Ransomware login page | Source: CRIL
On August 9, 2024, the HexaLocker ransomware group unveiled a new variant of their infamous malware on Telegram. Written in Go, the ransomware promised a more sophisticated attack strategy. This announcement marked the group’s ambitious return following earlier declarations of their shutdown in October. By December, the cybersecurity community witnessed their resurgence with a revitalized HexaLocker ransomware, now bolstered by the addition of the Skuld stealer.
HexaLocker V2 exhibits a significant evolution in both functionality and complexity compared to its predecessor. According to Cyble Research and Intelligence Labs (CRIL), the ransomware now combines advanced encryption techniques with data theft capabilities.
- Persistence Mechanisms: Upon execution, HexaLocker V2 creates a self-copy in the %appdata%\MyApp directory, naming it myapp.exe. It then establishes persistence via an AutoRun entry in the Windows registry, ensuring execution on reboot.
- Advanced Obfuscation: The ransomware leverages AES-GCM decryption to generate strings such as stealer URLs and ransom notes during runtime. This dynamic approach makes it harder for security solutions to detect malicious activity.
- Pre-Encryption Data Theft: Before locking files, HexaLocker V2 deploys Skuld, an open-source stealer designed to extract sensitive information, particularly from browsers, crypto wallets, and Discord accounts. For example, Skuld targets popular browsers like Chrome, Firefox, and Edge, exfiltrating data such as cookies, saved credentials, and even credit card details. These details are compressed into a ZIP archive and sent to a remote server.
- Encryption with ChaCha20: The ransomware uses the ChaCha20 encryption algorithm to lock victim files, appending the extension .HexaLockerV2. It then deletes the original files to prevent recovery. Notably, this enhanced encryption algorithm is accompanied by stronger keys, which are transmitted to an attacker-controlled server for victim identification and potential recovery negotiation.
Victims are presented with a ransom note instructing them to contact the threat actors (TAs) through various channels, including Signal, Telegram, and a dedicated web chat. The stolen data and encryption keys are uploaded to a HexaLocker-controlled server.
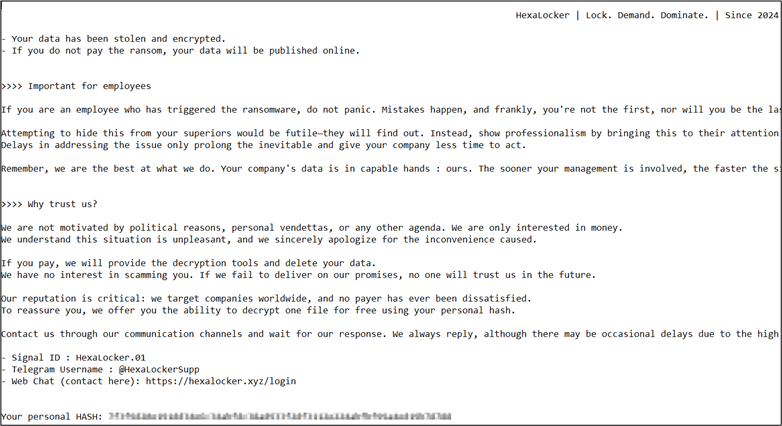
The integration of Skuld reflects a strategic shift in the group’s tactics. By exfiltrating data before encryption, HexaLocker V2 adds leverage to their ransom demands. Skuld’s focus on Chromium and Gecko-based browsers, among others, showcases its versatility. “This strategic combination of the Skuld stealer and the ransomware highlights the continuous evolution and sophistication of the HexaLocker group, posing an ongoing threat to targeted systems,” CRIL analysts observed.
For those seeking a proactive defense, the Yara rule to detect HexaLocker V2 is now available on GitHub.
Related Posts:
- New Skuld Infostealer Campaign Unveiled in npm Ecosystem
- Roblox Developers Targeted in Supply Chain Attack with Malicious npm Packages
- Roblox Cheaters Targeted: Skuld Stealer and Blank Grabber Malware Lurks in PyPI Packages
- Sophisticated Campaign Targets Manufacturing Industry with Lumma Stealer and Amadey Bot
- Malware Alert: Banshee Stealer Targets macOS Users