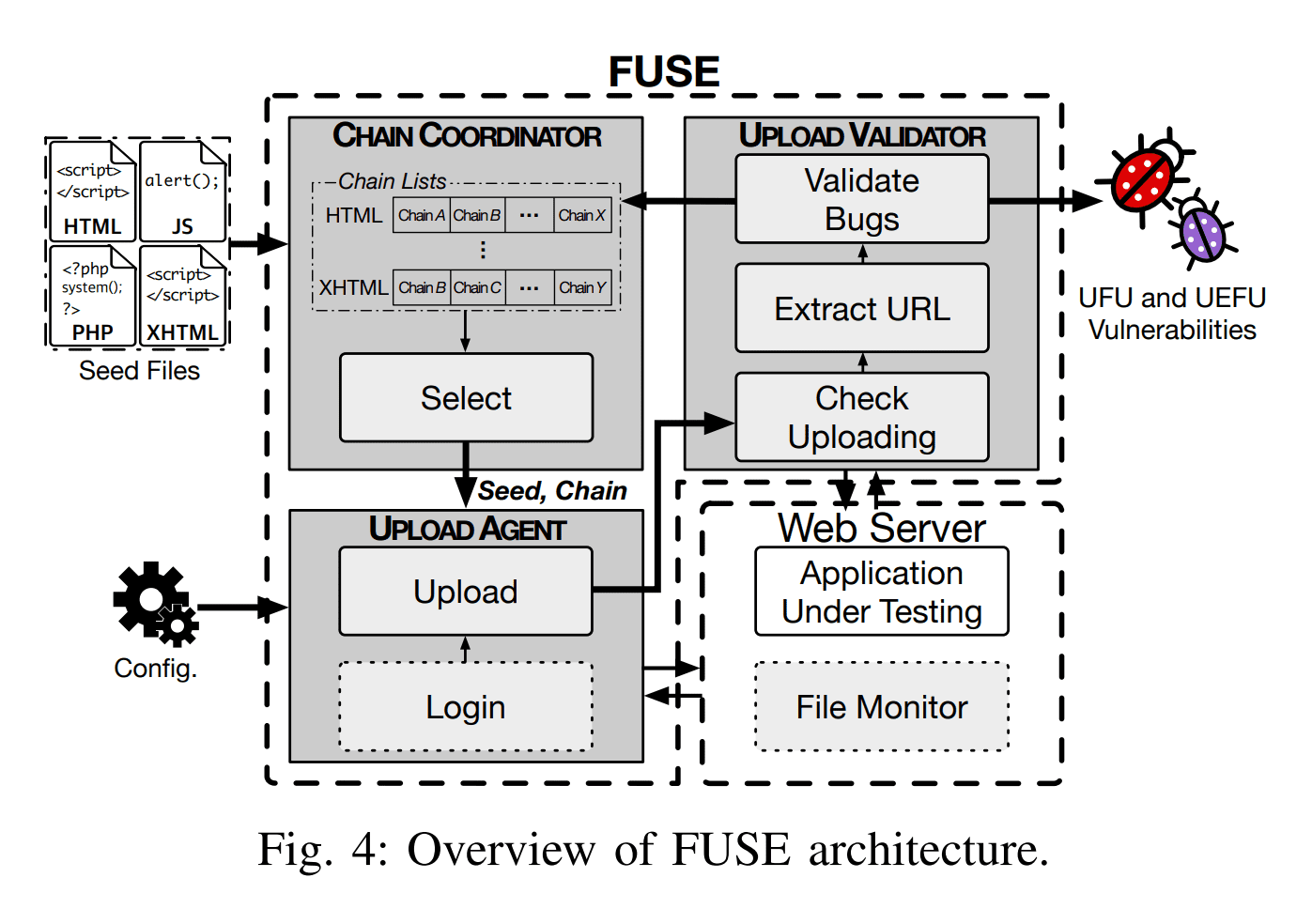
FUSE
FUSE is a penetration testing system designed to identify Unrestricted Executable File Upload (UEFU) vulnerabilities. The details of the testing strategy is in our paper, “FUSE: Finding File Upload Bugs via Penetration Testing”, which appeared in NDSS 2020.
Install
FUSE currently works on Ubuntu 18.04 and Python 2.7.15.
- Install dependencies
# apt-get install rabbitmq-server # apt-get install python-pip # apt-get install git
- Clone and build FUSE
$ git clone https://github.com/WSP-LAB/FUSE $ pip install -r requirement.txt
- If you plan to leverage headless browser verification using selenium, please install Chrome and Firefox web driver by referring selenium document.
Usage
Configuration
- FUSE uses a user-provided configuration file that specifies parameters for a target PHP application. The script must be filled out before testing a target Web application. You can check out README file and example configuration files.
- Configuration for File Monitor (Optional)
Execution
- FUSE
$ python framework.py [Path of configuration file]
- File Monitor
$ python filemonitor.py
- Result
- When FUSE completes the penetration testing, a [HOST] directory and a [HOST_report.txt] file are created.
- A [HOST] folder stores files that have been attempted to upload.
- A [HOST_report.txt] file contains test results and information related to files that trigger U(E)FU.
Author
This research project has been conducted by WSP Lab at KAIST.
- Taekjin Lee
- Seongil Wi
- Suyoung Lee
- Sooel Son
Source: https://github.com/WSP-LAB/