heyserial: create hunting rules for deserialization exploitation
HEY SERIAL!
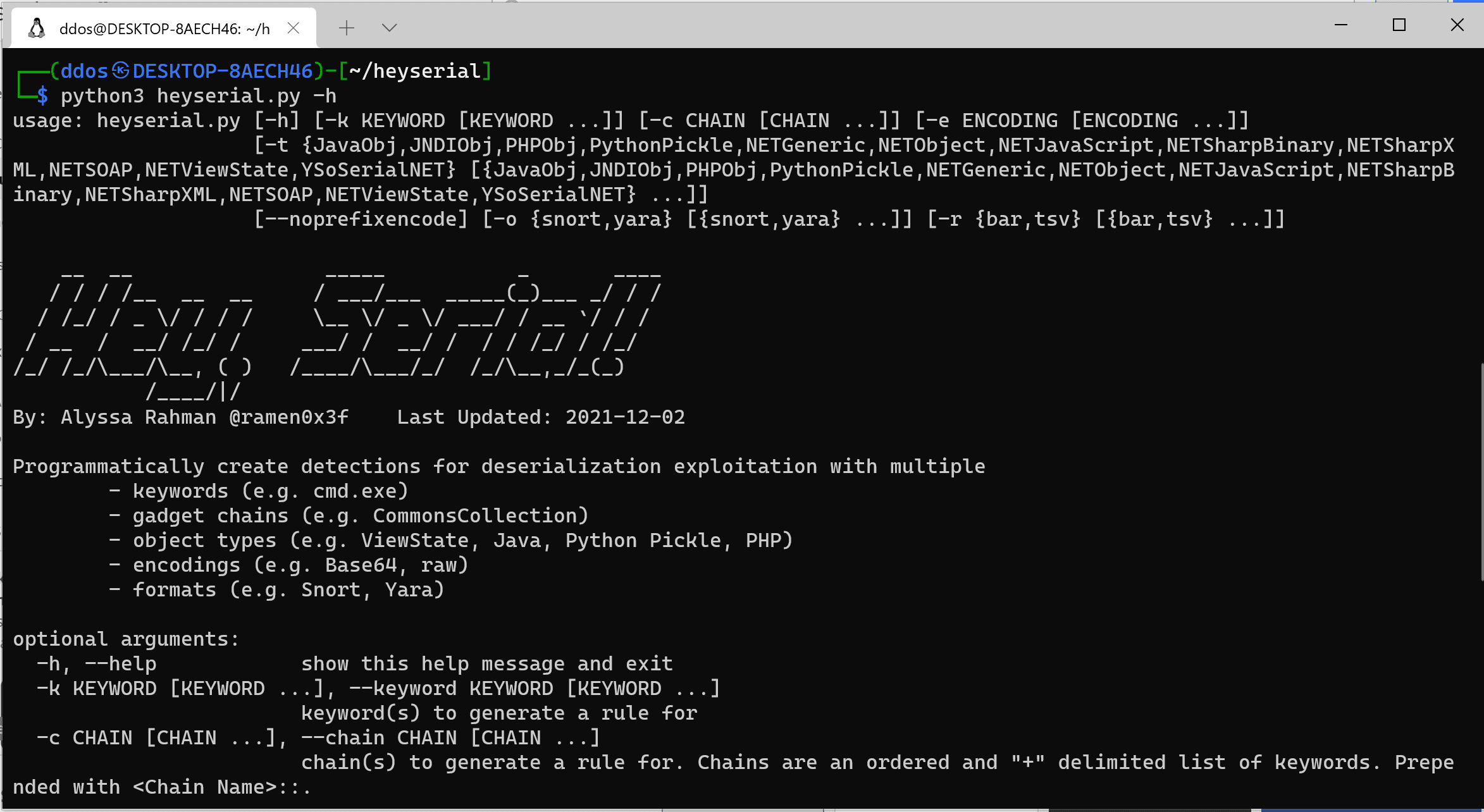
Programmatically create hunting rules for deserialization exploitation with multiple
- keywords (e.g. cmd.exe)
- gadget chains (e.g. CommonsCollection)
- object types (e.g. ViewState, Java, Python Pickle, PHP)
- encodings (e.g. Base64, raw)
- rule types (e.g. Snort, Yara)
Install
git clone https://github.com/mandiant/heyserial.git
cd heyserial
pip install -r REQUIREMENTS
Use
Example
python3 heyserial.py -c ‘ExampleChain::condition1+condition2’ -t JavaObj
python3 heyserial.py -k cmd.exe whoami ‘This file cannot be run in DOS mode’
python3 heyserial.py -k Process.Start -t NETViewState -e base64 “base64+utf16le”
Utils
utils/checkyoself.py
This is a tool to automate bulk testing of Snort and Yara rules on a variety of sample files.
Usage: python3 checkyoself.py [-y rules.yara] [-s rules.snort] [-o file_output_prefix] [–matches] [–misses] -d malware.exe malware.pcap
Examples: python3 checkyoself.py -y rules/javaobj -s rules/javaobj -d payloads/javaobj pcaps –misses -o java_misses
utils/generate_payloads.ps1
YSoSerial.NET v1.34 payload generation. Run on Windows from the ./utils directory.
- Source: https://github.com/pwntester/ysoserial.net
- License: ysoserial.net_LICENSE.txt
utils/generate_payloads.sh
YSoSerial payload generation. Run on Linux from the ./utils directory.
- Source: https://github.com/frohoff/ysoserial
- License: ysoserial_LICENSE.txt
utils/install_snort.sh
Installing Snort on a Debian-based system was a bit finicky for me, so I wrote my install notes here.
Use at your own risk in a VM that you have snapshotted recently.
utils/server.py
Simple Python script that runs an HTTP server on 127.0.0.1:12345 and accepts POST requests.
Handy for generating test PCAPs.
For more details on this tool and the research process behind it, check out our blog!
Copyright (C) 2021 Alyssa Rahman, Mandiant, Inc. All Rights Reserved
Source: https://github.com/mandiant/