What is Horusec?
Horusec is an open-source tool that performs a static code analysis to identify security flaws during the development process. Currently, the languages for analysis are C#, Java, Kotlin, Python, Ruby, Golang, Terraform, Javascript, Typescript, Kubernetes, PHP, C, HTML, JSON, Dart. The tool has options to search for key leaks and security flaws in all files of your project, as well as in Git history. Horusec can be used by the developer through the CLI and by the DevSecOps team on CI /CD mats. See in our DOCUMENTATION the complete list of tools and languages that we perform analysis.
Horusec manager
- Separate repositories by companies
- Manage users who have access to your company (users must be pre-registered on horusec to be invited to a pre-existing company)
- Manage the repositories available in your company for analysis
- Manage users who have access to company repositories
- Manage your access tokens for the specific repository (required to identify which repository this analysis belongs to and save to our system)
- Visually view all existing vulnerabilities in your company and/or its repository
How does Horusec work?
Horusec performs a SAST analysis of your project from the code perspective.
The tool uses:
- Horusec-CLI when you run the commands performs security analysis and the vulnerabilities identification and classification.
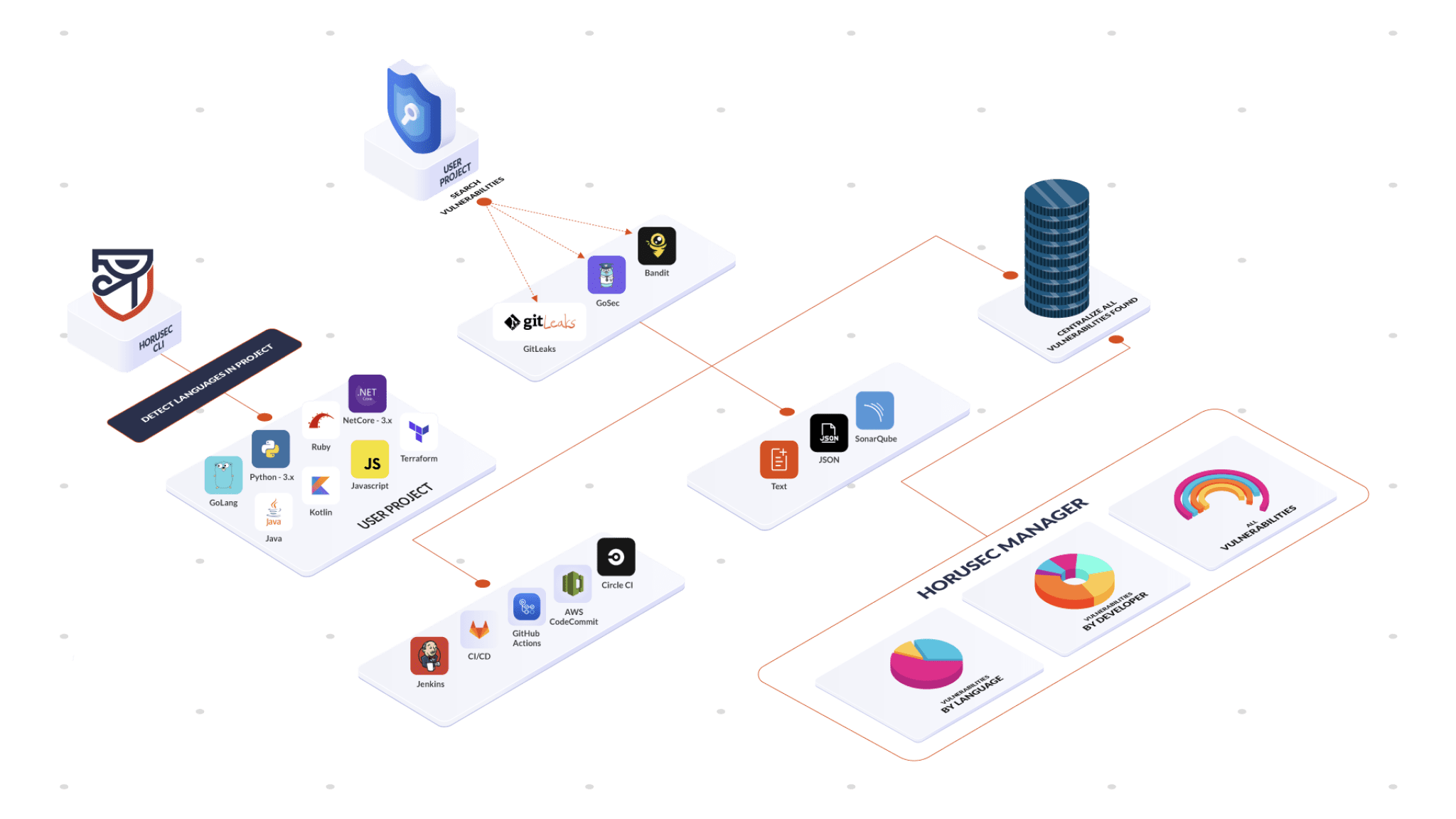
- Web application is the CLI extension used to manage and classify the vulnerabilities found in your application. See the structure in the image below:
When Horusec starts an analysis, it follows the steps below:
- 1- When you start an analysis through Horusec-CLI, it will identify what are the current languages in your project;
- 2- Now, the tool will start the analysis according to the identified languages, searching for vulnerabilities;
- 3- When the analysis finishes, it will start 3 actions:
- 3.1- Show the analyis’ output in your interface or in the file;
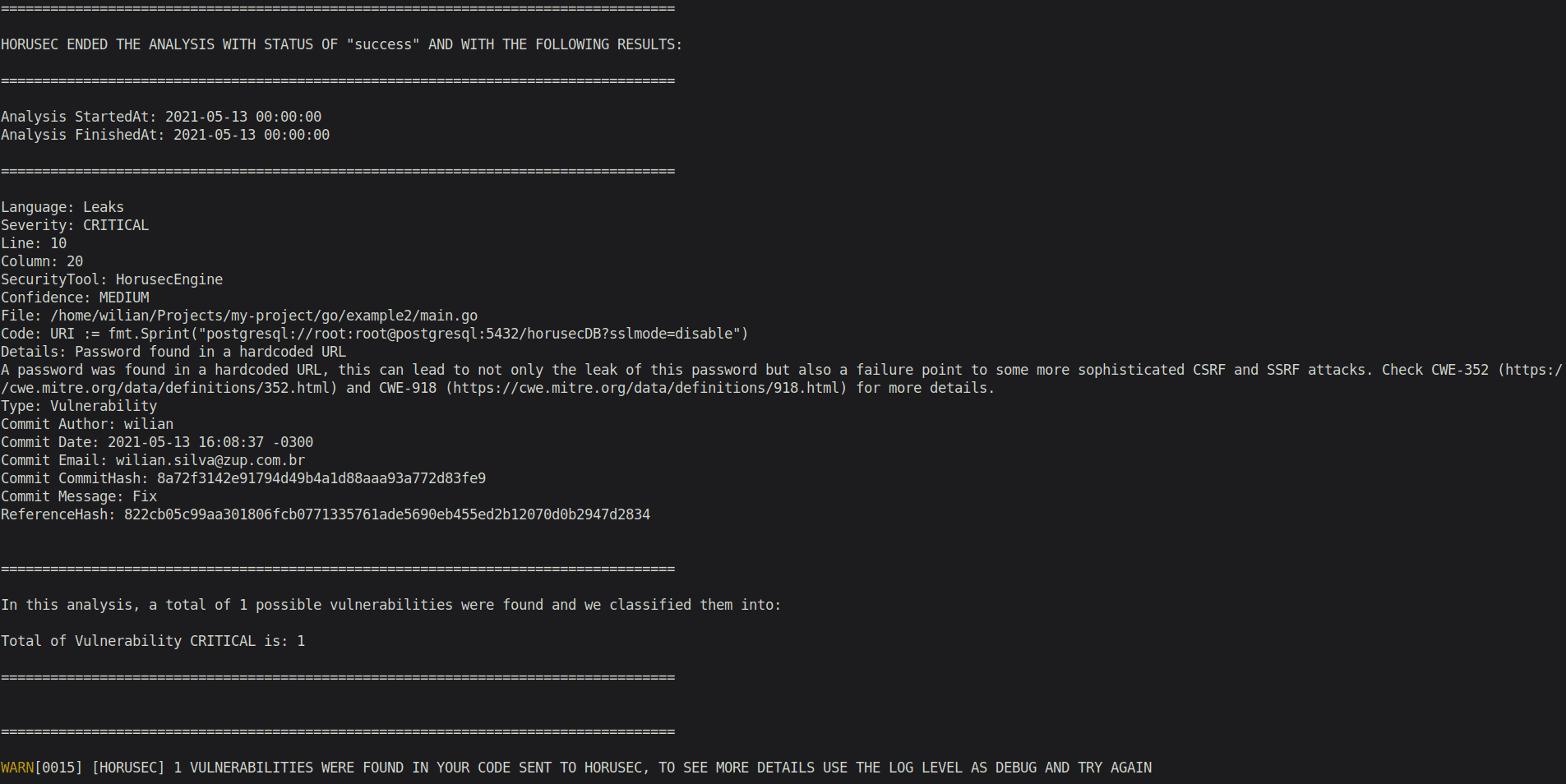
- 3.2- If you have been using the CI/CD process in your pipeline and you want to abort the operations, a return type
exit 1will be sent and it won’t go on until all the vulnerabilities are corrected. If there isn’t any vulnerabilities, a status typeexit 0will be returned and it will proceed to the next step.
