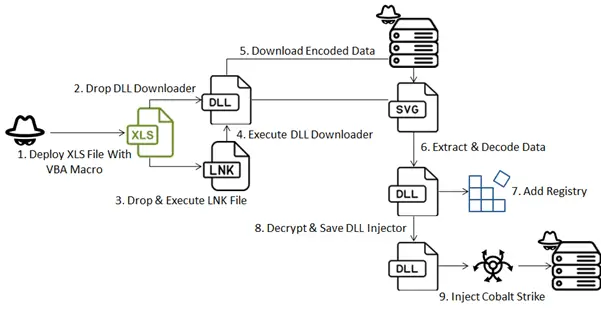
Attack flow
FortiGuard Labs has recently unveiled a sophisticated cyberattack that leverages an Excel file embedded with a VBA macro to deploy a DLL file. This multi-stage malware strategy ultimately delivers the notorious “Cobalt Strike” payload, establishing communication with a command and control (C2) server. The attack employs various evasion techniques to ensure successful payload delivery.

The attack begins with a seemingly benign Excel file containing Ukrainian language elements, designed to deceive victims into enabling macros. Upon activation, the file reveals its true nature, masquerading as budgetary calculations for military units – a tactic aimed at further luring targets into a false sense of security.
The attack’s complexity doesn’t end there. It employs a range of evasion techniques, including encoded strings within the VBA macro and an obfuscated DLL downloader, designed to bypass conventional security measures. This multi-stage delivery mechanism hinders detection and analysis, allowing the threat to remain undetected for longer periods.
The ultimate payload of this attack is Cobalt Strike, a powerful toolkit favored by both red teams and malicious actors. Cobalt Strike provides attackers with extensive capabilities, including remote access, data exfiltration, and lateral movement within compromised networks.
Ukraine has been a significant target for cyberattacks over the past few years due to its geopolitical situation. The history of these attacks reveals a pattern of increasing complexity and frequency, particularly during periods of geopolitical tension. For instance, in 2022, FortiGuard Labs reported a campaign using a malicious Excel document themed around the Ukrainian military to deliver a multi-stage Cobalt Strike loader. In 2023, Ukraine’s Computer Emergency Response Team (CERT-UA) disclosed that UAC-0057 was involved in an attack using a malicious XLS file containing a macro and a lure image to deploy PicassoLoader and Cobalt Strike Beacon on compromised systems.
This attack serves as a stark reminder of the evolving threat landscape and the need for proactive cybersecurity measures. Organizations and individuals must remain vigilant and adopt a defense-in-depth approach to safeguard their digital assets. As cyber warfare tactics continue to advance, it is imperative to stay one step ahead of malicious actors and adapt security strategies accordingly.