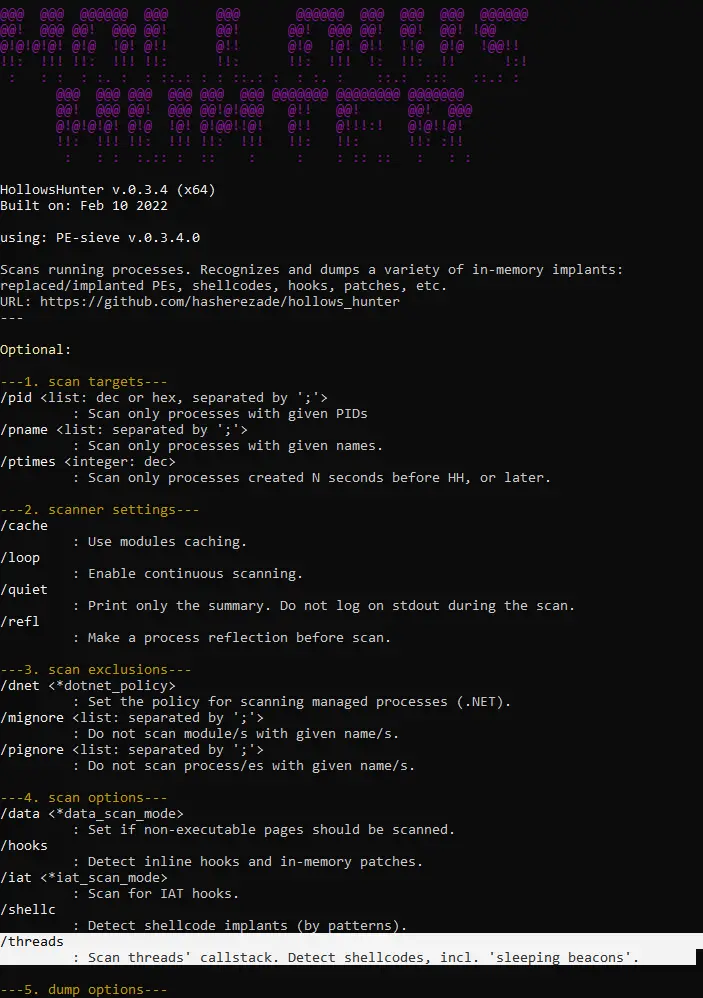
hollows_hunter
Scans all running processes. Recognizes and dumps a variety of potentially malicious implants (replaced/implanted PEs, shellcodes, hooks, in-memory patches).
It is an application based on PE-sieve (a library version), so there is a big overlap of the features between those two. They have a similar command-line interface, but while PE-sieve is an engine dedicated to scanning a single process, Hollows Hunter offers many additional features and filters on the top of this base.

Features
Hollows Hunter vs PE-sieve
Hollows Hunter gives you access to all the PE-sieve features, so the list of features from PE-sieve wiki is relevant.
In contrast to PE-sieve, HollowsHunter scan multiple processes, one by one.
In order to avoid noise, one of the default PE-sieve features (scanning for code patches and hooks) is not default in HollowsHunter. It can be enabled by a /hooks parameter.
Selecting processes to scan
By default, HollowsHunter scans all accessible processes. However, we can make the scan more focused, and select only processes of our interest. There are a few criteria by which we can do the selection:
- by name (parameter /pname)
- by PID (parameter /pid)
- by the time of process creation (parameter /ptimes) – relative to the start of HollowsHunter
PID can be supplied as a decimal or hexadecimal number.
In contrast to PE-sive, where only one process can be selected, HollowsHunter allows to supply a list. Both, /pname and /pid can let us supply multiple elements, separated by ;.
Example:
- hollows_hunter.exe /pname svchost.exe;explorer.exe – will scan only processes named svchost.exe and explorer.exe
- hollows_hunter.exe /pid 456;123 – will scan only processes with PIDs 456 and 123
Output directories
In both, PE-sieve and HollowsHunter, you can specify the output directory where the dumps will be saved by using a /dir parameter. If it is not selected, the output will be saved in the current directory where the application was run.
Additionally, HollowsHunter offers a /uniqd parameter – to create a unique, timestamped directory on each scan, so that the content of the previous dump will not get overwritten.
If you use both /dir <out_dir> and /uniqd parameters, then the <out_dir> will be used as a root directory, where the unique directory with dumps will be created.
Continuous scan
Sometimes a single scan is not enough, and rather than this we want HollowsHunter to run in a loop. You can do it by using /loop parameter. Keep in mind that scanning all the processes in a loop can be processor-consuming. So, it is recommended to use it occasionally, and only for selected processes.
This feature can be useful i.e. when we are unpacking malware, and we expect that at some point it will make an injection to a process with a particular name. Scanning in a loop can help us to capture this moment.
Killing or suspending detected processes
After the suspicious processes are detected and reported, we may choose to do something about them. There are two options:
- /suspend – suspend the process
- /kill – kill the process
Changelog v0.3.8
FEATURE
- Supported new PE-sieve param:
/obfusc - Supported new options for PE-sieve
/shellcparam
Download
Copyright (c) 2018-2022, @hasherezade
All rights reserved.