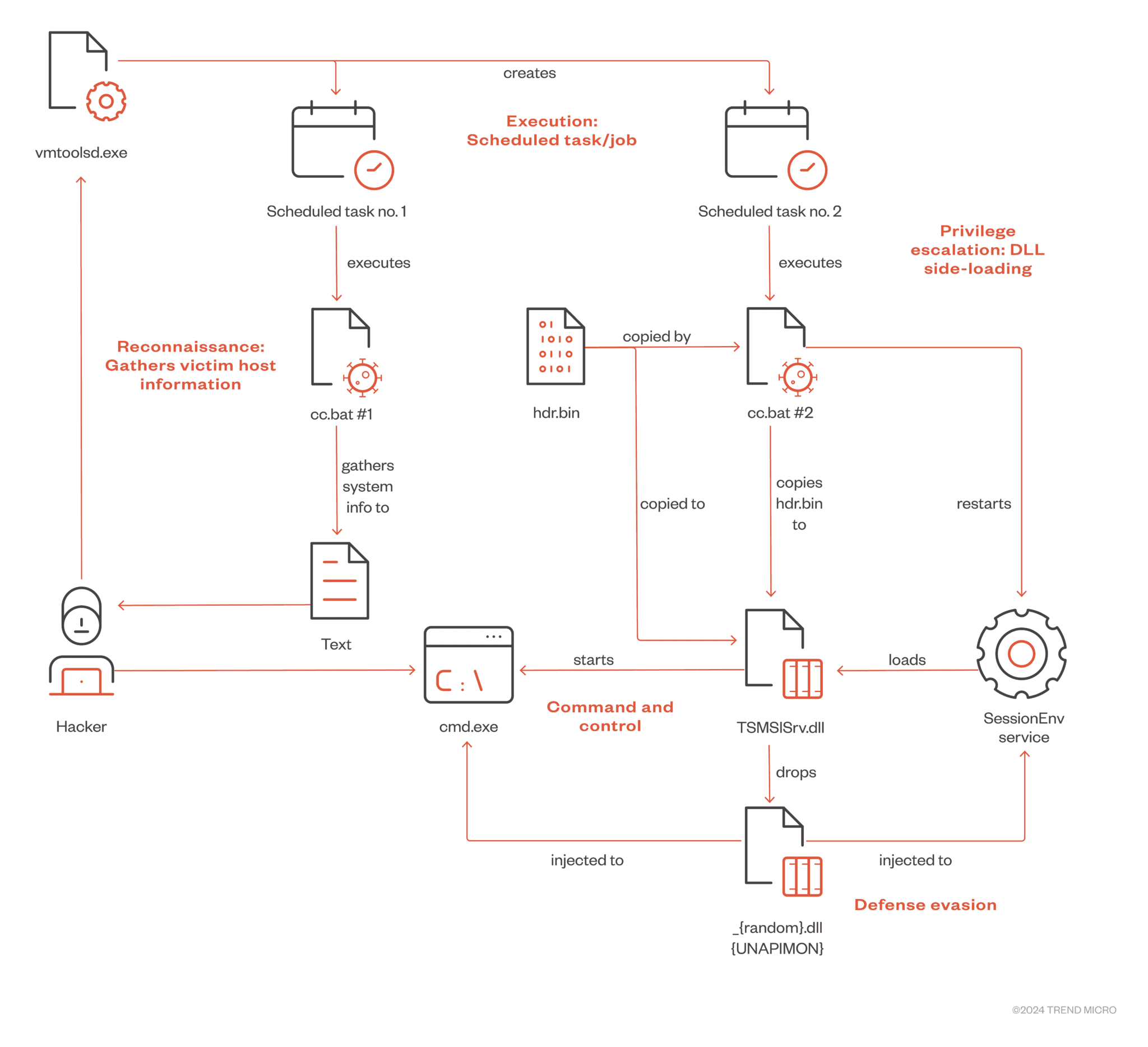
Earth Freybug attack chain | Image: TrendMicro
In a recent cyberespionage campaign attributed to Earth Freybug (also a subset of APT41), security researchers from Trend Micro observed a unique malware, dubbed UNAPIMON, designed to evade detection. Earth Freybug is a long-standing threat group known for espionage and financially motivated attacks across various industries.
Attack Flow Overview

The campaign exhibits tactics similar to those documented by Cybereason. Researchers observed a vmtoolsd.exe process creating a remote scheduled task using schtasks.exe, launching a pre-deployed cc.bat script. This first cc.bat performs system reconnaissance, followed by a second cc.bat that side-loads a malicious DLL. The second cc.bat also drops the UNAPIMON malware, which serves as the backdoor and the focus of this analysis.
UNAPIMON Functionality: A Deeper Dive
UNAPIMON’s core function lies in unhooking critical Windows API functions within child processes, effectively bypassing monitoring mechanisms that security solutions frequently rely upon. It accomplishes this through a calculated sequence:
- Hooking CreateProcessW: UNAPIMON intercepts calls to CreateProcessW, a function responsible for process creation, using the Microsoft Detours library. This allows it to manipulate the creation of child processes.
- Process Suspension: The malware suspends newly created child processes, preventing immediate execution and allowing for under-the-radar modifications.
- DLL Validation: UNAPIMON meticulously examines loaded DLLs within the child process. It creates local copies of these DLLs, ensuring a baseline for comparison and enabling targeted unhooking.
- Unhooking: The malware identifies and reverts any modifications (“hooks”) placed on exported API functions. This restores the original code, rendering the APIs undetectable by standard monitoring tools.
- Stealth Execution: With API hooks removed, malicious child processes can operate with significantly reduced visibility.
UNAPIMON, while straightforward in its design, employs a strategic hooking mechanism to intercept and manipulate system calls, effectively allowing malicious processes to execute undetected. This malware not only demonstrates Earth Freybug’s technical prowess but also highlights the potential for even basic tools and libraries to be weaponized in the hands of skilled adversaries.
Implications: The Risk of Undetected Activity
UNAPIMON’s anti-monitoring capabilities pose a significant threat to organizations. By allowing malicious processes to evade detection, threat actors can maintain extended persistence within a compromised environment. This increases the risk of data exfiltration, lateral movement, and the execution of further attacks.
Security Recommendations
- Credential Management: Enforce strict credential management practices, including regular password rotation, limited administrator accounts, and activity logging.
- Principle of Least Privilege: Grant users and processes only the necessary permissions to reduce potential attack surfaces.
- Vigilance: Security teams must remain vigilant against both advanced and seemingly simple techniques that can be combined for sophisticated attacks.
Conclusion
Earth Freybug continues to refine its methods for successful cyberespionage. Organizations must prioritize robust security practices and ongoing threat intelligence to defend against these evolving threats.