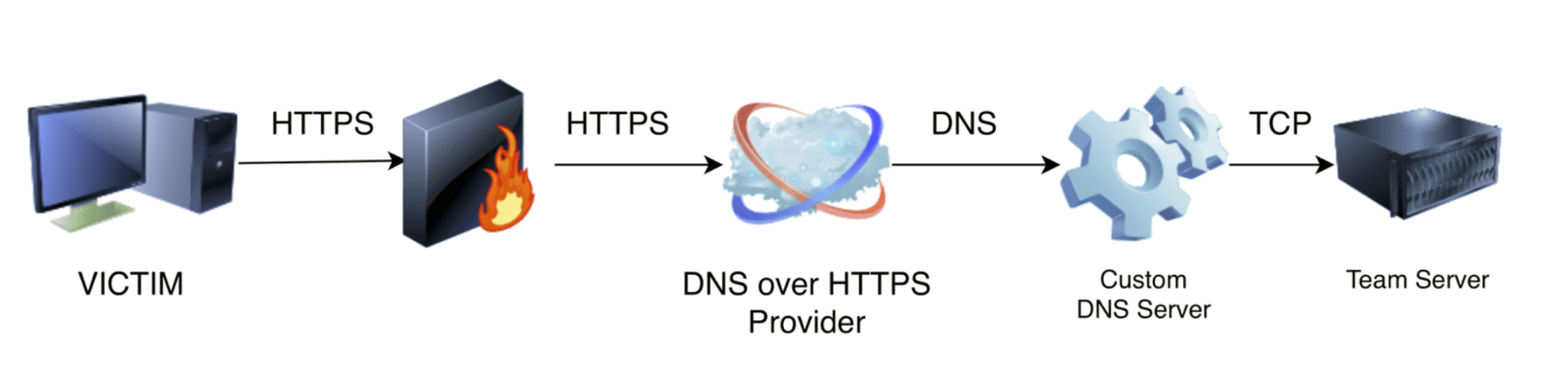
DoHC2
DoHC2 allows the ExternalC2 library from Ryan Hanson (https://github.com/ryhanson/ExternalC2) to be leveraged for command and control (C2) via DNS over HTTPS (DoH). This is built for the popular Adversary Simulation and Red Team Operations Software Cobalt Strike.
This project was released on October 23rd 2018 at Mitre ATT&CKcon.
Slides: Playing Devil’s Advocate to Security Initiatives with ATT&CK
Diagram

Download
git clone https://github.com/SpiderLabs/DoHC2.git
Usage
- Install and launch Cobaltstrike teamserver.
- Launch a beacon_http/beacon_https listener – Gotcha This can be firewalled off but you need this for External C2 to work.
- Load in script ‘external_c2.cna’ to Start ExternalC2 port 2222 (Firewall off).
- Install dependencies for a python3 server.
- Allow port 53/udp to the Internet (or to the DoH provider IP ranges).
- Create an A record on your domain to point to the teamserver/DNS server IP i.e. [A] entry.example.org -> 000.000.000.000
- Create an NS record to point to the A record for send channel (INPUTDOMAIN) i.e. [NS] send.example.org -> entry.example.org.
- Create an NS record to point to the A record for receive channel (OUTPUTDOMAIN) i.e. [NS] receive.example.org -> entry.example.org.
- Change INPUTDOMAIN and OUTPUTDOMAIN in DoHC2.py. Change encryption key/IV – this is used to encrypt the path from Teamserver–>Client Only (Encrypts Stager).
- Launch python3 DNS server.
- Build ExternalC2 library. Change encryption key/IV in DoHChannel.cs to match python3 server.
- Configure and launch DoHC2() as below being sure to set INPUTDOMAIN, OUTPUTDOMAIN and a DoH provider.
Server
Python DNS server based on ACME DNS Server
- This interfaces raw DNS to the Cobalt Strike Teamserver on 127.0.0.1:2222 by default.
- Change INPUTDOMAIN and OUTPUTDOMAIN to be hosts that are NS of the server’s external IP:
pip3 install -r requirements.txt
sudo python3 ./DoHC2.py
Copyright (C) 2018 Trustwave Holdings, Inc.
Source: https://github.com/SpiderLabs/