EVILRDP – More control over RDP
The evil twin of aardwolfgui using the aardwolf RDP client library that gives you extended control over the target and additional scripting capabilities from the command line.

Features
- Control the mouse and keyboard in an automated way from the command line
- Control the clipboard in an automated way from the command line
- Spawn a SOCKS proxy from the client that channels network communication to the target via RDP
- Execute arbitrary SHELL and PowerShell commands on the target without uploading files
- Upload and download files to/from the target even when file transfers are disabled on the target
Scripts
- evilrdp – GUI + command line RDP client
Install
git clone https://github.com/skelsec/evilrdp.git
pip3 install .
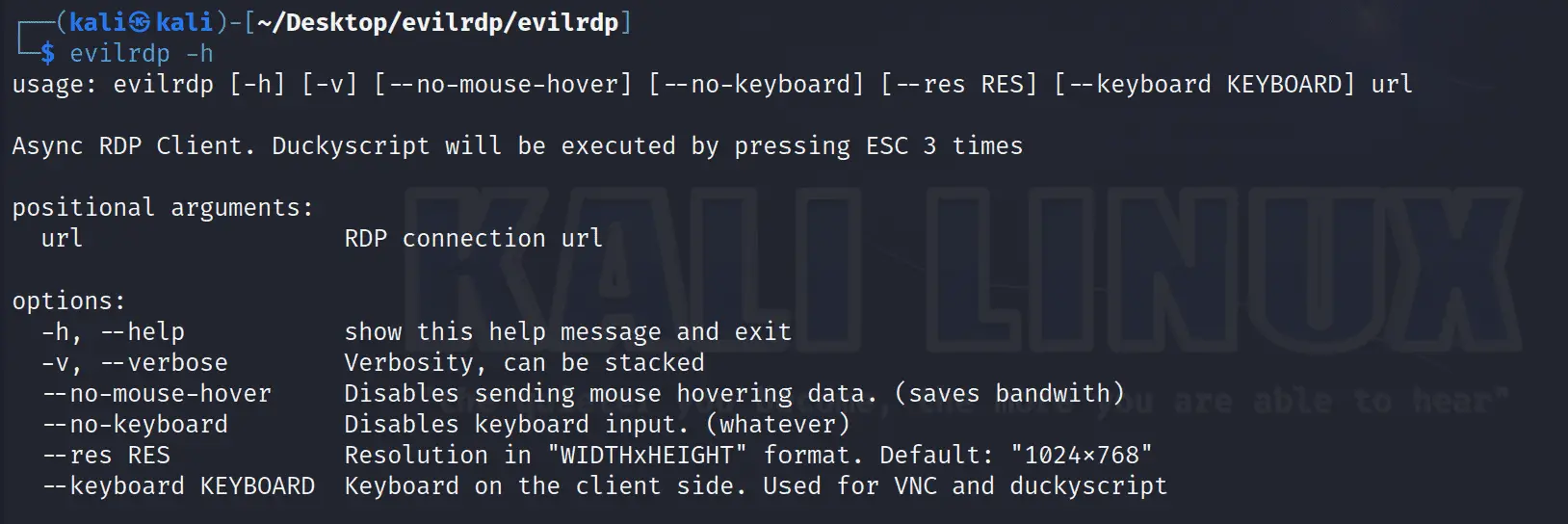
Usage
After installing this package, a new executable will be available called evilrdp. Upon making a successful connection to the target you’ll be presented with a GUI just like a normal RDP client as well as the command line from where you executed evilrdp will turn into an interactive shell. There will be two groups of commands available to you, as follows:
- Commands that can be issued at any time. This includes commands like:
- mousemove
- rightclick
- doubleclick
- type
- typefile
- return/enter
- invokerun
- clipboardset
- clipboardsetfile
- clipboardget
- powershell
- screenshot
- Commands that only work when the PSCMD channel is established
- pscmdchannel – Changes the PSCMD channel name from the default. Use this when you change the channelname in agent script file
- startpscmd – This tries to automatically start the remote agent which allows further commands to be used
- pscmd – Executes a powershell command
- getfile – Downloads remote file
- shell – Executes a shell command
- socksproxy – Starts a SOCKS4a/5 proxy
As it is with all things RDP, automatic command execution doesn’t always work mostly because of timing issues therefore the startpscmd might need to be used 2 times, OR you might need to start the PSCMD channel manually.
When PSCMD channel starts, you’ll get a notification in your client shell.
URL format
As usual, the scripts take the target/scredentials in URL format. Below some examples
- rdp+kerberos-password://TEST\Administrator:Passw0rd!1@win2016ad.test.corp/?dc=10.10.10.2&proxytype=socks5&proxyhost=127.0.0.1&proxyport=1080
CredSSP (aka HYBRID) auth using Kerberos auth + password via socks5 to win2016ad.test.corp, the domain controller (kerberos service) is at 10.10.10.2. The socks proxy is on 127.0.0.1:1080 - rdp+ntlm-password://TEST\Administrator:Passw0rd!1@10.10.10.103
CredSSP (aka HYBRID) auth using NTLM auth + password connecting to RDP server 10.10.10.103 - rdp+ntlm-password://TEST\Administrator:<NThash>@10.10.10.103
CredSSP (aka HYBRID) auth using Pass-the-Hash (NTLM) auth connecting to the RDP server 10.10.10.103 - rdp+plain://Administrator:Passw0rd!1@10.10.10.103
Plain authentication (No SSL, encryption is RC4) using a password connecting to RDP server 10.10.10.103
Source: https://github.com/skelsec/