Dr. ROBOT is a tool for Domain Reconnaissance and Enumeration. By utilizing containers to reduce the overhead of dealing with dependencies, inconsistency across operating systems, and different languages, Dr. ROBOT is built to be highly portable and configurable.
Use Case: Gather as many public-facing servers that a target organization possesses. Querying DNS resources enables us to quickly develop a large list of possible targets that you can run further analysis on.
Note: Dr. ROBOT is not just a one-trick pony. You can easily customize the tools that are used gather information so that you can enjoy the benefits of using latest and greatest along with your battle-tested favorites.
Changelog v1.3
Added
- Threading for Ansible
Changed
- Regex for hostname aggregation
- Relative imports
- CLI Args
- Package layout
- Cleaned up dockerfilesj
Fixed
- Multiprocessing bug when doing aggregation.
- Add port numbers to url for screenshotting later
Install and Run
Inspect
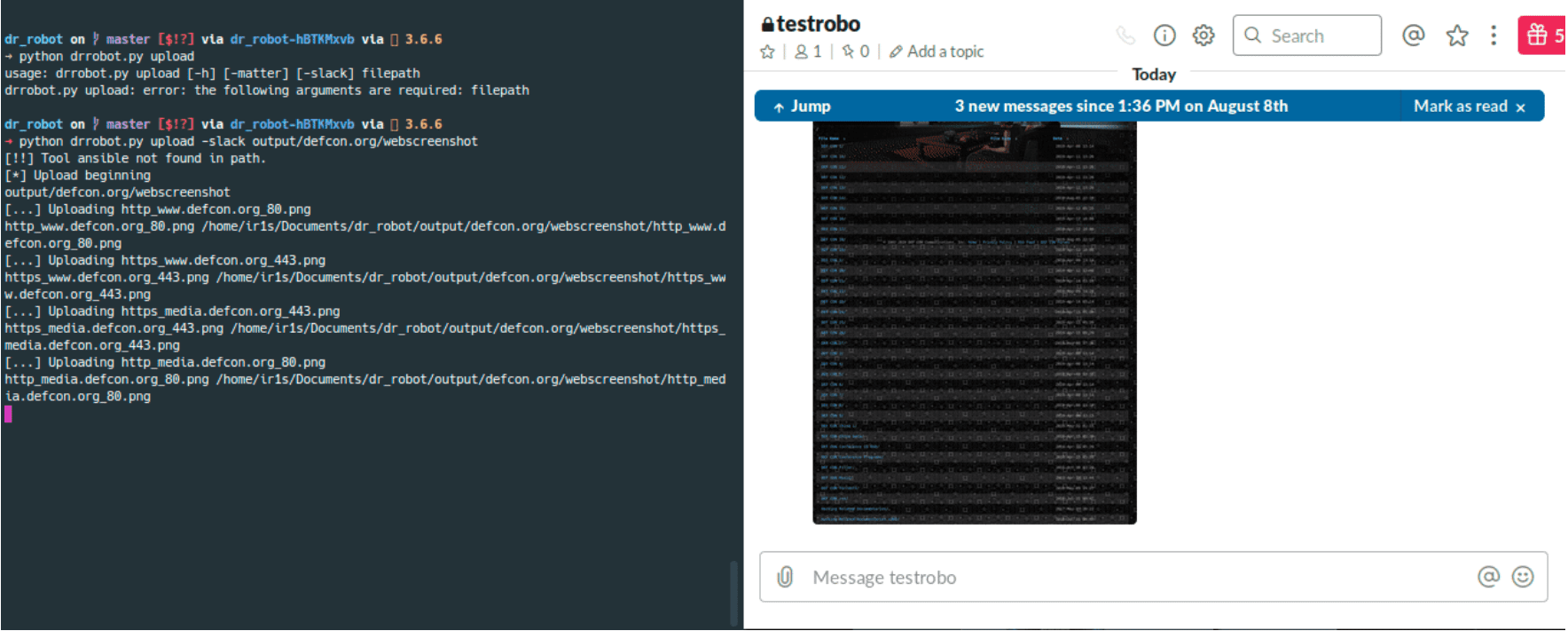
Upload Slack
Dump DB
Output
Serve
Command Examples
- Run gather using Sublist3r and Aquatone and Shodanpython drrobot.py example.domain gather -sub -aqua -shodan
- Run gather using Sublist3r with Proxy
python drrobot.py --proxy http://some.proxy:port example.domain gather -sub
- Run inspect using Eyewitness
python drrobot.py example.domain inspect -eye
- Run inspect using httpscreenshot and grabbing headers
python drrobot.py example.domain inspect -http -headers
- Run upload using Mattermost/Slack
python drrobot.py example.domain upload -matter
Install & Use
Copyright 2018 National Technology & Engineering Solutions of Sandia, LLC (NTESS). Under the terms of Contract DE-NA0003525 with NTESS, the U.S. Government retains certain rights in this software
Copyright (c) 2018 Sandia National Laboratories





