
ExtractBitlockerKeys
A system administration or post-exploitation script to automatically extract the bitlocker recovery keys from a domain.
Features
- Automatically gets the list of all computers from the domain controller’s LDAP.
- Multithreaded connections to extract Bitlocker keys from LDAP.
- Iterate on LDAP result pages to get every computer of the domain, no matter the size.
⚠️ Please do not store this backup in an online SMB share of the domain. You should prefer to print it and store it physically in a locked safe.
- Export results in JSON with Computer FQDN, Domain, Recovery Key, Volume GUID, Created At, and Organizational Units.
- Export results in XLSX with Computer FQDN, Domain, Recovery Key, Volume GUID, Created At, and Organizational Units.
- Export results in SQLITE3 with Computer FQDN, Domain, Recovery Key, Volume GUID, Created At, and Organizational Units.
Download
git clone https://github.com/p0dalirius/ExtractBitlockerKeys.git
Use

Demonstration from Linux in Python
To extract Bitlocker recovery keys from all the computers of the domain domain.local you can use this command:
./ExtractBitlockerKeys.py -d ‘domain.local’ -u ‘Administrator’ -p ‘Podalirius123!’ –dc-ip 192.168.1.101

Demonstration from Windows in Powershell
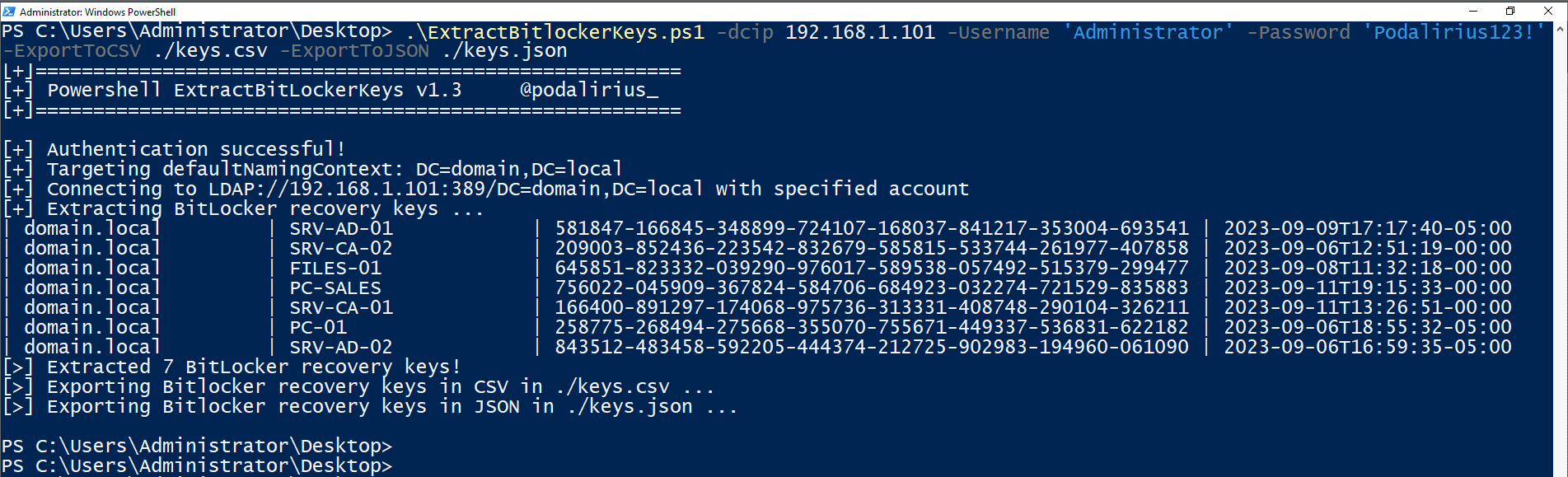
To extract Bitlocker recovery keys from all the computers of the domain domain.local you can use this command:
You will get the following output:
Source: https://github.com/p0dalirius/