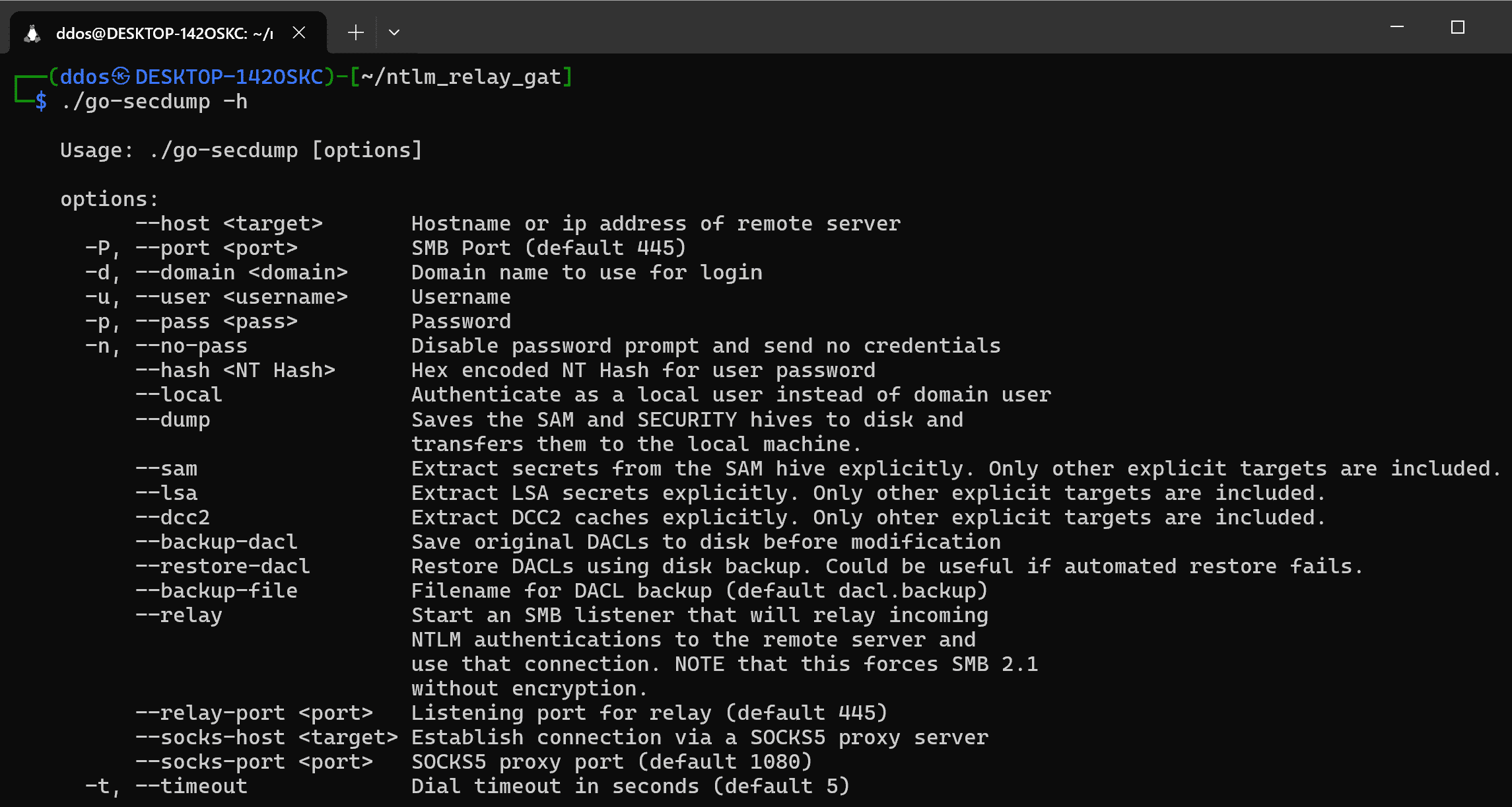
go-secdump
Package go-secdump is a tool built to remotely extract hashes from the SAM registry hive as well as LSA secrets and cached hashes from the SECURITY hive without any remote agent and without touching the disk.
The tool is built on top of the library go-smb and uses it to communicate with the Windows Remote Registry to retrieve registry keys directly from memory.
It was built as a learning experience and as a proof of concept that it should be possible to remotely retrieve the NT Hashes from the SAM hive and the LSA secrets as well as domain cached credentials without having to first save the registry hives to disk and then parse them locally.
The main problem to overcome was that the SAM and SECURITY hives are only readable by NT AUTHORITY\SYSTEM. However, I noticed that the local group administrators had the WriteDACL permission on the registry hives and could thus be used to temporarily grant read access to itself to retrieve the secrets and then restore the original permissions.
Use

Changing DACLs
go-secdump will automatically try to modify and then restore the DACLs of the required registry keys. However, if something goes wrong during the restoration part such as a network disconnect or other interrupt, the remote registry will be left with the modified DACLs.
Using the –backup-dacl argument it is possible to store a serialized copy of the original DACLs before modification. If a connectivity problem occurs, the DACLs can later be restored from a file using the –restore-dacl argument.
Examples
Dump all registry secrets
Dump only SAM, LSA, or DCC2 cache secrets
NTLM Relaying
Dump registry secrets using NTLM relaying
Start listener
Trigger an auth to your machine from a client with administrative access to 192.168.0.100 somehow and then wait for the dumped secrets.
SOCKS Proxy
Dump secrets using an upstream SOCKS5 proxy either for pivoting or to take advantage of Impacket’s ntlmrelayx.py SOCKS server functionality.
When using ntlmrelayx.py as the upstream proxy, the provided username must match that of the authenticated client, but the password can be empty.
Download
Copyright (c) 2023 Jimmy Fjällid