
In a revealing report, Google’s Threat Analysis Group (TAG) has uncovered a series of sophisticated watering hole attacks targeting Mongolian government websites between November 2023 and July 2024. These attacks, which exploited vulnerabilities in both iOS and Android devices, have been linked with moderate confidence to the Russian government-backed hacking group APT29. What makes this discovery particularly alarming is the repeated use of exploits originally developed by commercial surveillance vendors (CSVs), including Intellexa and NSO Group.
The attackers first compromised Mongolian government websites, including cabinet.gov[.]mn and mfa.gov[.]mn, embedding malicious iframes that redirected visitors to attacker-controlled domains. In November 2023, iPhone users running iOS versions older than 16.6.1 were the primary targets, as the compromised websites delivered a WebKit exploit (CVE-2023-41993) that had been previously used in APT29 campaigns in 2021. The payload was a cookie-stealing framework aimed at exfiltrating authentication cookies from prominent websites like Gmail and LinkedIn.
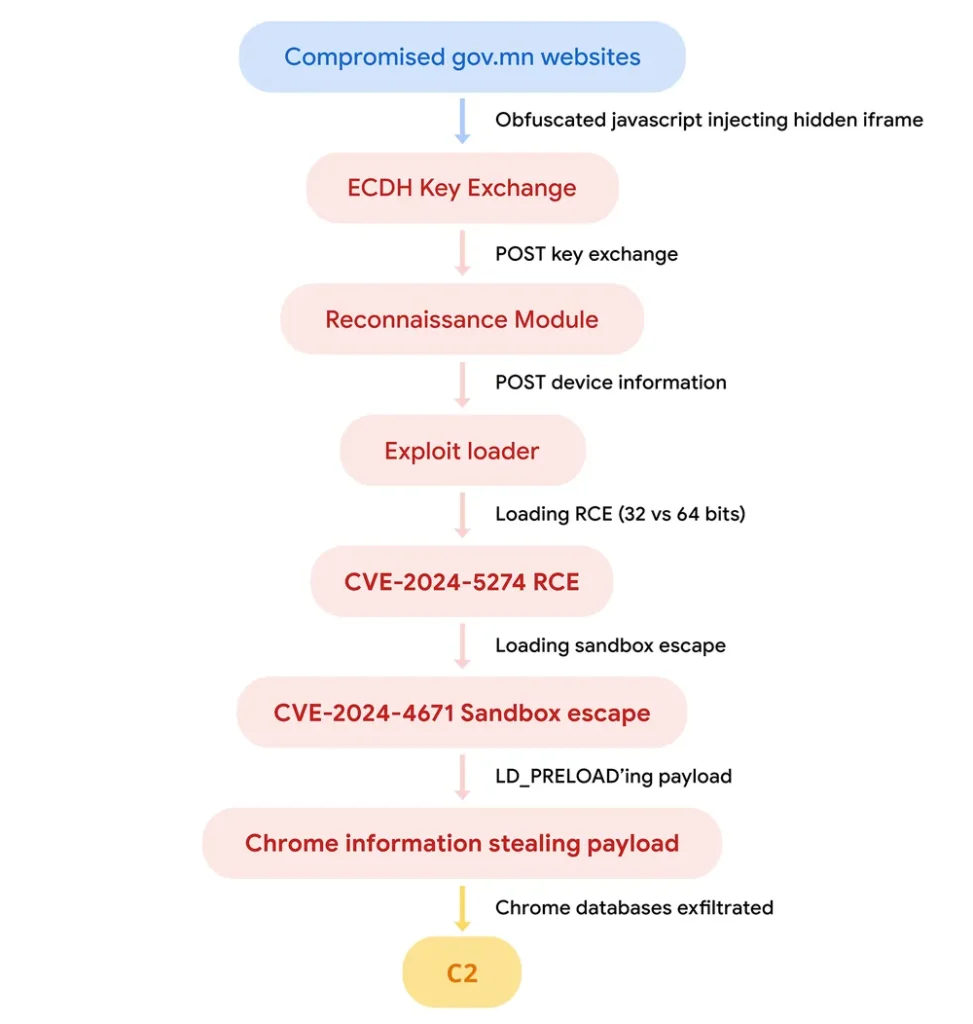
By February 2024, the attackers had updated their target list, continuing to exploit the same WebKit vulnerability while expanding their reach to additional high-value websites. The July 2024 attack marked a significant escalation, as Android users running Chrome versions m121 to m123 were targeted with a new exploit chain. This chain included CVE-2024-5274, a Chrome vulnerability previously seen in attacks by NSO Group, and CVE-2024-4671, used to escape Chrome’s sandbox.
