Execution Flow | Image: CRIL
In a sophisticated attack campaign recently uncovered by Cyble Research and Intelligence Lab (CRIL), digital marketing professionals, particularly those specializing in Meta (Facebook and Instagram) Ads, have become the primary targets of a Vietnamese threat actor. This group has been active since July 2022 and is responsible for the dissemination of malware such as Ducktail and Quasar RAT, using a combination of phishing, sandbox evasion, and privilege escalation techniques to breach systems.
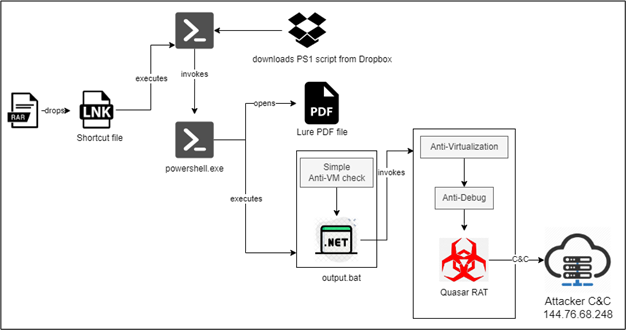
The attack begins with phishing emails containing an archive file, which includes a malicious LNK file disguised as a PDF. Upon opening, the LNK file executes a PowerShell command that downloads additional malicious scripts from an external source, often hosted on platforms like Dropbox. These scripts are heavily obfuscated and encoded to bypass traditional security tools. The attackers use multiple anti-sandboxing and anti-debugging checks to ensure the malware runs only in non-virtualized environments.
Once the system is confirmed to be a real target, the attack proceeds to the final stage. Using hardcoded keys, the scripts decrypt the payload, resulting in the deployment of Quasar RAT, a powerful remote access trojan. This gives the attackers full control over the victim’s system, allowing them to exfiltrate data, steal credentials, and deploy further malware. “The employment of AES encryption for the payload, along with anti-debugging techniques and advanced .NET-based obfuscation, illustrates the attackers’ strong focus on evading traditional security solutions,” the CRIL report notes.
The primary victims of this attack are professionals in the digital marketing, e-commerce, and performance marketing sectors. The attackers have cleverly tailored their phishing lures to these individuals by using job-related documents or projects, often masquerading as professional opportunities. One such lure document, named “PositionApplied_VoyMedia.pdf”, is a fake job application that triggers the malware when opened.

This targeted approach is not a coincidence. The threat actor behind this campaign has a history of targeting digital marketing professionals with information-stealing malware, such as Ducktail. Over time, the group has evolved its tactics, expanding its operations by incorporating Malware-as-a-Service (MaaS) offerings to deliver their payloads in a scalable and versatile manner.
One of the standout features of this campaign is its use of evasion techniques designed to bypass sandbox environments, virtual machines, and security analysis tools. The malware conducts extensive checks to identify if the system is running in a virtualized environment by querying disk drive types, searching for virtual machine-related files, and checking for specific sandbox modules like Sandboxie or Cuckoo. “If any of these checks indicate a virtual environment, the script exits without further execution,” according to the report.
The attackers also employ advanced privilege escalation methods using PowerShell commands and CMSTP to ensure they gain administrative control over the victim’s system. If the malware detects it does not have administrative privileges, it modifies the Process Environment Block (PEB) to mimic Windows Explorer, re-launching itself with elevated privileges. This allows the malware to set up persistence, ensuring it remains on the system even after a reboot.
As CRIL warns, “The modular structure of the attack, with some evasion techniques left unused but ready to deploy based on the target environment, underscores the threat actor’s adaptability and capability to overcome varying levels of defense.” The report further highlights the need for digital marketing professionals and organizations to stay vigilant, as the attackers are likely to continue expanding their operations in the future.
Related Posts:
- New Ducktail Malware Campaign Uses Delphi to Steal Facebook Business Accounts
- Beware of LinkedIn: Ducktail Malware’s Sneaky ZIP Attack Revealed
- Quasar RAT: Stealthy Data Extraction via DLL Sideloading
- ViperSoftX Leverages Deep Learning with Tesseract to Exfiltrate Sensitive Information
- Phishing Campaign Bypasses MFA to Target Meta Business Accounts, Putting Millions at Risk