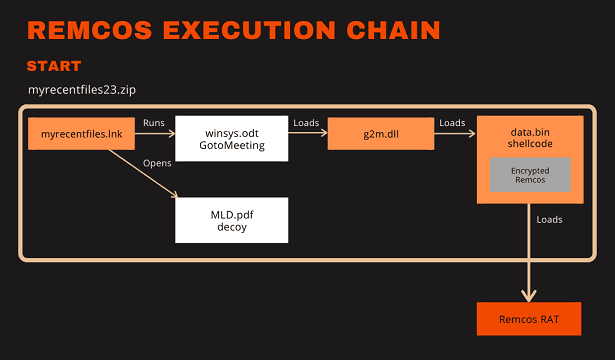
Execution chain of Remcos RAT abusing a legitimate GoTo Meeting executable | Image: G Data
Recently, cybersecurity experts at G Data have uncovered a sophisticated malware campaign that hijacks legitimate applications to execute malicious activities. This particular scheme involves the misuse of GoTo Meeting, a popular online meeting platform, to deploy the notorious Remcos Remote Access Trojan (RAT).

The attackers cleverly disguise their lures using seemingly benign downloads related to software setups, and even tax forms, with filenames in both Russian and English.
A typical scenario starts with a user downloading a deceptive ZIP file, such as “myrecentfiles23.zip”. This file contains a shortcut, “myrecentfiles.lnk”, which masquerades as a PDF through its icon. However, when double-clicked, it simultaneously opens a benign-looking PDF, “MLD.pdf”, and executes a maliciously sideloaded DLL via a legitimately signed GoTo Meeting executable, “winsys.odt”. The seemingly innocuous PDF serves to lower the user’s guard by matching their expectations of opening a document, despite its outdated content.
The core of the attack involves a Rust-written DLL, “g2m.dll”, which sideloads through the GoTo Meeting executable. This DLL is particularly insidious; it exports functions that lead to an empty function, effectively rendering the GoTo Meeting application inoperative. However, its real purpose is to facilitate the execution of a malware loader through its DLLMain function.
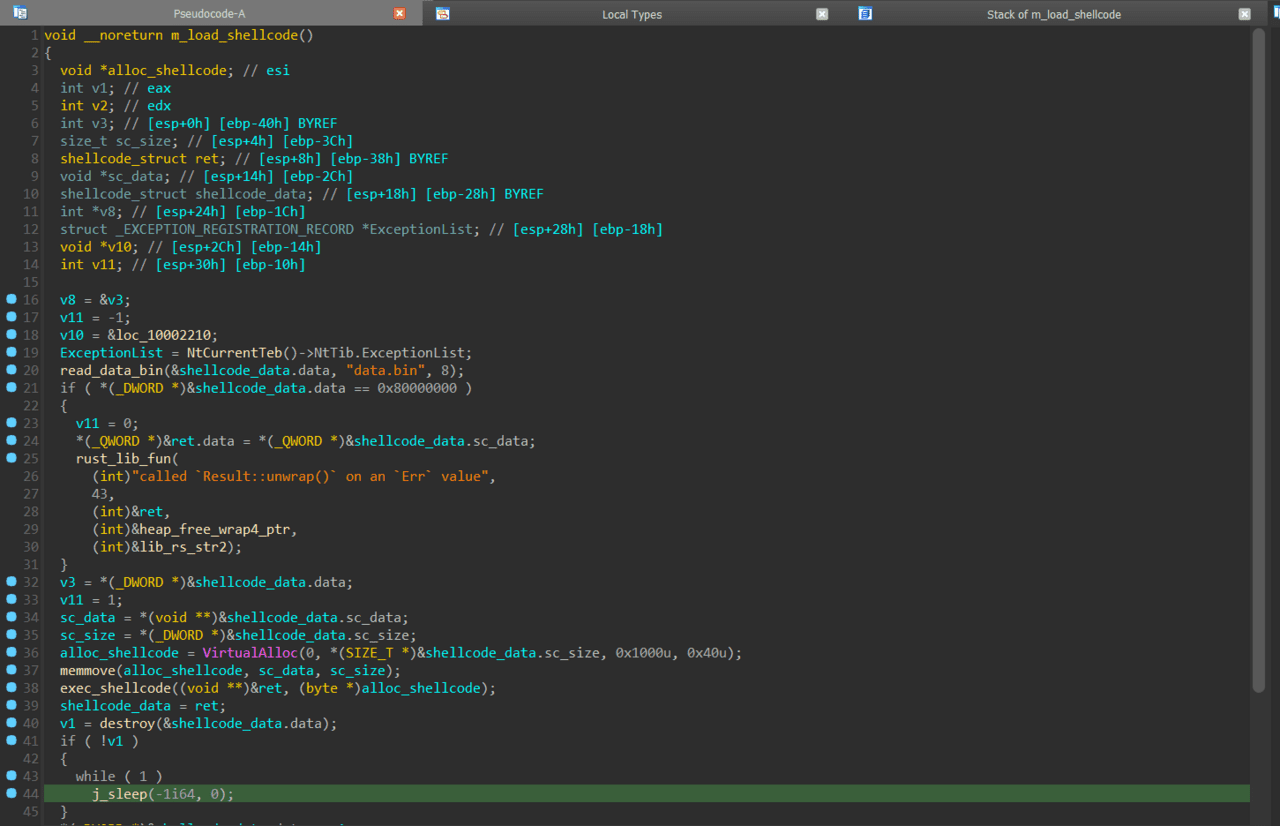
This loader then reads and executes “data.bin”, a file containing encrypted shellcode. The shellcode decrypts and executes the payload, which turns out to be the Remcos RAT—a powerful tool for gaining remote control over the infected machine. Tools like Speakeasy are used to unpack this payload with specific commands, illustrating the complexity and sophistication of the attack.
Further investigation led researchers to uncover additional infection methods and targets by searching for related files on VirusTotal. They discovered various initial infectors, from fake setup files for software like “LeonardoAI2” and “OnlyFans Livestreams” to bogus tax documents and applications for “geodevices” in Russian.
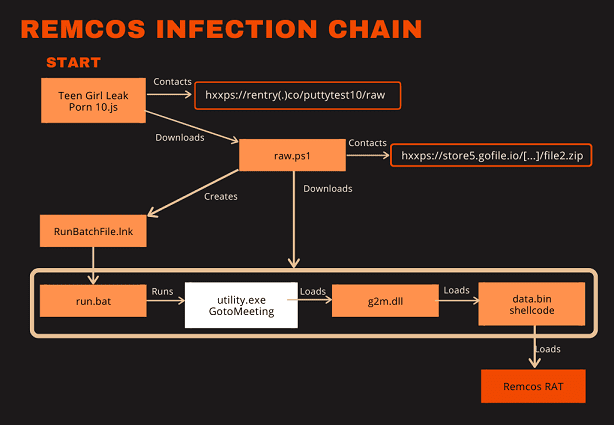
These findings highlight a slightly modified execution chain involving a JScript file, which targets consumers of content. The script initiates a sequence starting with the download of a PowerShell script from a markdown paste service. This script, in turn, fetches a ZIP file and establishes persistence in the system startup folder, thereby ensuring the malware’s continued operation upon reboot.
To protect against this and similar threats, organizations and individuals should:
- Exercise caution when opening attachments or clicking on links, even if they appear to come from trusted sources.
- Keep software up to date, including security patches for GoTo Meeting and other applications.
- Implement robust endpoint security solutions that can detect and block fileless malware and suspicious DLL loading behavior.