Argo Workflows, a widely-used open-source tool for orchestrating workflows in Kubernetes, has become a valuable asset for cloud-native automation. However, recent findings by Yali Mintus, a Cloud Security Researcher at E.V.A Information Security, reveal alarming vulnerabilities stemming from misconfigurations in Argo Workflows instances. These flaws could allow attackers to compromise entire Kubernetes clusters.
Over the course of a year, E.V.A Information Security identified recurring misconfigurations in Argo Workflows during cloud security penetration testing engagements. “These misconfigurations have created exploitable conditions, allowing us to compromise clusters, escalate privileges, and conduct lateral movements – ultimately gaining Kubernetes Cluster-Admin access,” writes Mintus in the report.
he research highlights key factors that make Argo Workflows an enticing target:
- Default Unauthenticated Access: Many instances, deployed using the QuickStart manifest, lack authentication, allowing unrestricted access to workflows.
- Extensive Permissions: Misconfigured deployments often grant excessive permissions, enabling attackers to execute code with privileged roles.
- Exposure of Secrets: Secrets embedded within workflows can be exploited to access sensitive resources.
- Lateral Movement Potential: Workflows operating across interconnected networks provide opportunities for attackers to pivot into other organizational systems.
A survey conducted in November 2024 revealed approximately 3,000 publicly accessible Argo Workflows instances, exposing organizations to significant risk.
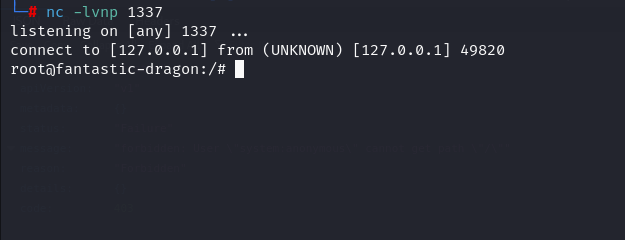
E.V.A’s team demonstrated how attackers could leverage these vulnerabilities. By identifying misconfigured instances using tools like Shodan and querying unauthenticated APIs, they gained full access to workflows. In one scenario, a malicious workflow was crafted to deploy a reverse shell within the Kubernetes environment. “This default configuration significantly increases the attack surface, as an unauthenticated attacker can exploit these privileges to execute arbitrary workflows and potentially compromise the entire Kubernetes environment,” the report states.
Organizations can protect themselves by adopting robust security measures:
- Enable Authentication: Implement proper authentication using Client Mode or Single Sign-On (SSO) to restrict unauthorized access.
- Scope Permissions: Limit ClusterRole permissions to specific namespaces, reducing the impact of potential compromises.
- Monitor Exposed Instances: Regularly scan for publicly accessible instances and enforce secure deployment practices.
“By restricting permissions to only the necessary namespaces, organizations can limit the potential attack surface and reduce the impact of a compromised Argo Workflows instance,” advises Mintus.
Related Posts:
- CVE-2024-31989: Critical Argo CD Flaw Exposes Kubernetes Clusters to Takeover
- Argo CD Users Beware: CVE-2024-28175 (CVSS 9.0) – Critical XSS Vulnerability Exposed
- CVE-2023-40029 in Argo CD lets attackers view the full contents of a cluster secret