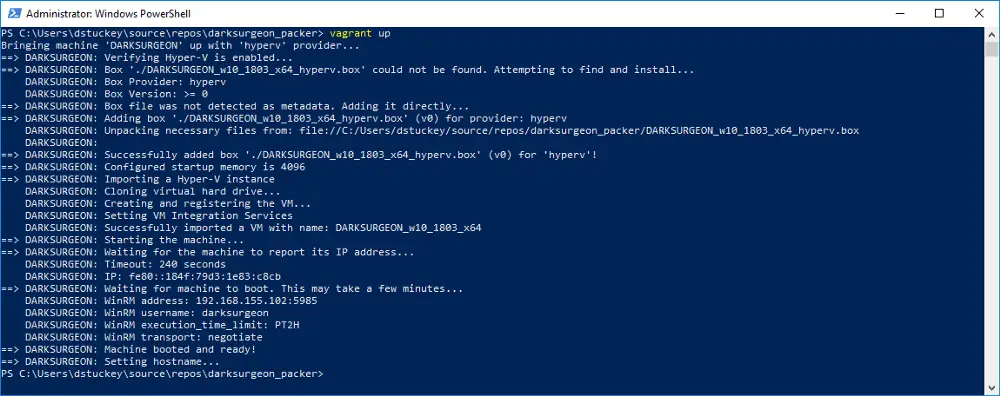
DARKSURGEON is a Windows packer project to empower incident response, digital forensics, malware analysis, and network defense.
DARKSURGEON has three stated goals:
- Accelerate incident response, digital forensics, malware analysis, and network defense with a preconfigured Windows 10 environment complete with tools, scripts, and utilities.
- Provide a framework for defenders to customize and deploy their own programmatically-built Windows images using Packer and Vagrant.
- Reduce the amount of latent telemetry collection, minimize error reporting, and provide reasonable privacy and hardening standards for Windows 10.
DARKSURGEON is based on a few key development principles:
- Modularity is key. Each component of the installation and configuration process should be modular. This allows for individuals to tailor their packer image in the most flexible way.
- Builds must be atomic. A packer build should either complete all configuration and installation tasks without errors, or it should fail. A packer image with missing tools is a failure scenario.
- Hardened out of the box. To the extent that it will not interfere with investigative workflows, all settings related to proactive hardening and security controls should be enabled. Further information on DARKSURGEON security can be found later in this post.
- Instrumented out of the box. To the extent that it will not interfere with investigative workflows, Microsoft Sysmon, Windows Event Logging, and osquery will provide detailed telemetry on host behavior without further configuration.
- Private out of the box. To the extent that it will not interfere with investigative workflows, all settings related to privacy, Windows telemetry, and error reporting should minimize collection.
Hardening
DARKSURGEON is hardened out of the box and comes with scripts to enable High or Low-security modes.
All default installations of DARKSURGEON have the following security features enabled:
- Windows Secure Boot is Enabled.
- Windows Event Log Auditing is Enabled. (Palantir Windows Event Forwarding Guidance)
- Windows Powershell Auditing is Enabled. (Palantir Windows Event Forwarding Guidance)
- Windows 10 Privacy and Telemetry are Reduced to Minimal Settings. (Microsoft Guidance)
- Sysinternals Sysmon is Installed and Configured. (SwiftonSecurity Public Ruleset)
- LLMNR is Disabled.
- NBT is Disabled.
- WPAD is Removed.
- Powershell v2 is Removed.
- SMB v1 is Removed.
- Application handlers for commonly-abused file extensions are changed to notepad.exe.
Low-Security mode is primarily used for virtual machines intended for reverse engineering, malware analysis, or systems that cannot support VBS security controls.
In Low-Security mode, the following hardening features are configured:
- Windows Defender Anti-Virus Real-Time Scanning is Disabled.
- Windows Defender SmartScreen is Disabled.
- Windows Defender Credential Guard is Disabled.
- Windows Defender Exploit Guard is Disabled.
- Windows Defender Exploit Guard Attack Surface Reduction (ASR) is Disabled.
- Windows Defender Application Guard is Disabled.
- Windows Defender Application Guard does not enforce isolation.
Packages
Out of the box, DARKSURGEON comes equipped with tools, scripts, and binaries to make your life as a defender easier.
Android Analysis:
Tools, scripts, and binaries focused on android analysis and reverse engineering.
- APKTool (FLARE)
Blue Team:
Tools, scripts, and binaries focused on blue team, network defense, and alerting/detection development.
