ForgeCert
ForgeCert uses the BouncyCastle C# API and a stolen Certificate Authority (CA) certificate + private key to forge certificates for arbitrary users capable of authentication to Active Directory.
This attack is codified as DPERSIST1 in our “Certified Pre-Owned” whitepaper. This codebase was released ~45 days after the whitepaper was published.
Background
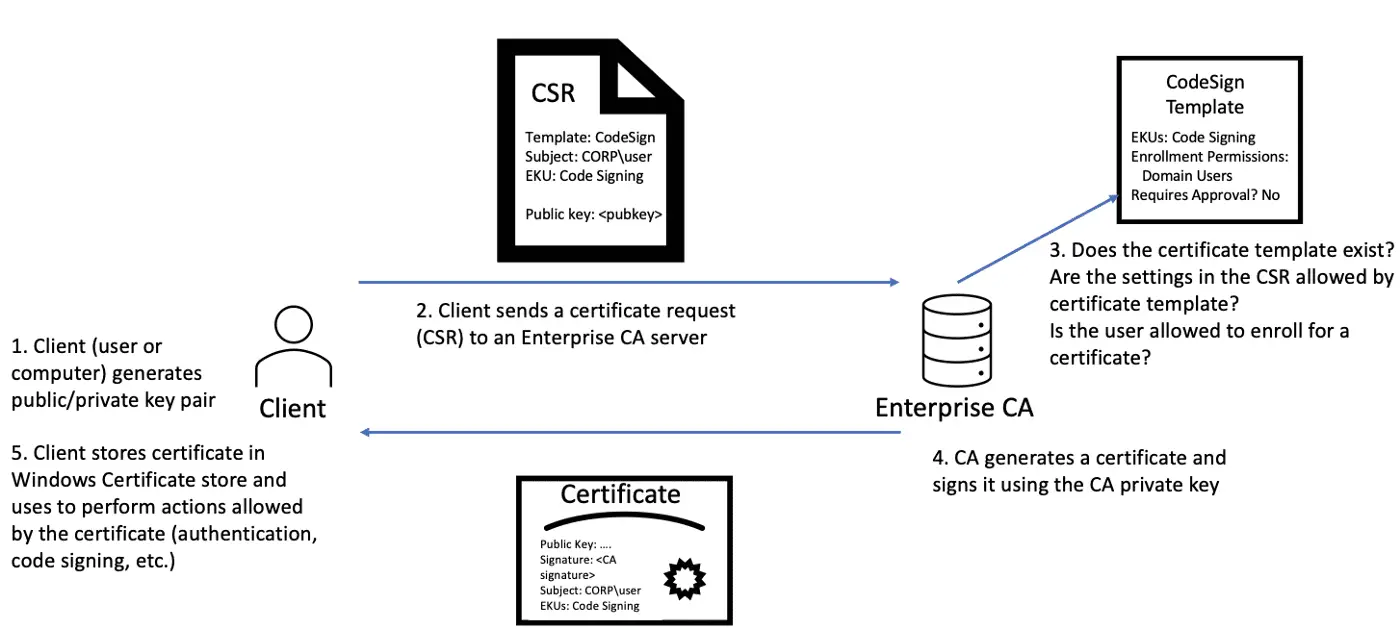
As described in the Background and Forging Certificates with Stolen CA Certificates – DPERSIST1 sections of our whitepaper, the private key for a Certificate Authority’s CA certificate is protected on the CA server either via DPAPI or hardware (HSM/TPM). Additionally, the certificate (sans private key) is published to the NTAuthCertificates forest object, which defines CA certificates that enable authentication to AD. Put together, a CA whose certificate is present in NTAuthCertificates uses its private key to sign certificate signing requests (CSRs) from requesting clients. This graphic summarizes the process:
The security of the CA’s private key is paramount. As mentioned, if the private key is not protected by a hardware solution like a TPM or an HSM, the key will be encrypted with the Data Protection API (DPAPI) and stored on a disk on the CA server. If an attacker is able to compromise a CA server, they can extract the private key for any CA certificate not protected by hardware by using @gentilkiwi‘s Mimikatz or GhostPack’s SharpDPAPI project. THEFT3 in the whitepaper describes this process for machine certificates.
Because the only key material used to sign issued certificates is the CA’s private key, if an attacker steals such a key (for a certificate in NTAuthCertificates) they can forge certificates capable of domain authentication. These forged certificates can be for any principal in the domain (though the account needs to be “active” for authentication to be possible, so accounts like krbtgt will not work) and the certificates will be valid for as long as the CA certificate is valid (usually 5 years by default but can be set to be longer).
Also, as these certificates are not a product of the normal issuance process, the CA is not aware that they were created. Thus, the certificates cannot be revoked.
Note: the private key for ANY CA certificate in NTAuthCertificates (root or subordinate CA) can be used to forge certificates capable of authentication in the forest. If the certificate/key is from a subordinate CA, a legitimate CRL for verification of the certificate chain must be supplied.
ForgeCert uses the BouncyCastle’s X509V3CertificateGenerator to perform the forgeries.
Install & Use
- @tifkin_ is the primary author of ForgeCert.
- @tifkin_ and @harmj0y are the primary authors of the associated Active Directory Certificate Service research (blog and whitepaper).