Example of a verified YouTube account with a large following, suspected to be compromised.
A new report by Proofpoint security reveals a disturbing trend: hackers are hijacking YouTube to prey on gamers seeking a free ride. Popular games and software are offered as “free” downloads or cheats in videos, but those tempting links unleash a threat much worse than losing in-game rewards.

Proofpoint’s investigation reveals a disturbing trend: threat actors are targeting consumer users, particularly younger audiences drawn to popular video games, by promoting cracked software and game modifications. These videos, complete with instructions that promise enhanced gaming experiences or free upgrades, harbor links that, in reality, lead to the download of information-stealing malware such as Vidar, StealC, and Lumma Stealer.
A particularly insidious tactic observed involves the impersonation of “Empress,” a notorious figure within the software piracy community. Videos under this guise offer seemingly legitimate links to cracked versions of games like “League of Legends.” However, the provided links only serve the purpose of disseminating malware, with one example leading unsuspecting victims to a Telegram URL followed by a MediaFire link containing the malevolent “empress.exe” file.
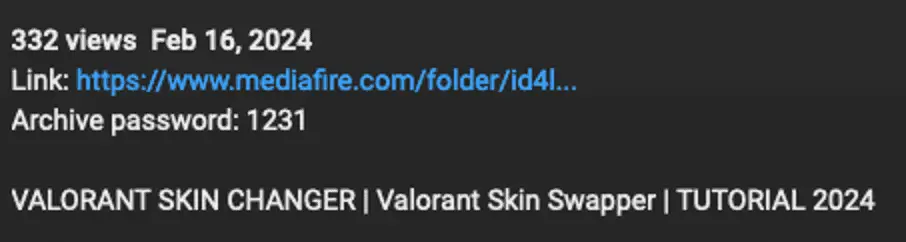
The distribution strategy is as ingenious as it is malicious. The videos typically include links to password-protected .rar files, which, when executed, download and install the malware. This method of distribution not only preys on the trust of users but also utilizes sophisticated evasion techniques to sidestep antivirus solutions, such as padding the executable files to exceed the scanning capabilities of many security tools.
Proofpoint’s report also highlights the use of social media and community forums for command and control (C2) activities, allowing the malware to camouflage its network traffic amongst legitimate connections to platforms like Telegram, Steam Community, and Tumblr.
Another notable vector for malware distribution identified by Proofpoint is the use of Discord servers. These servers host various malware files associated with different video games, providing a seemingly innocuous environment for users to download game cheats or bypass paid functionalities. Instructions often accompany these downloads, misleading users to disable their antivirus software, further compromising their security.
This campaign’s emergence on YouTube, a platform frequented by millions daily, underscores the evolving landscape of cyber threats and the ingenious methods employed by cybercriminals to target unsuspecting users. While YouTube has been prompt in removing reported content, the fleeting nature of these channels—often active for mere hours before dispersing their payload—presents a significant challenge to cybersecurity defenses.