DOME – A subdomain enumeration tool
Dome is a fast and reliable python script that makes active and/or passive scans to obtain subdomains and search for open ports. This tool is recommended for bug bounty hunters and pentester in their reconnaissance phase.
If you want to use more OSINT engines, fill the config.api file with the needed API tokens
Top Features
- Easy to use. Just install the requirements.txt and run
- Active and Passive scan (read above)
- Faster than other subdomain enumeration tools
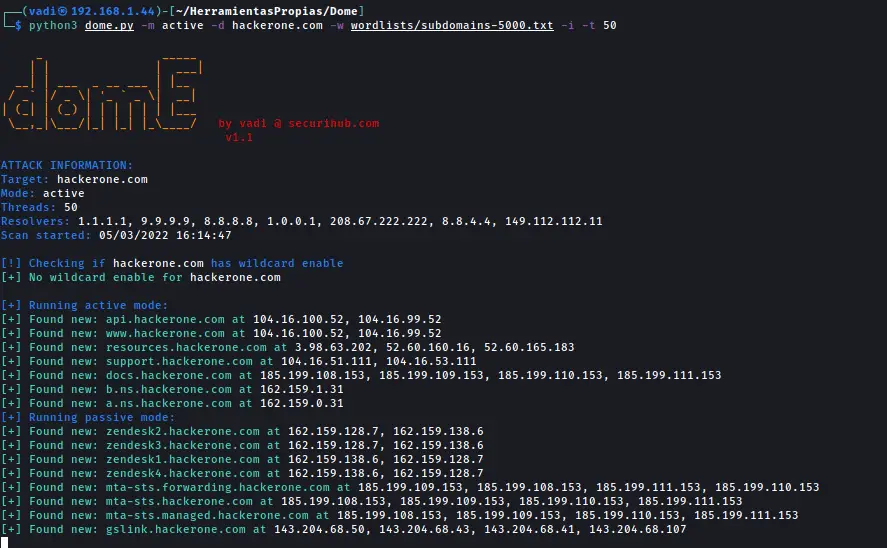
- 7 different resolvers/nameservers including google, Cloudflare (fastest), Quad9, and cisco DNS (use –resolvers filename.txt to use a custom list of resolvers, one per line)
- Up to 21 different OSINT sources
- Subdomains obtained via OSINT are tested to know if they are alive (only in active mode)
- Support for webs that requires an API token
- Detects when api key is no longer working (Other tools just throw an error and stops working)
- Wildcard detection and bypass
- Custom Port scanning and built-in params for Top100, Top1000, and Top Web ports
- Colored and uncolored output for an easy read
- Windows and Python 2/3 support (Python 3 is recommended)
- Highly customizable through arguments
- Scan more than one domain simultaneously
- Possibility to use threads for faster bruteforce scans
- Export output in different formats such as txt, json, html
OSINT Search Engines
Dome uses these web pages to obtain subdomains
Without API:
- AlienVault
- HackerTarget
- RapidDNS
- ThreatMiner
- urlscan.io
- threatcrowd.org
- web.archive.org
- crt.sh
- bufferover.run
- CertSpotter
- Anubis-DB
- Hunt.io
- Sonar
- SiteDossier
- DNSrepo
With API:
- VirusTotal
- Shodan
- Spyse
- SecurityTrails
- PassiveTotal
- BinaryEdge
Passive Mode:
Use OSINT techniques to obtain subdomains from the target. This mode will not make any connection to the target so it is undetectable. The basic use of this mode is:
python dome.py -m passive -d domain
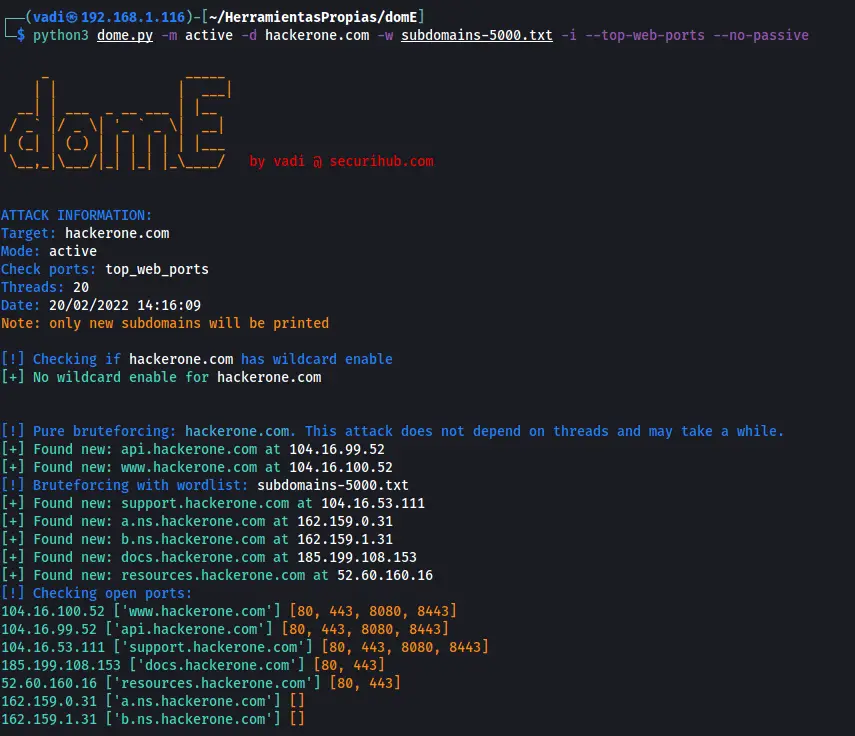
Active Mode:
Perform bruteforce attacks to obtain alive subdomains. There are 2 types of bruteforce:
- Pure Bruteforce: Check subdomains from a.domain.com to zzz.domain.com (26 + 26^2 + 26^3 = 18278 subdomains) this bruteforce can be disabled with -nb, –no-bruteforce
- Wordlist based: Use a custom wordlist provided by the user using the flag -w, –wordlist. If no wordlists are specified, this mode won’t be executed
This mode will also make a passive mode attack but in this case, the connection is tested to ensure the subdomain is still alive. To disable passive scan in active scan mode, use –no-passive flag
The basic use of this mode is:
python dome.py -m active -d domain -w wordlist.txt
Add -p option or a built-it port option (see usage menu) to perform port scanning
python dome.py -m active -d domain -w wordlist.txt -p 80,443,8080
Installation
git clone https://github.com/v4d1/Dome.git
cd Dome
pip install -r requirements.txt
python dome.py –help