DSInternals PowerShell Module and Framework v4.13 Releases
DSInternals PowerShell Module and Framework
The DSInternals project consists of these two parts:
- The DSInternals Framework exposes several internal features of Active Directory and can be used from any .NET application. The codebase has already been integrated into several 3rd party commercial products that use it in scenarios like Active Directory disaster recovery, identity management, cross-forest migrations and password strength auditing.
- The DSInternals PowerShell Module provides easy-to-use cmdlets that are built on top of the Framework. These are the main features:
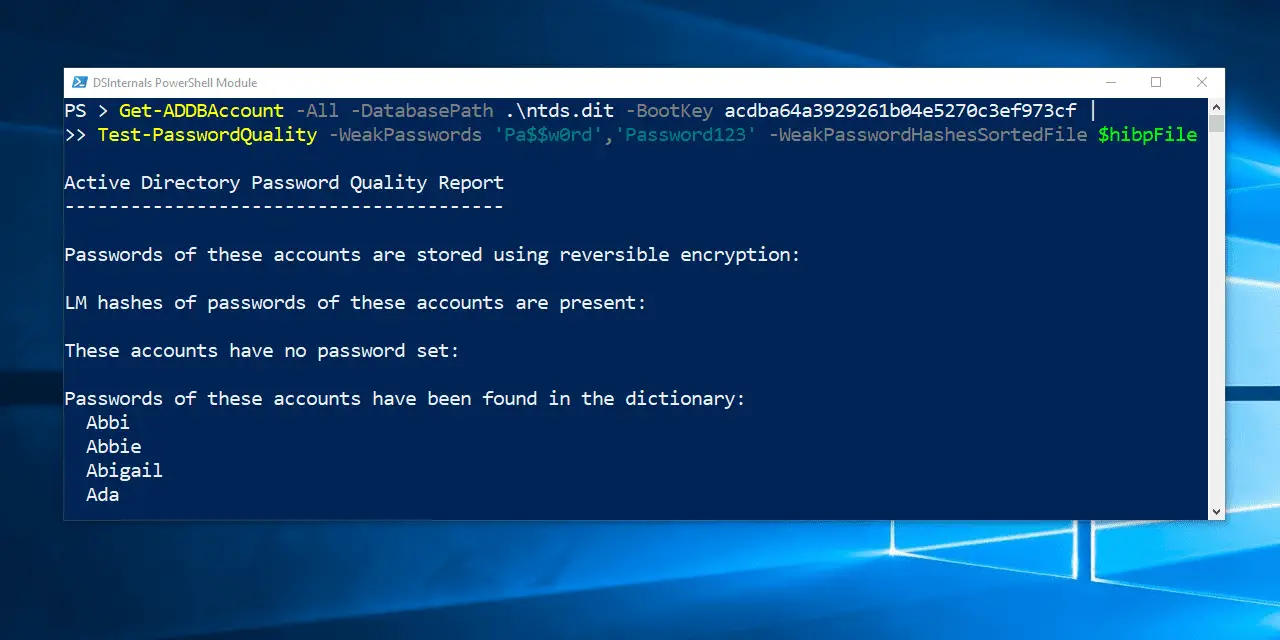
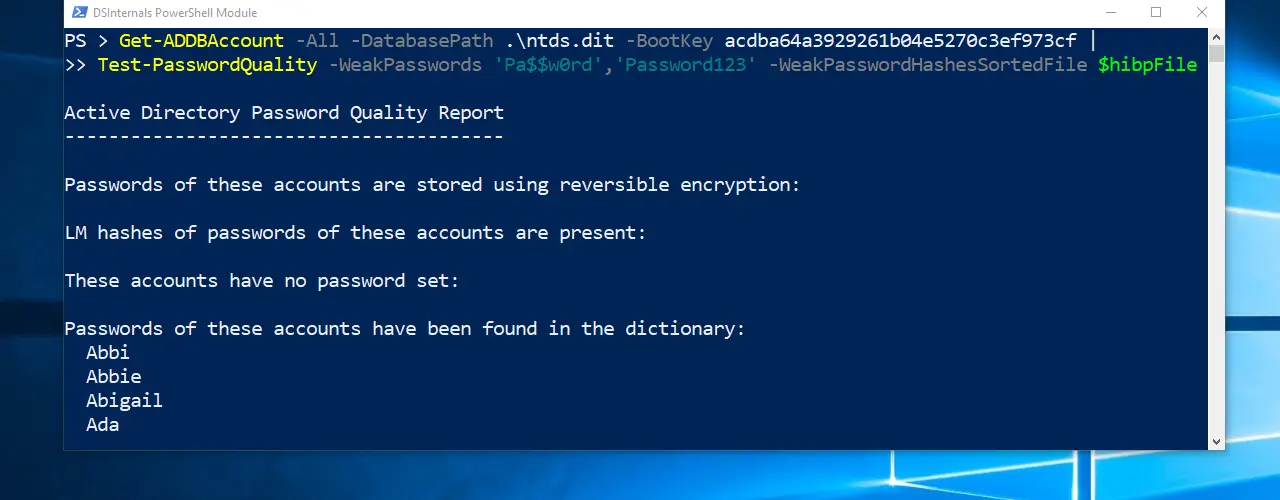
- Active Directory password auditing that discovers accounts sharing the same passwords or having passwords in a public database like HaveIBeenPwned or in a custom dictionary.
- Key credential auditing and generation, including support for NGC, FIDO2 and STK keys. Keys can also be tested against the ROCA vulnerability. New NGC keys can also be registered through the MS-DRSR protocol.
- Bare-metal recovery of domain controllers from just IFM backups (ntds.dit + SYSVOL).
- Offline ntds.dit file manipulation, including hash dumping, password resets, group membership changes, SID History injection and enabling/disabling accounts.
- Online password hash dumping through the Directory Replication Service (DRS) Remote Protocol (MS-DRSR). This feature is commonly called DCSync.
- Domain or local account password hash injection through the Security Account Manager (SAM) Remote Protocol (MS-SAMR) or directly into the database.
- LSA Policy modification through the Local Security Authority (Domain Policy) Remote Protocol (MS-LSAD / LSARPC).
