XSS vectors, work in different contexts (JS var, JS function, inside HTML tag, outside HTML tag)
- Basic page to list the vulnerabilities URL and TYPE
- Time-based SQLi scanner using polyglot vectors (MySQL, SQLite, Oracle, Postgresql, SQL Server)
- RCE scanner using polyglot vectors based on time
- New logo for the extension
- Re-use your cookies and user-agent to get access to page with cookie-authentication
- Export vulnerabilities into a CSV file
- Launch scan when a form is submitted or a page is opened via the URL bar
Warnings: Do not use this extension for the illegal purpose, the main goal of it is to simplify the life of bug hunters. It’s a BETA version, many improvements will come don’t worry
Install
You need to install and configure the server, it uses ghost and flask with gunicorn
If you have any trouble with Ghost you should have a look at the documentation: http://ghost-py.readthedocs.org/en/latest/
1 – The extension isn’t packed, to use it go to chrome://extensions or opera://extensions then select “Load unpacked extension”
2 – Don’t forget to launch the server
Note: if Gunicorn fails you should launch the “server.py” instead 3 – Edit the server configuration in popup.js and background.js with your server’s information
4 – Browse the internet! (Don’t forget to start the extension by clicking the ‘START’ button) You can try the Error SQL, Blind SQL, LFI with Damn Vulnerable Web App
Source: https://github.com/swisskyrepo/