- ACE
- Bloodhound / Sharphound
- CimSweep
- Dumpsterfire
- EndGame Red Team Automation (RTA)
- Kansa
- Posh-Git
- Invoke-ATTACKAPI
- LOLBAS (Living Off the Land Binaries And Scripts)
- OSX Collector
- Posh-SecMod
- Posh-Sysmon
- PowerForensics
- PowerSploit
- Practical Malware Analysis Labs (FLARE)
- Revoke-Obfuscation
- Yara (FLARE)
Debuggers:
Tools, scripts, and binaries for debugging binary artifacts.
- Ollydbg (FLARE)
- OllyDump (FLARE)
- OllyDumpEx (FLARE)
- Ollydbg2 (FLARE)
- OllyDump2Ex (FLARE)
- x64dbg (FLARE)
- Windbg (FLARE)
Disassemblers:
Tools, scripts, and binaries for disassembling binary artifacts.
- IDA Free Trial (FLARE)
- Binary Ninja Demo (FLARE)
- Radare2 (FLARE)
Document Analysis: Tools, scripts, and binaries for performing analysis of documents.
- OffVis (FLARE)
- OfficeMalScanner (FLARE)
- PDFId (FLARE)
- PDFParser (FLARE)
- PDFStreamDumper (FLARE)
DotNet Analysis:
Tools, scripts, and binaries for performing analysis of DotNet artifacts.
- DE4Dot (FLARE)
- DNSpy (FLARE)
- DotPeek (FLARE)
- ILSpy (FLARE)
Flash Analysis:
Tools, scripts, and binaries for performing analysis of flash artifacts.
- FFDec (FLARE)
Forensic Analysis:
Tools, scripts, and binaries for performing forensic analysis on the application and operating system artifacts.
- Amcache Parser
- AppCompatCache Parser
- IISGeolocate
- JLECmd
- LECmd
- JumpList Explorer
- PECmd
- Registry Explorer
- Regshot (FLARE)
- Shellbags Explorer
- Timeline Explorer
- TSK (The Sleuthkit)
- Volatility
- X-Ways Forensics Installer Manager (XWFIM)
Hex Editors:
- FileInsight (FLARE)
- HxD (FLARE)
- 010 Editor (FLARE)
Java Analysis:
- JD-GUI (FLARE)
- Dex2JAR
Network Analysis:
- Burp Free
- FakeNet-NG (FLARE)
- Wireshark (FLARE)
PE Analysis:
- DIE (FLARE)
- EXEInfoPE (FLARE)
- Malware Analysis Pack (MAP) (FLARE)
- PEiD (FLARE)
- ExplorerSuite (CFF Explorer) (FLARE)
- PEStudio (FLARE)
- PEview (FLARE)
- Resource Hacker (FLARE)
- VirusTotal Uploader
Powershell Modules:
- Active Directory
- Azure Management
- Pester
Python Libraries:
- Cryptography
- Hexdump
- OLETools
- LXML
- Pandas
- Passivetotal
- PEFile
- PyCryptodome
- Scapy
- Shodan
- Sigma
- Visual C++ for Python
- Vivisect
- WinAppDBG
- Yara-Python
Red Team:
- Grouper
- Inveigh
- Nmap
- Powershell Empire
- PowerupSQL
- PSAttack
- PSAttack Build Tool
- Responder
Remote Management:
- AWS Command Line (AWSCLI)
- OpenSSH
- Putty
- Remote Server Administration Tools (RSAT)
Utilities:
- 1Password
- 7Zip
- Adobe Flash Player
- Adobe Reader
- API Monitor
- Bleachbit
- Boxstarter
- Bstrings
- Checksum
- Chocolatey
- Cmder
- Containers (Hyper-V)
- Curl
- Cyber Chef
- Docker
- DotNet 3.5
- DotNet 4
- Exiftool
- FLOSS (FLARE)
- Git
- GoLang
- Google Chrome
- GPG4Win
- Hashcalc
- Hashdeep
- Hasher
- Hashtab
- Hyper-V
- Irfanview
- Java JDK8
- Java JRE8
- JQ
- Jupyter
- Keepass
- Microsoft Edge
- Mozilla Firefox
- Mozilla Thunderbird
- Neo4j Community
- NodeJS
- Nuget
- Office365 ProPlus
- OpenVPN
- Osquery
- Python 2.7
- Qbittorrent
- RawCap
- Slack
- Sublime Text 3
- Sysinternals Suite
- Tor Browser
- UnixUtils
- UPX
- Visual C++ 2005
- Visual C++ 2008
- Visual C++ 2010
- Visual C++ 2012
- Visual C++ 2013
- Visual C++ 2015
- Visual C++ 2017
- Visual Studio Code
- Windows 10 SDK
- Windows Subsystem for Linux (WSL)
- Winlogbeat
- XorSearch
- XorStrings
Visual Basic Analysis:
- VBDecompiler
You can download DARKSURGEON iso image here.
Copyright (c) 2018 DANΞ
Source: https://github.com/cryps1s/