- 3.3- Send to Horusec-Manager(web platform) where you can see all the vulnerabilities found, in an analytical way, you can also manage your project;
- 3.1- Show the analyis’ output in your interface or in the file;
Changelog v2.8
Features
- f0df9f4: docker:feature – Validate Docker version from the Docker API (#965) (@luiguip)
- 522076a: cli:feat – add SARIF output support (#946) (@anthturner)
- df2e20c: hash:feature – new hash format and handle the future depreciations (#996) (@nathanmartinszup)
- 578e883: workflow:feat – Automating the release notes (#997) (@wiliansilvazup)
- 6e052fb: java:feature – Add Rule for CVE-2022-21724 (#1033) (@wiliansilvazup)
- 2c11096: rules:feat – adding rule to spring framework rce (#1053) (@nathanmartinszup)
- a615329: docs:feat – Security Policies (#1052) (@lucasbrunozup)
Bug fixes
- 1bfe223: install/sh:bugfix – updating install sh to install latest if more recent (#913) (@nathanmartinszup)
- 9245d7d: bundler:fix – correctly parse output error (#921) (@matheusalcantarazup)
- e263056: formatters:fix – not show which tool generate the error (#932) (@matheusalcantarazup)
- 0a2ecee: trivy:bugfix – adding func to avoid hash changes in trivy formatter (#929) (@nathanmartinszup)
- 73511f0: engine/swift:bugfix – improving HS-SWIFT-24 rule to avoid false positives (#930) (@nathanmartinszup)
- 18e8b89: formatters/tfsec:bugfix – vulnerabilities were being ignored due missing severity (#934) (@nathanmartinszup)
- 87673d1: engine/leaks:bugfix – improving leaks rule 26 (#972) (@nathanmartinszup)
- c4184c5: engines/jvm:fix – false positives on base64 encode/decode (#974) (@matheusalcantarazup)
- 22acb2b: dockerfile:fix – update and upgrade packages (#977) (@matheusalcantarazup)
- 0c1e691: commitAuthors:bugfix – fix when pass invalid line to SetCommitAuthors and changed formatters error handling approach (#978) (@iancardosozup)
- b6d92cd: dockerfiles:bugfix – adding no cache flag (#982) (@nathanmartinszup)
- 1b9673d: dockerfiles:bugfix – updating docker base image (#983) (@nathanmartinszup)
- 6e4d0c1: dockerfile:bugfix – updating dockerfiles docker base image (#989) (@nathanmartinszup)
- f860773: docs:fix – commit template message (#992) (@matheusalcantarazup)
- 345c748: analyzer:bugfix – separate warnings from errors (#1013) (@nathanmartinszup)
- 29c7330: gitleaks:bugfix – updating formatter to gitleaks v8 (#1010) (@nathanmartinszup)
- 96fbcc8: sarif:bugfix – removing version prefix (#1019) (@nathanmartinszup)
- 8517c84: goreleaser:bugfix – adding release auto (#1027) (@nathanmartinszup)
- 748d681: utils/file:fix – missing {HORUSEC_CLI} prefix and typo on log debug (#1025) (@matheusalcantarazup)
- a0c13d2: docker:fix – missing image name on debug log (#1026) (@matheusalcantarazup)
- e8eb1ba: horusec:fix – Errors reported in v2.8.0-beta.1 (#1050) (@wiliansilvazup)
- df32c1c: analyzer:fix – Fixing details wrong (#1054) (@wiliansilvazup)
Chores
- f2c500d: yarnaudit:chore – improve tests and code cleaning (#910) (@matheusalcantarazup)
- 0df35e4: analyzer:chore – split analyzer implementation into runner (#909) (@matheusalcantarazup)
- d3018a8: workflow/security:chore – updating security workflow to use latest rc (#911) (@nathanmartinszup)