- Extracting credential roaming data and DPAPI domain backup keys, either online through directory replication, LSARPC and offline from ntds.dit.
- Password hash calculation, including NT hash, LM hash and kerberos keys.
Changelog v4.13
Notable Changes
This is a bugfix release. The Set-LsaPolicyInformation cmdlet now generates the UNICODE_STRING structure with the trailing null character, to improve compatibility with NETLOGON. This issue mainly affects the functionality of the New-ADDBRestoreFromMediaScript cmdlet. Thanks, Christoffer Andersson, for reporting this issue. And sorry, Microsoft support escalation engineers, for the trouble this bug has caused.
If you ever restored a DC from an IFM backup using DSInternals, you need to re-run the Set-LsaPolicyInformation cmdlet with the right parameters on that DC.
Installation
Option 1 – Online (PowerShell 5+)
Since PowerShell 5, you can install the DSInternals module directly from the official PowerShell Gallery by running this command:
Install-Module DSInternals
Option 2 – Offline (Windows PowerShell 3+)
- Download the current release from GitHub.
- “Unblock” the ZIP file, using either the Properties dialog or the Unblock-File cmdlet. If you fail to do so, all the extracted DLLs will inherit this attribute and PowerShell will refuse to load them.
- Extract the ZIP file to a temporary location.
- Copy the DSInternals directory to your PowerShell modules directory, e.g. C:\Windows\system32\WindowsPowerShell\v1.0\Modules\DSInternals or C:\Users\John\Documents\WindowsPowerShell\Modules\DSInternals.
- Launch Windows PowerShell.
- (Optional) If you copied the module to a different directory than advised in step 4, you have to manually import it using the Import-Module .\DSInternals\DSInternals.psd1 command.
- Start using the module and don’t be evil.
Copyright (c) 2015 Michael Grafnetter