Evasor
The Evasor is an automated security assessment tool which locates existing executables on the Windows operating system that can be used to bypass any Application Control rules. It is very easy to use, quick, saves time, and fully automated which generates for you a report including description, screenshots and mitigations suggestions, suites for both blue and red teams in the assessment of a post-exploitation phase.
Usage instructions
Download the Evasor project and compile it. Verify to exclude from the project the App.config file from the reference tree.
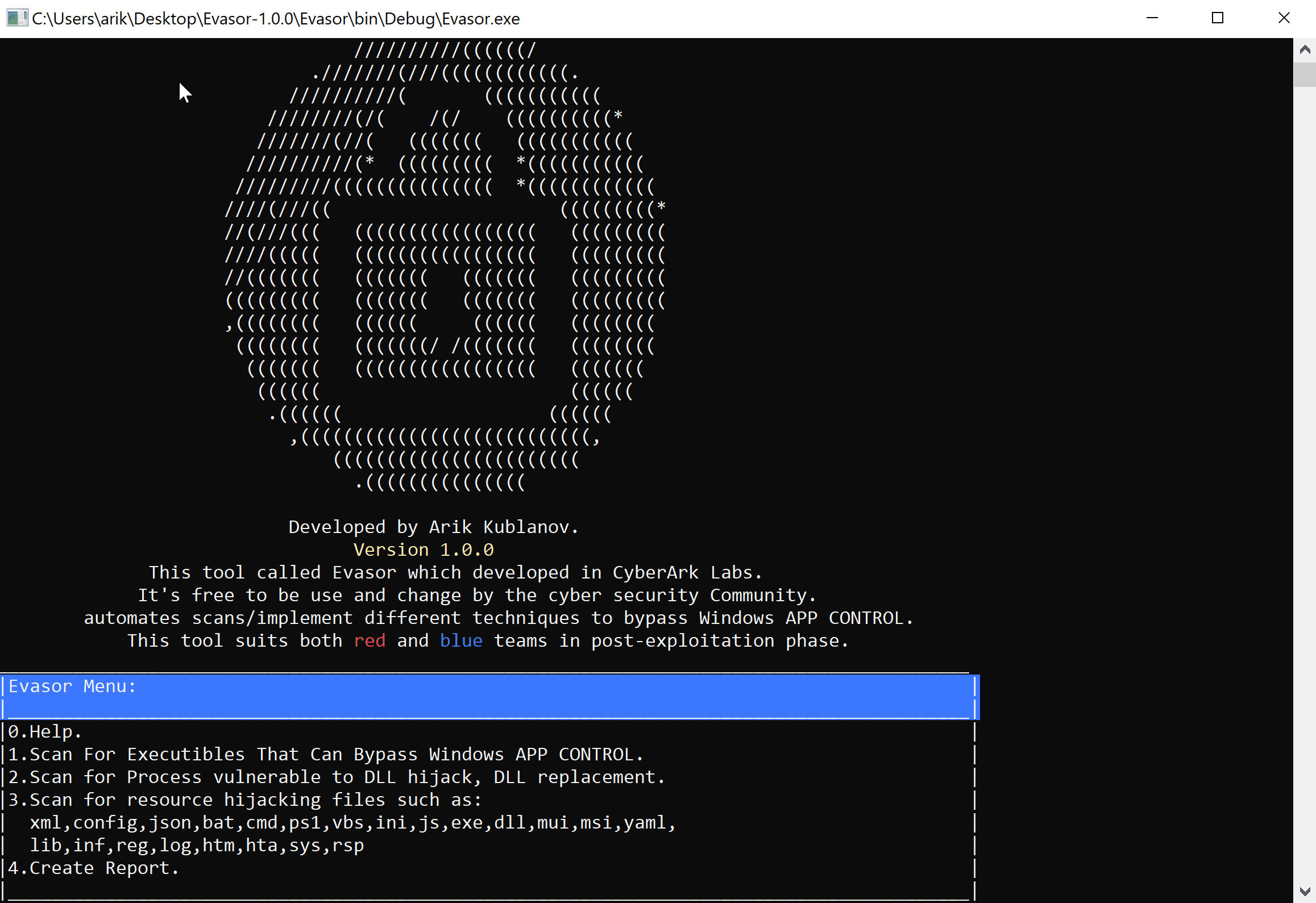
run Evasor.exe from the bin folder. Choose your numeric option from the following:
- Locating executable files that can be used to bypass the Application Control!
- Retrieving all running processes relative paths
- Checking every process (executable file) if it vulnerable to DLL Injection by:
- Running “MavInject” Microsoft component from path C:\Windows\System32\mavinject.exe with default parameters.
- Checking the exit code of the MavInject execution, if the process exited normally it means that the process is vulnerable to DLL Injection and can be used to bypass the Application Control.
- Locating processes that vulnerable to DLL Hijacking!
- Retrieving the all running processes
- For each running Process:
- Retrieving the loaded process modules
- Checking if there is permission to write data into the directory of the working process by creating an empty file with the name of the loaded module (DLL) or overwriting an existing module file on the working process directory.
- If the write operation succeeds – it seems that the process is vulnerable to DLL Hijacking.
- Locating for potential hijackable resource files
- Searching for specific files on the computer by their extension.
- Trying to replace that files to another place in order to validate that the file can be replaceable and finally, potentially vulnerable to Resource Hijacking.
- Extensions: xml,config,json,bat,cmd,ps1,vbs,ini,js,exe,dll,msi,yaml,lib,inf,reg,log,htm,hta,sys,rsp
- Generating an automatic assessment report word document includes a description of tests and screenshots taken.
Download
Copyright (c) 2020 CyberArk Software Ltd. All rights reserved.