
Unit 42 has uncovered HeartCrypt, a Packer-as-a-Service (PaaS) designed to protect malware from detection. Since its launch in February 2024, HeartCrypt has rapidly become a popular choice among cybercriminals, packing over 2,000 malicious payloads for 45 different malware families, including LummaStealer, Remcos, and Rhadamanthys.
HeartCrypt offers malware operators an affordable, efficient method to obscure their payloads. Advertised on platforms like Telegram, BlackHatForums, and XSS.is, the service charges $20 per file for packing. Unit 42 notes: “HeartCrypt packs malicious code into otherwise legitimate binaries,” allowing malware to evade detection.
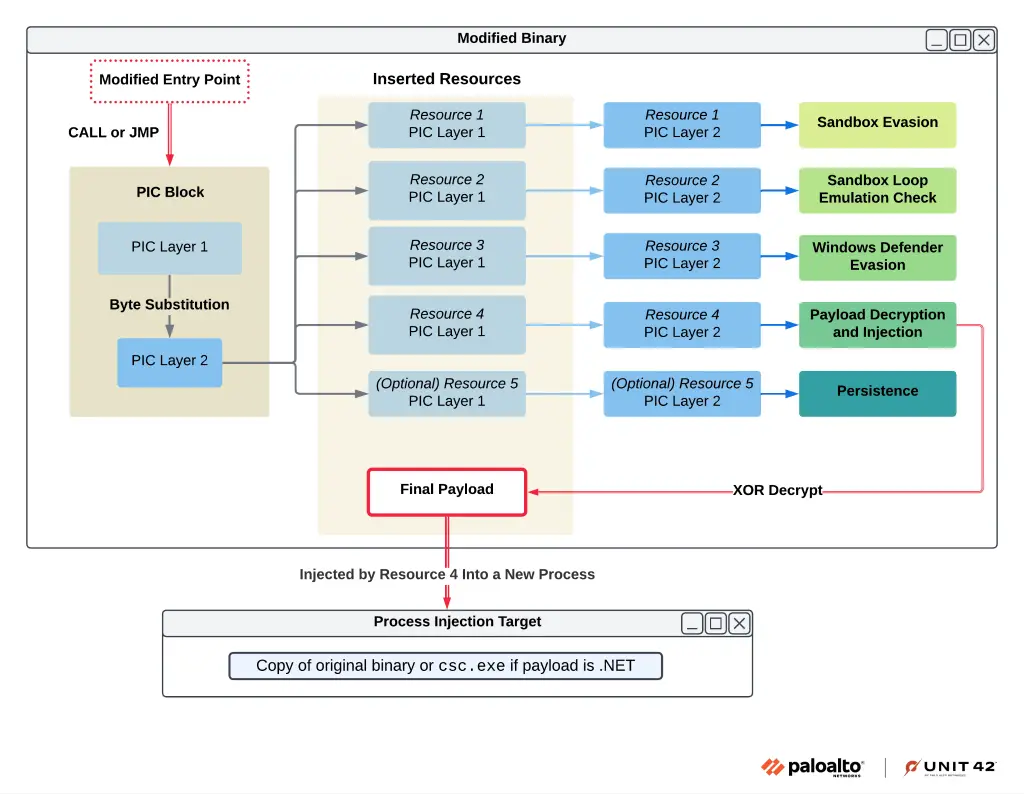
HeartCrypt combines several advanced techniques to hide malicious payloads:
- Injection into Legitimate Files: Malicious code is embedded in real executables, often outdated or low-profile binaries. This makes detection challenging for non-technical users.
- Control Flow Obfuscation: Techniques like dynamic API resolution, junk bytes, and stack strings hinder reverse engineering efforts.
- Layered Encryption: Each sample features multiple layers of obfuscation, including encoded payloads disguised as bitmap (BMP) files.
Unit 42 explains: “The injected PIC leverages multiple control flow obfuscation methods to hinder analysis,” including:
- Stack strings
- Dynamic API resolution
- Hundreds of direct jmp instructions
- Non-returning functions
- Arithmetic operations that have no effect on program execution
- Junk bytes after jmp and call instructions, impeding disassembly and decompilation
HeartCrypt employs sandbox detection and antivirus evasion methods, including:
- Dependency Emulation Checks: Attempts to load fake DLLs to detect sandbox environments.
- Windows Defender Evasion: Identifies virtual DLLs within Defender’s emulator to bypass detection.
- Anti-VM Techniques: Uses Direct3D API calls to detect virtual environments.
HeartCrypt has facilitated campaigns using various malware families. Key examples include:
- LummaStealer: Targeted users with fake CAPTCHA pages and impersonated legitimate software vendors.
- Remcos RAT: Frequently used in Latin American campaigns, including those impersonating well-known brands.
- Rhadamanthys: Leveraged for advanced financial theft and credential harvesting.
Unit 42 highlights HeartCrypt’s role in broadening access to malware: “HeartCrypt’s PaaS model lowers the barrier to entry for malware operators, increasing the volume and success of infections.”
HeartCrypt has been associated with peaks of up to 60 new samples per day, reflecting its rapid adoption among cybercriminals. These samples exhibit unique XOR keys and encoded payloads, suggesting client-side customization for different campaigns.
HeartCrypt’s evolution illustrates the commoditization of cybercrime tools. Launched as a service, it provides even novice threat actors with access to advanced obfuscation techniques
Related Posts:
- Palo Alto Networks’ Unit 42 Reveals a New Cyber Threat in China: Financial Fraud APKs
- EDRsandblast Exploited: How Attackers are Weaponizing Open-Source Code
- New VMware Findings: Kernel Drivers’ Vulnerabilities Risk Total Device Takeover
- A New Set of Tools for Cyber Espionage: Targeting the Middle East, Africa, and the US