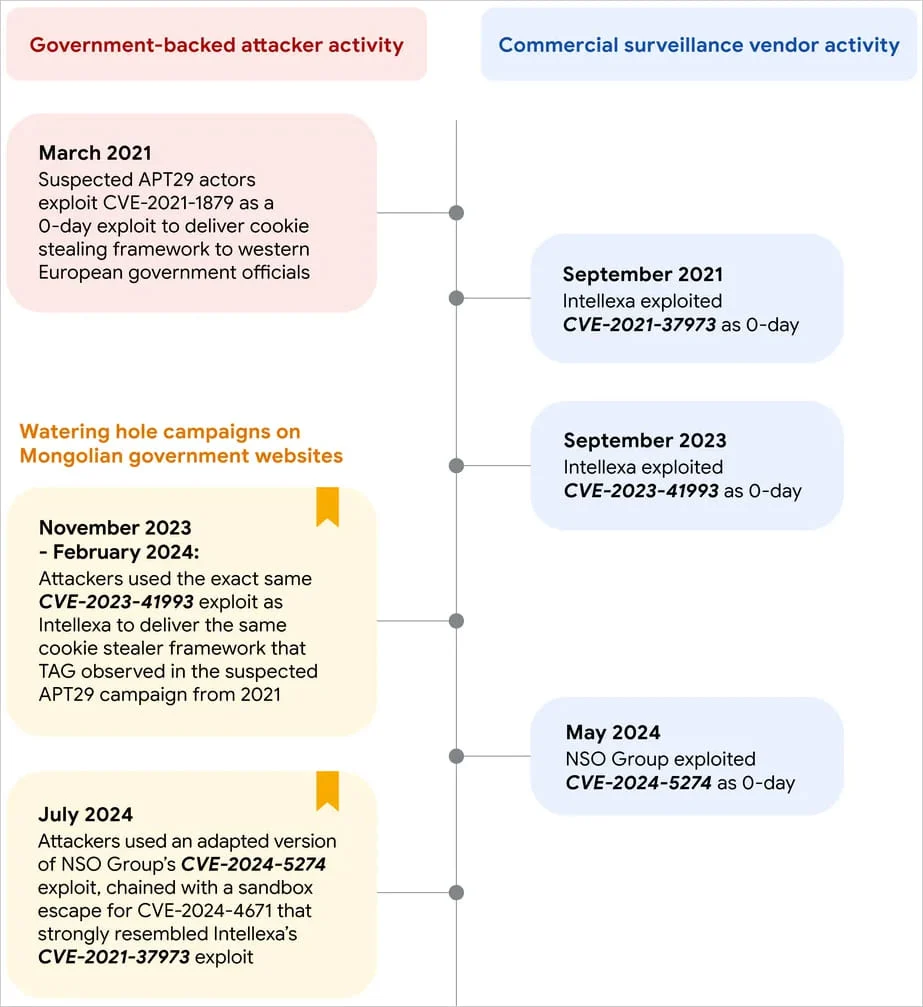
TAG’s analysis highlights a troubling trend: state-backed actors are increasingly using n-day exploits—vulnerabilities that have been patched but are still effective against unpatched systems—that were first employed as 0-days by commercial surveillance vendors. The overlap in exploit usage between APT groups and CSVs underscores the potential for dangerous proliferation of these tools into the hands of more aggressive threat actors.
One striking example is the WebKit exploit used in both the APT29 campaign and a separate operation by Intellexa. Although the underlying vulnerabilities had been addressed, the attackers leveraged these n-day exploits to launch successful attacks against unpatched devices. The similarity between the exploit techniques used by these state-backed actors and those seen in commercial surveillance operations raises questions about how these tools are being acquired and repurposed.
Watering hole attacks, where attackers compromise legitimate websites frequented by their targets, remain a potent method for delivering sophisticated exploits. Despite advances in browser security, these attacks demonstrate that even a single unpatched vulnerability can lead to significant breaches. In the case of the iOS and Chrome campaigns observed by TAG, the attackers’ ability to chain exploits together—bypassing protections like Chrome’s Site Isolation—highlights the ongoing challenges in securing both desktop and mobile platforms.
Upon discovering these campaigns, TAG immediately notified both Apple and Google’s Android and Chrome teams, as well as the Mongolian CERT, to remediate the compromised websites. Google’s Chrome browser on Android offers robust protections, including Site Isolation, which makes it more difficult for attackers to steal data from other websites. However, the attackers’ success in bypassing these defenses by chaining multiple vulnerabilities underscores the need for continuous vigilance and timely patching.
Related Posts:
- APT29 Lures Victims with Fake BMW Ads in Latest Attack
- APT29’s Espionage Campaign Exploits WinRAR Flaw, Targets Embassies
- APT29 Strikes German Politics with WINELOADER Malware Assault
- CVE-2024-5274: Chrome Zero-Day Exploited by APT29, PoC Exploit Published
- Morphisec discovered a new watering hole attack based Flash flaw on Leading Hong Kong Telecom Site