First pop-up warning | Image: Check Point
Foxit Software, a leading provider of PDF solutions, has issued a security advisory, disclosing actively exploited vulnerabilities in its popular Foxit PDF Reader and Foxit PDF Editor applications. The flaws affect both Windows and macOS users, making a swift update critical to protect against potential cyberattacks.
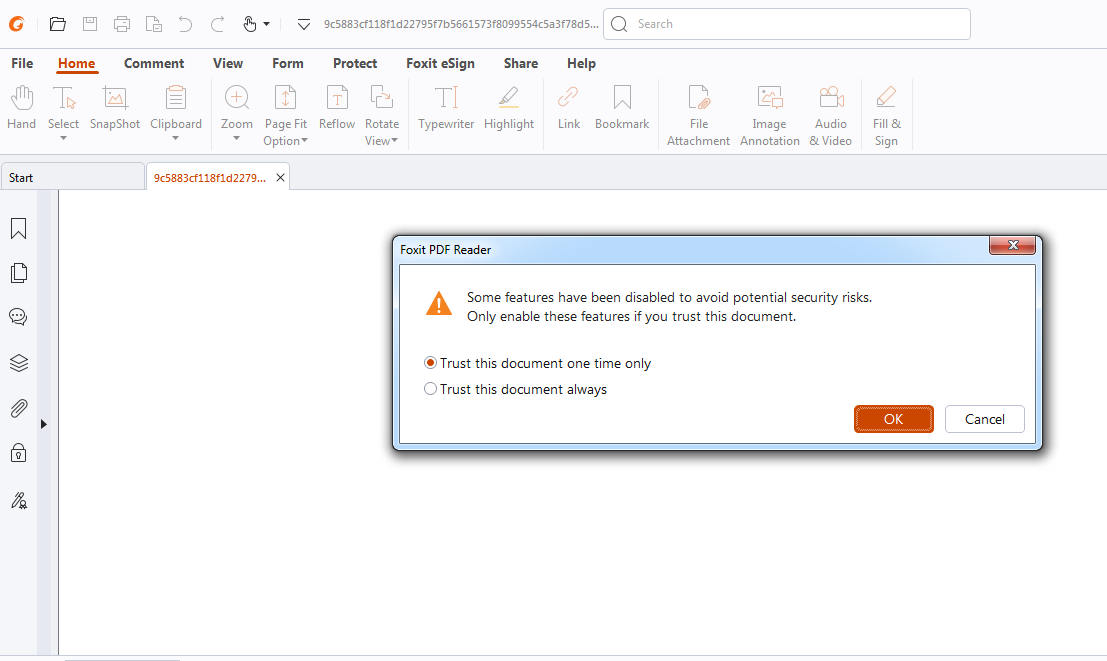
Deceptive Security Warnings Open Door to Attacks

The first major issue involves a design defect in the warning dialog box. When opening certain PDFs containing the Launch File action, the dialog box presents “OK” as the default selected option. This could prompt users to habitually click “OK” without understanding the potential risks, potentially leading to the execution of malicious commands. Haifei Li of EXPMON and @SquiblydooBlog have been credited with reporting this flaw. Both Windows and macOS versions of the software are affected, and there have already been instances of exploitation.
TOCTOU Vulnerability (CVE-2024-29072): Windows Users Face Additional Risk of Privilege Escalation
The second significant issue, identified as CVE-2024-29072 with a CVSS score of 8.2, pertains to a TOCTOU race condition. This vulnerability occurs during the update process of the Windows version of Foxit PDF applications. Attackers could exploit this flaw to replace the update file with a malicious one, leading to privilege escalation. The application fails to properly validate the certificate of the updater executable or lock the permissions of the update file after certificate validation. This flaw was reported by KPC of Cisco Talos, who also published detailed technical information on the vulnerability.
Update Now to Mitigate Risk
Foxit has released version 2024.2.2 for both Windows and macOS platforms to address these critical vulnerabilities. Users are strongly urged to update their software immediately to protect themselves from ongoing exploitation attempts.