Deploy-Deception
Deploy-Deception is a PowerShell module to deploy active directory decoy objects.

Functions
Deploy-Deception currently has the following functions:
All the functions must be run on a DC with domain admin privileges. There are multiple attributes and flags which can be set while deploying a decoy. These attributes and flags make the decoy interesting for an attacker. When a right, say, ReadProperty is used to access the decoy, a Security Event 4662 is logged.
Note that Windows Settings|Security Settings|Advanced Audit Policy Configuration|DS Access|Audit Directory Service Access Group Policy needs to be configured to enable 4662 logging.
Deploy-UserDeception
This function sets up auditing when a specified Right is used by a specified principal against the decoy user object.
EXAMPLE
PS C:\> Create-DecoyUser -UserFirstName user -UserLastName manager -Password Pass@123 | Deploy-UserDeception -UserFlag PasswordNeverExpires -Verbose
Creates a decoy user whose password never expires and a 4662 is logged whenever ANY property of the user is read. Very verbose!
Deploy-SlaveDeception
This function sets up auditing when a specified Right is used over the slave user by a master user who has FUllControl/GenericALl over the slave user.
EXAMPLE
PS C:\> Create-DecoyUser -UserFirstName master -UserLastName user -Password Pass@123
PS C:\> Create-DecoyUser -UserFirstName slave -UserLastName user -Password Pass@123 | Deploy-SlaveDeception -DecoySamAccountName masteruser -Verbose
The first command creates a deocy user ‘masteruser’.
The second command creates a decoy user ‘slaveuser’ and provides masteruser GenericAll rights over slaveuser.
For both the users a 4662 is logged whenever there is any interaction with them.
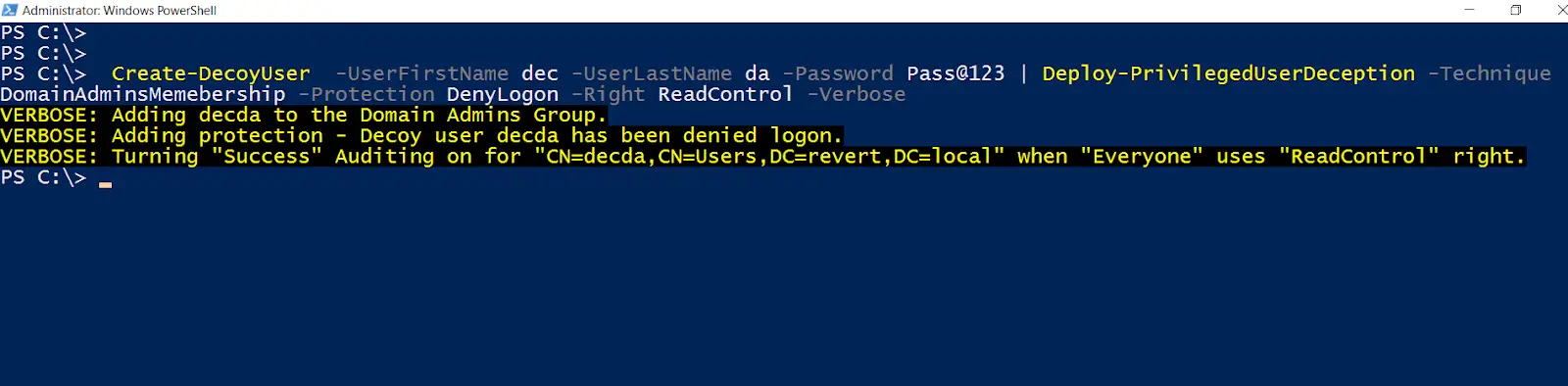
Deploy-PrivilegedUserDeception
This function deploys a decoy user which has high privileges like membership of the Domain Admins group. EXAMPLE
PS C:\> Create-DecoyUser -UserFirstName dec -UserLastName da -Password Pass@123 | Deploy-PrivilegedUserDeception -Technique DomainAdminsMemebership -Protection DenyLogon -Verbose
Create a decoy user named decda and make it a member of the Domain Admins group. As a protection against potential abuse, Deny logon to the user on any machine. Please be aware that if another DA gets compromised the DenyLogon setting can be removed.
If there is any attempt to use the user credentials (password or hashes) a 4768 is logged.
Any enumeration which reads DACL or all properties for the user will result in a 4662 logging.
EXAMPLE
PS C:\> Deploy-PrivilegedUserDeception -DecoySamaccountName decda -Technique DomainAdminsMemebership -Protection LogonWorkStation nonexistent -Verbose
Use existing user decda and make it a member of the Domain Admins group. As a protection against potential abuse set LogonWorkstation for the user to a non-existent machine.
If there is any attempt to use the user credentials (password or hashes) a 4768 is logged.
Any enumeration which reads DACL or all properties for the user will result in a 4662 logging.
Deploy-ComputerDeception
This function sets up auditing when a specified Right is used by a specified principal against the decoy computer object.
PS C:\> Create-DecoyComputer -ComputerName revert-web -Verbose | Deploy-ComputerDeception -PropertyFlag TrustedForDelegation -GUID d07da11f-8a3d-42b6-b0aa-76c962be719a -Verbose
Creates a decoy computer that has Unconstrained Delegation enabled and a 4662 is logged whenever x500uniqueIdentifier – d07da11f-8a3d-42b6-b0aa-76c962be719a property or all the properties of the computer are read.
EXAMPLE
PS C:\> Deploy-ComputerDeception -DecoyComputerName comp1 -PropertyFlag TrustedForDelegation -GUID d07da11f-8a3d-42b6-b0aa-76c962be719a -Verbose
Uses an existing computer object and set Unconstrained Delegation on it. A 4662 is logged whenever x500uniqueIdentifier – d07da11f-8a3d-42b6-b0aa-76c962be719a property or all the properties of the computer are read.
Using a real machine for the decoy is always recommended as it is harder to identify as a decoy.
Deploy-GroupDeception
This function sets up auditing when a specified Right is used by a specifed principal against the decoy group object.
EXAMPLE
PS C:\> Create-DecoyGroup -GroupName ‘Forest Admins’ -Verbose | Deploy-GroupDeception -AddMembers slaveuser -AddToGroup dnsadmins -Right ReadControl -Verbose
Creates a decoy Group ‘Forest Admins’, adds slaveuser as a member and makes the group part of the dnsadmins group. A 4662 is logged whenever DACL or all the properties of the group are read.
Download
git clone https://github.com/samratashok/Deploy-Deception.git
Usage
Import the module in the current PowerShell session.
PS C:\> Import-Module C:\Deploy-Deception\Deploy-Deception.psd1
Use the script with dot sourcing.
PS C:\> . C:\Deploy-Deception\Deploy-Deception.ps1
To get help about any function, use:
PS C:\> Get-Help [functionname] -Full
For example, to see the help about Deploy-UserDeception, use
PS C:\> Get-Help Deploy-UserDeception -Full
Copyright (C) 2018 Nikhil “SamratAshok” Mittal
Source: https://github.com/samratashok/