
d(ockerp)wn – a docker attack tool manager
dwn is a “docker-compose for hackers”. Using a simple YAML “plan” format similar to docker-compose, image names, versions, and volume/port mappings are defined to set up a tool for use.
features
With dwn you can:
- Configure common pentest tools for use in a docker container
- Have context-aware volume mounts
- Dynamically modify port bindings without container restarts
- And more!
Changelog v1.1.1
new
- Add new plans for altdns, arjun, chisel, dnsgen & gau, (7c129f2)
fixes
- Improve error handling when running plans (5ef8529)
Install
pip3 install dwn
Use
pwn is actually really simple. The primary concept is that of “plans” where information about a tool (such as name, version, mounts, and binds) are defined. There are a few built-in plans already available, but you can also roll your own. Without arguments, just running pwn would look like this.
To list the available plans, run dwn plans show.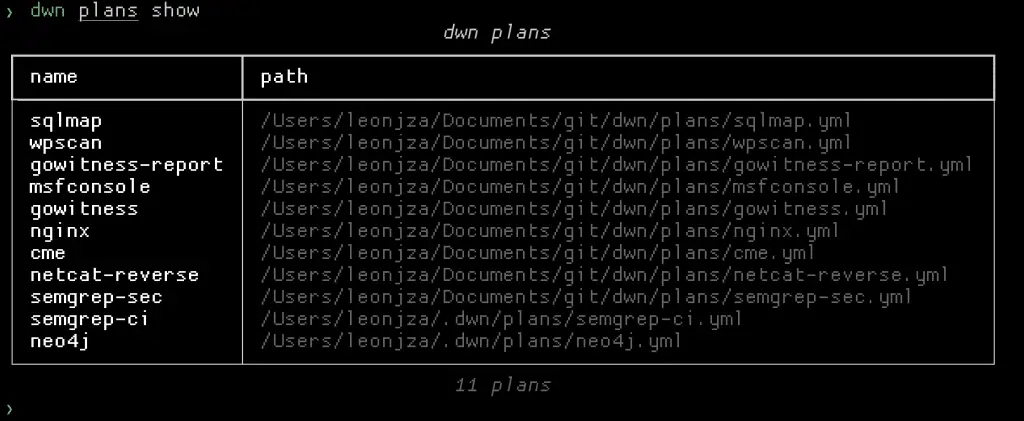
To run a plan such as gowitness screenshotting https://google.com, run dwn run gowitness –disable-db single https://www.google.com. This plan will exit when done, so you don’t have to dwn stop gowitness.
A plan such as netcat-reverse however will stay alive. You can connect to the plans TTY after it is started to interact with any shells you may receive. An example usage would be:
Attaching to the plan (and executing nc -e somewhere else)
You can get a running plan report too
And finally, stop a plan.
Tutorial
Copyright (C) 2020 sensepost