- 802f0c4: formatters:chore – remove unused methods from IService (#912) (@matheusalcantarazup)
- 04f682e: formatter:chore – replace strings.Replace to fmt.Sprintf (#914) (@matheusalcantarazup)
- d0f5f52: nancy:chore – remove logs when running without GITHUB_TOKEN env (#922) (@matheusalcantarazup)
- c43d93c: engine/java:chore – add CVE-2021-44832 detail to the description of the HS-JAVA-150 rule (#916) (@dearrudam)
- bfb07e6: workflows:chore – removing old release file to avoid confusion (#924) (@nathanmartinszup)
- 112e82e: bundler:chore – improve tests and code cleaning (#925) (@matheusalcantarazup)
- 5d8b435: phpcs:chore – Update PHP_CodeSniffer to show severity and code (#935) (@wiliansilvazup)
- 3d9f22a: engine:chore – update to new engine (#923) (@iancardosozup)
- a175361: sonarqube:chore – merge entities/sonarqube with services/sonarqube pkg (#947) (@matheusalcantarazup)
- ae31579: git:chore – move CommitAuthor declaration to git pkg (#948) (@matheusalcantarazup)
- 886da4c: makefile:chore – bump gci tool (#970) (@matheusalcantarazup)
- 43c551d: swift:chore – Improvements Tests of all Swift Rules (#953) (@wiliansilvazup)
- 6b630c1: kubernetes:chore – Improvements Tests of all Kubernetes Rules (#961) (@wiliansilvazup)
- aadaaed: enums:chore – remove unused enums/engine pkg (#979) (@matheusalcantarazup)
- 9f7dd64: checkov:chore – removing pborman/ansi dependency (#975) (@iancardosozup)
- 6abcc37: engine/java:chore – updating log4j rule to avoid false positives (#980) (@nathanmartinszup)
- 8659ee7: formatters:chore – add missing RuleIDs (#967) (@anthturner)
- d7fcbe3: lint:chore – Fix lint, format and Horusec API tests (#1004) (@wiliansilvazup)
- 0bd4d4d: formatters:chore – normalize not found files warn message (#1023) (@matheusalcantarazup)
- 649b267: formatters/ruby:chore – removing unnecessary error messages (#1024) (@nathanmartinszup)
- 763a796: custom_rules:chore – Refactored tests for custom_rules to table tests (#1049) (@Adam88morris)
- 013b22e: javascript::chore – Adding improvements on javascript rules (#1043) (@wiliansilvazup)
- 40d4191: csharp:chore – Improvements on safe and unsafe code in csharp (#1037) (@wiliansilvazup)
- cf7b1bf: dart:chore – Adding improvements on dart rules (#1038) (@wiliansilvazup)
- 6a4dd93: k8s:chore – Adding improvements on k8s rules (#1039) (@wiliansilvazup)
- 841c343: leaks:chore – Adding improvements on leaks rules (#1040) (@wiliansilvazup)
- 229df8b: swift:chore – Adding improvements on swift rules (#1042) (@wiliansilvazup)
- c6f20fe: nginx:chore – Adding improvements on nginx rules (#1041) (@wiliansilvazup)
Others
- f14f910: fix:semgrep – Disable collect metrics and fix log message (#968) (@wiliansilvazup)
- 0f24a9e: chore:workflow – Added new workflow to validate release workflows (#988) (@wiliansilvazup)
- 51a7006: docs: add issues section (#991) (@HenriqueZup)
- 2aa2c5b: release:build – Removing GPG and sign images from build.yaml (#1018) (@wiliansilvazup)
- ac6405a: scs: bugfix – att outdated chsharp sdk on horusec-engine-csharp (#1022) (@iancardosozup)
- cce34ce: This commit implements vulnerable and safe samples for the javascript rules. (#1051) (@lucasbrunozup)
Install & Use
Copyright 2020 ZUP IT SERVICOS EM TECNOLOGIA E INOVACAO SA