CYFIRMA, a leading cybersecurity firm, has issued an urgent warning regarding a critical vulnerability (CVE-2024-3273) discovered in multiple end-of-life D-Link network-attached storage (NAS) devices. This vulnerability has been assigned a CVSS base score of 9.8, underscoring its extreme severity and potential for widespread exploitation.
CVE-2024-3273 enables remote attackers to gain unauthorized control over affected NAS devices, potentially leading to data breaches, unauthorized modifications, and even complete system takeover. This vulnerability is particularly concerning due to the end-of-life status of the impacted devices, meaning they no longer receive security updates or patches from D-Link.
According to D-Link, this vulnerability impacts the EOL NAS device models DNS-320L, DNS-325, DNS-327L, and DNS-340L, and potentially all its EOL NAS devices. This vulnerability poses a significant risk to users who depend on these devices for data storage.

CYFIRMA’s research reveals that this vulnerability is already being actively exploited by threat actors. Discussions and shared intelligence on underground forums, including the exchange of IP addresses of vulnerable devices, indicate a heightened risk for organizations utilizing these NAS devices. Some attacks have been traced back to IP addresses originating from Russia and China, raising concerns about potential state-sponsored cyber espionage activities. Historically, Chinese state-sponsored APT groups such as Camaro Dragon (aka Mustang Panda) and Volt Typhoon have utilized similar firmware implants customized for routers to carry out malicious cyber-attacks.
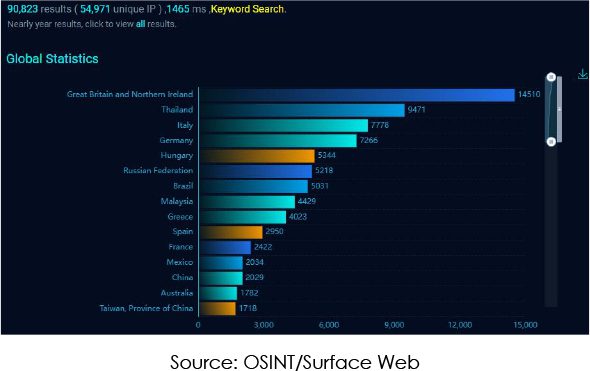
Estimates suggest that over 92,000 D-Link NAS devices globally may be susceptible to this vulnerability. The impact is not limited to a specific sector, as D-Link NAS devices are widely used across industries, including banking, healthcare, software development, and more, for data storage and backup purposes.
D-Link has strongly advised users to immediately decommission or replace affected devices. However, due to their end-of-life status, official patches may not be available. As an interim measure, organizations are urged to disconnect vulnerable devices from their networks and create offline backups of critical data.