
A new report from ReversingLabs has uncovered a sophisticated cyber campaign targeting developers, using fake recruiter tactics to deliver malicious Python packages. Linked to North Korea’s Lazarus Group, this campaign builds on previous attacks first identified in 2023, known as VMConnect.
According to ReversingLabs researchers, the attack works by luring developers into job interviews for non-existent positions at major financial firms. In the course of these fake interviews, candidates are asked to complete a coding test. These coding assignments, disguised as Python skill assessments, contain malicious code hidden within the Python packages.
The malware-laden tests are distributed through GitHub repositories and other public platforms, often named something innocuous like Python_Skill_Test.zip or PasswordManager.zip. These archives contain detailed README files instructing the developer to execute the code and fix supposed bugs. By doing so, the developer unknowingly runs the malicious code on their system, opening the door to further exploitation.
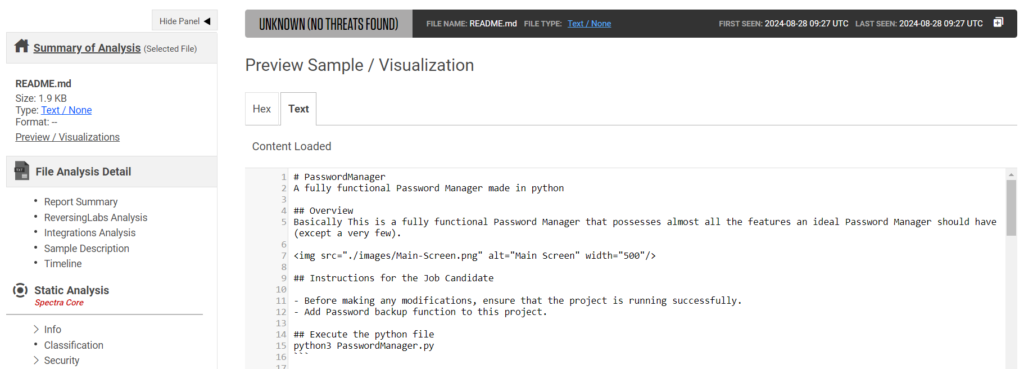
The malicious code embedded in these packages is well-concealed. The ReversingLabs team identified that the malware often hides in compiled Python files (PYC), making it harder for traditional scanning tools to detect. While the plain text Python files also contain malicious code, the malware is executed from the cached PYC files, which bypass typical scrutiny and execute faster.
Once executed, the malware acts as a downloader, sending Base64-encoded commands to a command-and-control (C2) server, receiving additional payloads that can range from backdoors to information stealers. These secondary payloads allow attackers to further compromise the developer’s system, exfiltrating data or gaining persistent access.
An interesting aspect of this campaign is how the attackers pose as employees of well-known financial institutions such as Capital One. Victims are contacted via LinkedIn, where attackers pretend to be recruiters from these firms. After a brief interaction, the targets are provided with a link to a GitHub repository or a zip file, containing the malicious Python coding tests.
This approach exploits the trust placed in reputable brands and taps into the job-seeking behaviors of developers. The urgency in completing these coding assessments often leads developers to bypass security checks, playing right into the attackers’ hands.
ReversingLabs has confirmed that this campaign is still active. In fact, on July 31, 2024, they identified a newly published GitHub repository containing similar malicious code to what had been found earlier in the VMConnect campaign. This suggests that the Lazarus Group is continuing to refine and reuse its tactics, targeting developers across various industries.
The long-standing nature of this campaign, dating back to early 2023, highlights the persistent threat that North Korean state-sponsored groups pose to organizations worldwide. By targeting developers, these groups can infiltrate sensitive development environments and leverage the developers’ access to further compromise high-value systems.
This campaign underlines the need for increased vigilance within the developer community. To mitigate the risk of falling victim to such attacks, developers should:
- Verify the source: Always confirm the legitimacy of coding tests, especially if they are shared through non-official channels like GitHub or LinkedIn.
- Review code thoroughly: Before executing any external code on your machine, perform a comprehensive review, especially when dealing with compiled Python files or complex code structures.
- Monitor network activity: Use advanced threat detection platforms that can spot suspicious activity, such as abnormal HTTP POST requests or connections to unfamiliar C2 servers.
For organizations, the focus should be on educating developers about these tactics and ensuring they are aware of the potential risks associated with accepting unsolicited coding tests or projects from unknown sources.
To read the full report, visit the ReversingLabs blog and stay updated on the latest developments in this ongoing cyber campaign.
Related Posts:
- Developers Beware: Supply Chain Attacks Target Visual Studio Code Extensions
- Temptation from Money: Lazarus APT extended to cryptocurrencies
- Malicious NuGet Campaign Exploits Homoglyphs and Code Injection to Fool Developers
- North Korea’s Lazarus Group: A Persistent Threat to the Defense Sector