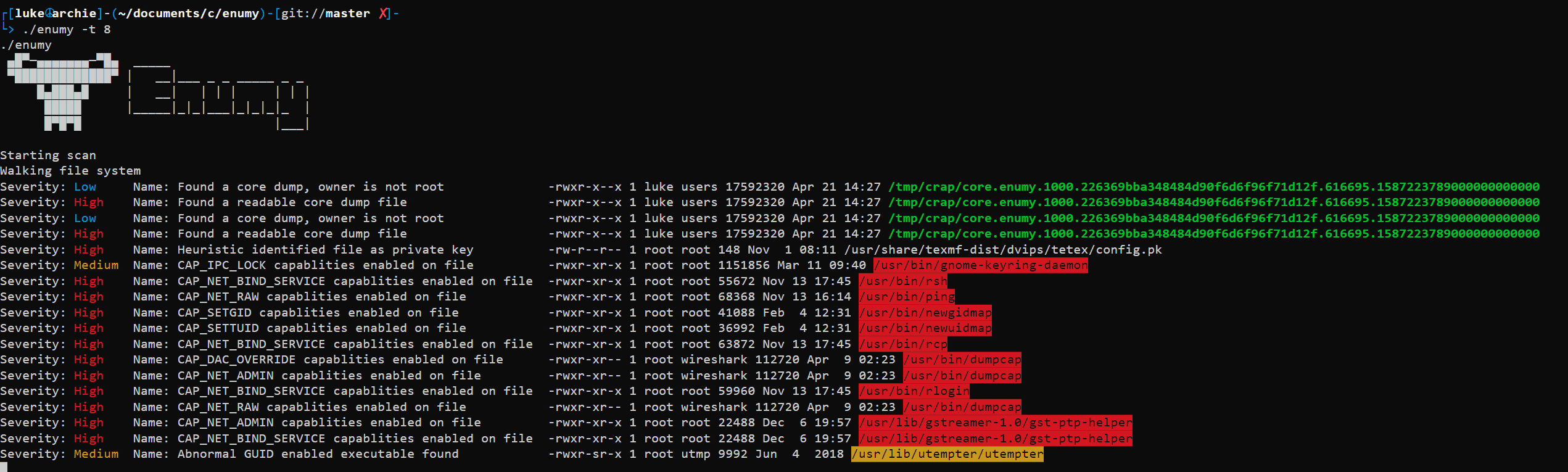
enumy
Enumy is an ultra-fast portable executable that you drop on target Linux machine during a pentest or CTF in the post-exploitation phase. Running enumy will enumerate the box for common security vulnerabilities.
Who Should Use Enumy
- Pentester can run on a target machine raisable issues for their reports.
- CTF players can use it to identify things that they might have missed.
- People, who are curious to know how many issues enumy finds on their local machine?
Scan types
Kernel Exploit Surgestor
This scan will check the kernel versions to see if it matches any kernel versions with known exploits.
SUID GUID Scan
The idea of this scan is to enumerate the system looking for SUID/GUID binaries that are abnormal or have weak permissions that can be exploited.
File Capabilities Scan
Recently the Linux kernel supports capabilities, this is the preferred way to give a file a subset of root’s powers to mitigate risk. Although this is a much safer way of doing things, if you’re lucky enough to find abnormal capabilities set on a file then it’s quite possible that you can exploit the executable to gain higher access. Enumy will check the capabilities set on all executable files on the system.
Interesting Files Scan
This is more of a generic scan that will try and categorize a file-based off its contents, file extension, and file name. Enumy will look for files such as private keys, passwords, and backup files.
Coredump Scan
Coredump files are a type of ELF file that contains a process’s address space when the program terminates unexpectedly. Now imagine if this process’s memory was readable and contained sensitive information. Or even more exciting, this coredump could be for an internally developed tool that segfaulted, allowing you to develop a zero-day.
Breakout Binary Scan
Some files should never have SUID bit set, it is quite common for a lazy sysadmin to give a file like a docker, ionice, hexdump SUID make a bash script work or there life easier. This scan tries to find some known bad SUID binaries.
Sysctl Parameter Hardening
Sysctl is used to modify kernel parameters at runtime. It’s also possible to query these kernel parameters and check to see if important security measures like ASLR are enabled.
Living Off The Land scan
Living off the land is a technique used where attackers weaponize what’s already on the system. They do this to remain stealthy amongst other reasons. This scan would enumerate the files that an attacker would be looking for.
Dynamic Shared Object Injection Scan
This scan will parse ELF files for their dependencies. If we have to write access to any of these dependencies or write access to any DT_RPATH and DT_RUNPATH values then we can create our own malicious shared object into that executable potentially compromising the system.
SSH Misconfiguration Scan
SSH is one of the most common services that you will find in the real world. It’s also quite easy to misconfigure it. This scan will check to see if it can be hardened in any way.
Current User Scan
The current user scan just parses /etc/passwd. With this information, we find root accounts, unprotected and missing home directories, etc.
Permissions Scan
This scan is going to find files that are globally writable files, uneven permissions, and unowned files. See here for inspiration of the scan.
File System Scan
This scan would be useful for people trying to harden their Linux machines. It will highlight issues such as unencrypted drives and insecure mounting configurations.
Changelog v1.3.1
-
Merge pull request #28 from johnthesecond/fix_issue_1
Fix issue 1
Download
Use
./enumy
Copyright (c) 2020 luke-goddard
Source: https://github.com/luke-goddard/